So they added another feature to Immunet.
https://www.cisco.com/c/dam/en/us/p.../amp-for-endpoints/white-paper-c11-740980.pdf
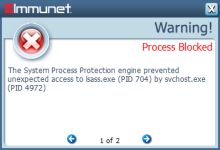
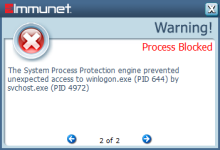
Malicious Activity Protection (MAP) engine included in the AMP Connector Version 6.1.5 for Windows defends your endpoints by monitoring the system and identifying processes that exhibit malicious activities when they execute and stops them from running.
Malicious Activity Protection provides run-time detection and blocking of abnormal behavior of a running program on the endpoint (for example, behaviors associated with ransomware).
The MAP engine is a behavioral-based detection engine that identifies malicious actions that are happening on the endpoint at run time. After extensive research with many variants of ransomware samples observed in the wild, the AMP for Endpoints research and development team has attributed common behaviors associated with such threats to build a rule set that is a part of the engine, residing on the AMP Connector itself.
How it works:
The MAP engine constantly checks for certain changes (explained further) on the protected system to identify the processes that should be convicted when activities outlined in the behavioral rule set are matched. The following actions can be taken on processes detected by MAP, according to the policy configuration: - Log the detection: In this mode, the identified malicious process is not blocked by MAP, but the detection is logged in the AMP for Endpoints console. (This is Audit mode, where no blocking or quarantine action happens, but the detection is logged.) - Block process execution: In this mode, the malicious binary is identified and blocked, and no longer allowed to execute (similar to how the Application Blocking feature works). - Quarantine process: This mode terminates the offending process and places the files into quarantine. The set of detection rules in the MAP engine look for abnormalities on the system. For example, if the process reads, writes, and renames a set of files within a short span of time, then the rule can trigger to take action on that process. Alternatively, if the process reads and writes the content of a file to a different file and then deletes the original files, then the MAP engine can trigger to take action defined in the policy. These are just a couple of examples of rules present in the rule set. Rules are internal for developers and are never exposed to users, as well as not configurable by users. AMP for Endpoints engineering and research teams are continuously assessing techniques used by malware and ransomware in the wild to enhance the anticipated protection levels. To combat false-positive detections, processes that are identified by the MAP engine as exhibiting malicious activity are checked against guardrails to prevent accidental blocking or quarantine of legitimate applications and operating system components.
Works like Kaspersky system watcher? someone needs to start testing Immunet : )