I cant download the file either. I get a russian notification that says "server error" or something like that.
Hot Take Malicious website escaping secure dns
- Thread starter Parkinsond
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
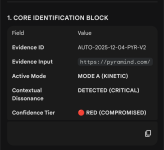
I did not have the guts to try clicking on "update"; just checked if any security vendor or layer could flag the website as malicious, especially I looked like malicious.The update button leads to download a malware that's based on Node.js (the most popular JavaScript runtime environment).
ESET didn't block the malware download source site like Kaspersky, but the main malicious file was detected after extraction.
View attachment 293470
That is true; I typed the web address of the link which is supposed to be lead to after clicking update (from @harlan4096 screenshot); it did not lead anything.How did you manage to download the infected file? I thought the server that's hosting the malicious files was taken down.
I see what the reason was. NextDNS actually blocks the source of the malicious download via Ai and Threat Intelligence Feeds.
Great job, @Trident , as usualDetected by Hawk Eye, just tried.
Nothing more satisfying for a solution engineer than seeing the solution work where many others fail.
View attachment 293471
I did not find the chance to re-check after changing the DOH from AG to NextDNS, especially after finding out all major AV vendors did not flag.I see what the reason was. NextDNS actually blocks the source of the malicious download via Ai and Threat Intelligence Feeds.
Just a quick update
I reopened the malicious link and I managed to download the file. It's a compressed file (installer.57-12-4-71.zip
Anyone willing to test it? Please let me know.
@Trident
I reopened the malicious link and I managed to download the file. It's a compressed file (installer.57-12-4-71.zip
Anyone willing to test it? Please let me know.
@Trident
I am seeing many of these fake updaters lately, there were heuristics built in to the early versions of Orion Malware Cleaner, later on renamed that detected this activity.
The detection was Orion:AppImpersonator
I did not open the zip file and I did not even scan it with BD.I am seeing many of these fake updaters lately, there were heuristics built in to the early versions of Orion Malware Cleaner, later on renamed that detected this activity.
I confirm that BD does not detect the file.
When checked earlier on VT, there was no single detection.I confirm that BD does not detect the file.
I just ran a manual scan.When checked earlier on VT, there was no single detection.
And yes it is not detected by any vendor on VT.
Earlier was not detected by Avast on VT (signature); