Why is it restricted by default, just curious? That would get in the way of legitimate usage of 7-zip too like scripts that make backups, etc.Hi,
in SecureAplus signed 7z.exe is in the restricted list by default, even its signed. Can i have the POC, so i can test it against SecureAplus?
MacDefender Test #2, "Trojan" Ransomware
- Thread starter MacDefender
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Kaspersky never fails to disappoint even the free version lots of users switching from avast to kaspersky.
Brilliant thread!

If I thought F-Secures stable version would show any other result then the Beta version I could always have a run, but I doubt it in this case simply because of the infection description and also the result. The Ransomware protection bypass I know for example member @Lord Ami even officially reported about last year but no feedback.
Thanks for reporting it back then! I also filed a bug and I agree, FS Protection likely does not perform differently than the stable version of SAFE. Other than UI bugs with the scanner I've never seen DeepGuard and other core modules act differently or worse in the beta.
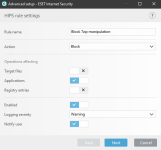
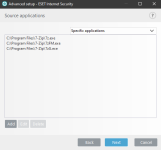
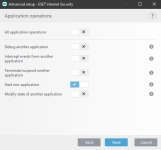
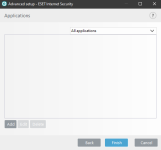
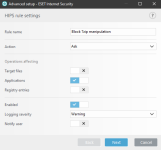
ESET HIPS rules to prevent this kind of manipulation of 7zip, WinRar, WinZip, BandiZip or anything that you may use. Should be useful for ESET users. Thanks for the test and sharing with malware hub tester MacDefender
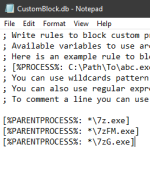
Rules:
1) or
or 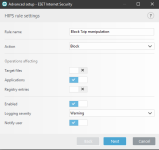
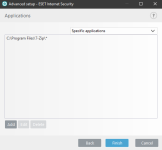
2)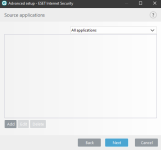 3)
3) 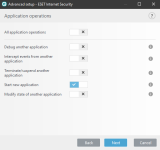 4)
4) 
Result: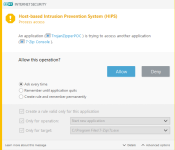 or
or 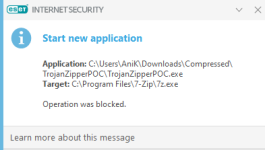
Rules:
1)
 or
or 
2)
 3)
3)  4)
4) 
Result:
 or
or 
ESET HIPS rules to prevent this kind of manipulation of 7zip, WinRar, WinZip, BandiZip or anything that you may use. Should be useful for ESET users. Thanks for the test and sharing with malware hub tester MacDefender
Rules:
1) View attachment 233385 or View attachment 233386
2) View attachment 233387 3) View attachment 233388 4) View attachment 233389
Result: View attachment 233391 or View attachment 233390
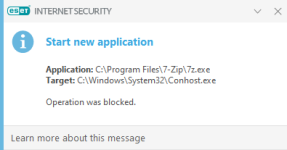
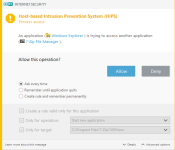
Nice! "Start new application" would be the right choke point for the HIPS.
The ESET HIPS is a very powerful Swiss army knife but it's not set it and forget it. With any of the automatic settings it does almost nothing but the possibilities are endless.
If ESET added a traditional style behavior blocker I would have no complaints about the product!
Oops! About the ESET rule above: I just realized it's going to detect even when you try to open 7zip itself. So not an ideal solution tbhNice! "Start new application" would be the right choke point for the HIPS.
The ESET HIPS is a very powerful Swiss army knife but it's not set it and forget it. With any of the automatic settings it does almost nothing but the possibilities are endless.
If ESET added a traditional style behavior blocker I would have no complaints about the product!
- May 26, 2014
- 1,378
- 9,319
- 2,288
Thanks @MacDefender and @harlan4096 for those tests, you guys are one of the things that makes MalwareTips a great community.
Said that, as I expected Kaspersky System Watcher is smart enough to detect this kind of abuse, but in the case that it "failed", I wonder if the rollback feature could save the files.
Said that, as I expected Kaspersky System Watcher is smart enough to detect this kind of abuse, but in the case that it "failed", I wonder if the rollback feature could save the files.
- May 26, 2014
- 1,378
- 9,319
- 2,288
ESET HIPS rules to prevent this kind of manipulation of 7zip, WinRar, WinZip, BandiZip or anything that you may use. Should be useful for ESET users. Thanks for the test and sharing with malware hub tester MacDefender
Rules:
1) View attachment 233385 or View attachment 233386
2) View attachment 233387 3) View attachment 233388 4) View attachment 233389
Result: View attachment 233391 or View attachment 233390
Those kind of rules are not good enough for protection, what if the "sponsor" (7-Zip for example) isnt launched in from the default files?
The criminals could download the "sponsor" and execute from another place, they could embedded along with the malware, they could execute a different version of the sponsor ...
I already saw some ransomwares that use WinRar/7-Zip and do exactly that, so those kind of rules are not that very useful.
Edit: ROI Locker is the kind of the ransomware that uses this method that I mentioned before:
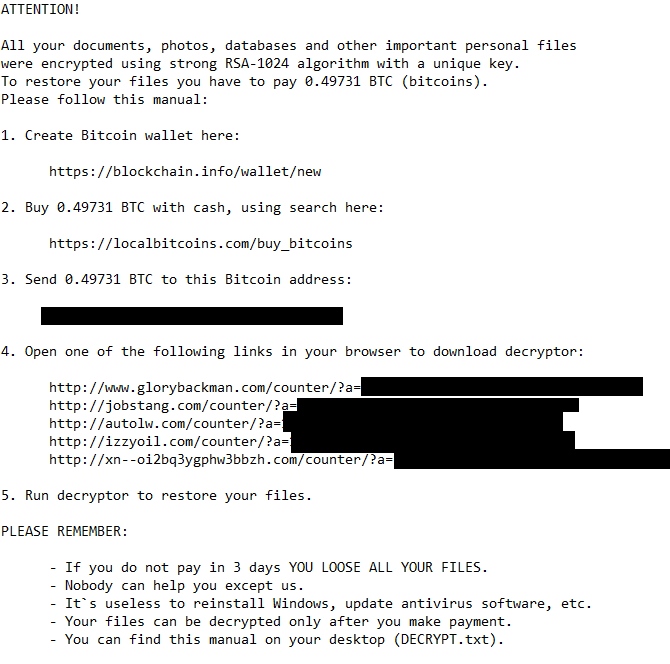
ROI Locker was identified early in April, but appears to have been in circulation as early as March, based on our observation of an advertisement in an underground market. This ransomware is potentially distributed via rogue software websites, based on the fact that this sample was observed sporting the icon of the popular P2P application uTorrent, and is bundled with a uTorrent installer. After ROI Locker is installed, it makes its presence known to the victim in the usual manner with a variation on a lock screen. However, under the hood it operates much differently.
ROI Locker differentiates itself from other ransomware variants mainly in the ransom note screen, as well as the “encryption” mechanism it employs. ROI Locker moves commonly used file-types found on the victim computer into a password-protected RAR archive. Once the files are moved into the RAR archive, ROI Locker spawns an application which contains detailed information for the victim about the infection and the status of their files, as shown in Figure 7. However, due to the way in which this process is carried out, the password to the RAR archive can be found in clear-text in the victim machine’s memory. Additionally, it is important to note that a decrypter has been made publically available for this ransomware, and can be found with additional details at BleepingComputer [5] .
ROI Locker attempts to encrypt the following file types:
.jpg, .jpeg, .png, .gif, .psd, .ppd, .tiff, .flv, .avi, .mov, .qt, .wmv, .rm, .asf, .mp4, .mpg, .mpeg, .m4v, .3gp, .3g2, .pdf, .docx, .pptx, .doc, .7z, .zip, .txt, .ppt, .pps, .wpd, .wps, .xlr, .xls, .xlsl
When executed, ROI Locker will make a copy of itself named “cryptohost.exe” located in the C:\Users\<User>\AppData\Roaming\ directory. Once there, another binary is created and dropped in the same directory called “processor.exe”. This appears to be a version of WinRAR and carries out deletion and addition of identified files to the RAR archive. It should be noted that ROI Locker deletes files after moving them to the RAR archive. Therefore, there is no filename extension for encrypted files associated with this ransomware.
Executed Command via WinRAR C:\Users\[User]\AppData\Roaming\processor.exe A -r -p{SHA-1 Hash of System Info}[User] -m0 -dw C:\Users\[User]\AppData\Roaming\{SHA-1 Hash of System Info}.rar C:\*.jpg C:\*.jpeg C:\*.png C:\*.gif C:\*.psd C:\*.ppd C:\*.tiff C:\*.flv C:\*.avi C:\*.mov C:\*.qt C:\*.wmv C:\*.rm C:\*.asf C:\*.mp4 C:\*.mpg C:\*.mpeg C:\*.m4v C:\*.3gp C:\*.3g2 C:\*.pdf C:\*.docx C:\*.pptx C:\*.doc C:\*.7z C:\*.zip C:\*.txt C:\*.ppt C:\*.pps C:\*.wpd C:\*.wps C:\*.xlr C:\*.xls C:\*.xlsl Switch Function A Create RAR archive -r Recursive search of subfolders -p Set password -m0 Set compression method; 0 indicates file are added with no compression -dw Wipe files after archiving
Ransomware Explosion Continues: CryptFlle2, BrLock and MM Locker Discovered | Proofpoint US
Proofpoint researchers continue to see the regular and rapid emergence of new ransomware strains and variants, validating trends observed since the end of 2015.
Last edited:
Those kind of rules are not good enough for protection, what if the "sponsor" (7-Zip for example) isnt launched in from the default files?
The criminals could download the "sponsor" and execute from another place, they could embedded along with the malware, they could execute a different version of the sponsor ...
I already saw some ransomwares that use WinRar/7-Zip and do exactly that, so those kind of rules are not that very useful.
Edit: ROI Locker is the kind of the ransomware that uses this method that I mentioned before:

Ransomware Explosion Continues: CryptFlle2, BrLock and MM Locker Discovered | Proofpoint US
Proofpoint researchers continue to see the regular and rapid emergence of new ransomware strains and variants, validating trends observed since the end of 2015.www.proofpoint.com
That's pretty cool that there's already ransomware that does this!
I mentioned earlier that this wasn't a very creative idea, I spent just a few minutes looking at various well known executables that could be used to ransom files. The hardest thing to find actually was the ability to delete the original since attempting to do that from a untrusted binary sets off behavior blockers for sure. The other zip/RAR archiver's had stricter licenses and I wanted to respect copyright law. I also quickly looked at Busybox and MinGW and other UNIX like runtimes. Busybox actually had a negative cloud reputation with ESET and Windows Defender so I am guessing malware has tried to use it before. But there's many many other things that can be used to carry out this kind of escape.
By the way, thanks to all the other testers who have been trying this against custom settings. That is a lot of valuable info. It's of course good to know when standard settings don't work, but I also like learning about what tools and techniques are available for those willing to put in that extra effort to configure them. I like making proof of concept exploits because the way they behave can be described in an easy to understand manner and we can just analyze the core mechanics. Real malware tends to be obfuscated, depend heavily in a remote payload stage, and attempts to evade analysis. It takes much longer to whittle them down to the point that you're able to test just a component of the malware.
For example, even in "bonus" dynamic testing, you can see a lot of AVs still simply say "the cloud thinks this is a virus", and that's more or less still signature scanning, not a behavior blocker test.
I agree. But using of 7-Zip and WinRar is not common in the wild since it's easier to decrypt them. As you can see from the report you shared the decryption key can be found in victim's machine's memory so this kind of technique won't be used much.Those kind of rules are not good enough for protection, what if the "sponsor" (7-Zip for example) isnt launched in from the default files?
The criminals could download the "sponsor" and execute from another place, they could embedded along with the malware, they could execute a different version of the sponsor ...
I already saw some ransomwares that use WinRar/7-Zip and do exactly that, so those kind of rules are not that very useful.
Edit: ROI Locker is the kind of the ransomware that uses this method that I mentioned before:

Ransomware Explosion Continues: CryptFlle2, BrLock and MM Locker Discovered | Proofpoint US
Proofpoint researchers continue to see the regular and rapid emergence of new ransomware strains and variants, validating trends observed since the end of 2015.www.proofpoint.com
Anyway, I've managed to create another better HIPS rule to prevent the POC discussed here.
However, due to the way in which this process is carried out, the password to the RAR archive can be found in clear-text in the victim machine’s memory
I agree. But using of 7-Zip and WinRar is not common in the wild since it's easier to decrypt them. As you can see from the report you shared the decryption key can be found in victim's machine's memory so this kind of technique won't be used much.
I agree with that, though I will wager a bet that if everyone had a behavior blocker as good as Emsisoft/DeepGuard/KSW, for a ransomware writer an exposed key is better than no ransomware at all.
In practice that Node.js exploit is more likely what you will see in the wild. Bring along a non AMSI enabled interpreter to do your dirty work for you. A lot of video games include Lua or Python interpreters in their installation. Professional tools like MATLAB and AutoCAD all have scriptable modes. Some game engines are so dumb that they just have an ini file that you can fill with arbitrary commands. I've also noticed that most AVs don't react to things happening within WSL/WSL2, so I'm working on my next exploit pack that uses WSL
I just found the WinRAR example funny more than anything else because creating a password protected archive is just such a lazy way of making ransomware. What's next, open the document in Microsoft Office and script it to turn on password protection?
- May 26, 2014
- 1,378
- 9,319
- 2,288
There are other ransomwares that make the use of a similar technique and not all malware writers will make those foolish mistakes.
Anyway, this is more POC than anything, I dont see a reason to worry about this, but those tests are very interesting because they provide insights about how vendors deal with more exotic and random attack vectors.
While F-Secure DeepGuard isnt the most powerful, I am quite okay with it considering how non-intrusive it is; Emsisoft and Kaspersky behavior blockers (especially the latter) are pretty good too, they always impress me with their technology prowess.

New ransomware variant encrypts files using 7-Zip software - Myce.wiki
The Nemucod ransomware has been found to use the free open source archive software 7-Zip to encrypt files. Nemucod is a pretty common JavaScript malware family distributed through spam emails.
www.myce.com
Anyway, this is more POC than anything, I dont see a reason to worry about this, but those tests are very interesting because they provide insights about how vendors deal with more exotic and random attack vectors.
While F-Secure DeepGuard isnt the most powerful, I am quite okay with it considering how non-intrusive it is; Emsisoft and Kaspersky behavior blockers (especially the latter) are pretty good too, they always impress me with their technology prowess.
Last edited:
We would be waitingI've also noticed that most AVs don't react to things happening within WSL/WSL2, so I'm working on my next exploit pack that uses WSL
As we talked about over in the Emsi vs F-Secure thread (Help Me Decide - Emsisoft vs. Eset Internet Security vs. BitDefender Total Security vs. F-Secure Safe (2020) ), one weakness I've found in F-Secure and other Behavior Blockers is that the most common way to escape the behavior blocker is by using a trusted (but not super well known) process to do your dirty work.
If you use something too popular like Powershell or cmd.exe, behavior blockers are smart, especially thanks to AMSI. However, if you use something just mildly popular like a Node.JS runtime, a copy of Cygwin/MinGW, or in this case, 7-Zip, it seems to be blanket whitelisted by behavior blockers.
This piece of fake "malware", which I'm calling TrojanZipperPOC, does this:
- Find a copy of 7-zip. It prefers "C:\Program Files\7-Zip\7z.exe", as long as you have installed a native copy of 7-zip (e.g. 64-bit on 64-bit Windows). Otherwise it uses a 7z.exe in your current folder, which I've bundled as simply a copy of my 7-zip folder on my development machine. Both copies of 7-zip are official shipping versions which means they're both signed as well as considered high-reputation by cloud lookup.
- Looks for "My Documents\test" (to restrict it from being ACTUAL ransomware), loops through every file in there.
- Runs "7z.exe a -tzip -pransom -sdel FOO.encrypted FOO" for each file you have. This puts it in a zip file with password "ransom" and instructs 7zip to delete the original file.
So far it's worked against both AVs I primarily use. Ouch! I'll spin up additional VMs to test more, but if this is worth testing in the Malware Hub as a special sample, please PM me for the binaries
Antimalware Program Files in My Documents\test Comments Tester ESET NOD32 (all heuristics set to highest, HIPS set to Smart) ENCRYPTED @MacDefender F-Secure SAFE 17.8 Beta ENCRYPTED Ransomware protection is even enabled @MacDefender Symantec Endpoint Protection 14.x (latest) ENCRYPTED @MacDefender Windows Defender Controlled Folder Access intact! CFA blocked anything from happening @MacDefender Emsisoft AM 2020.2 ENCRYPTED @MacDefender
Conclusions:
This is a really really trivial way of commandeering a known process to do your dirty work. It's not hard to trace the fact that 7z.exe was launched directly by an untrusted process, so I consider this to be a solvable vulnerability.
It wouldn't be impossible to distance the untrusted process further from 7z.exe. For example, scheduled tasks or startup items, or using a process to launch a process, etc etc etc. So consider this a dumb "5 minute" approach (that's literally how long it took for me to write this) to replicate a in-the-wild ransomware strategy.
Default Controlled Folder protection is not much of a protection when you realize everything not covered by Controlled Folder protection is allowed to be encrypted. And that can cause problems. But then I suppose the average W10 user would be happy with the fact that it prevented their photos from being encrypted... despite the fact that they should have a backup solution. You know, if one points this sort of stuff out, it strikes a nerve and isn't very popular. Whatever.
To make the best use of the feature one has to skillfully configure it.
Im using F-Secure SAFE with SecureAplus APEX and Comodo Firewall with custom HIPS
The POC uses 7z.exe whic is already on the SAP restricted list by default.
SAP for sure gave a pop-up, signed 7z.exe and universal AV did not detected anything.
The POC uses 7z.exe whic is already on the SAP restricted list by default.
SAP for sure gave a pop-up, signed 7z.exe and universal AV did not detected anything.
There are other ransomwares that make the use of a similar technique and not all malware writers will make those foolish mistakes.

New ransomware variant encrypts files using 7-Zip software - Myce.wiki
The Nemucod ransomware has been found to use the free open source archive software 7-Zip to encrypt files. Nemucod is a pretty common JavaScript malware family distributed through spam emails.www.myce.com
Anyway, this is more POC than anything, I dont see a reason to worry about this, but those tests are very interesting because they provide insights about how vendors deal with more exotic and random attack vectors.
While F-Secure DeepGuard isnt the most powerful, I am quite okay with it considering how non-intrusive it is; Emsisoft and Kaspersky behavior blockers (especially the latter) are pretty good too, they always impress me with their technology prowess.
Yep this totally is just a POC and I am not one for doomsday headlines. It's a way to test behavior blockers which I find interesting.
I definitely agree DeepGuard is a good match to complement F-Secure. The product has anywhere from 3 to 5 engines over time and it's no slouch at signature detection. DeepGuard is just sensitive enough to complement their product and provide zero day protection.
Emsisoft's BB is great too and very sensitive (almost to a fault)
yeah it's both a lot and not a lot. It also stops Blizzard from saving game saves and Turbotax from opening my tax returns..... And yeah everything outside of the protected folders have zero protectionDefault Controlled Folder protection is not much of a protection when you realize everything not covered by Controlled Folder protection is allowed to be encrypted. And that can cause problems. But then I suppose the average W10 user would be happy with the fact that it prevented their photos from being encrypted... despite the fact that they should have a backup solution. You know, if one points this sort of stuff out, it strikes a nerve and isn't very popular. Whatever.
To make the best use of the feature one has to skillfully configure it.
It's a useful tool but not a magical fix for this problem
yeah it's both a lot and not a lot. It also stops Blizzard from saving game saves and Turbotax from opening my tax returns..... And yeah everything outside of the protected folders have zero protection
It's a useful tool but not a magical fix for this problem
Just create and save to your Documents or Downloads folder, then move to whatever protected folder you wish.
It is easy enough. However, I know people and they will complain about having to do a single additional step.
You may also like...
-
App Review Testing Orion Malware Cleaner Designed by Me
- Started by Trident
- Replies: 8
-
AV-TEST ATP Test: How easily Windows can be tricked by malware
- Started by SeriousHoax
- Replies: 45
-
App Review Kaspersky Premium vs McAfee Advanced
- Started by Shadowra
- Replies: 87
-
-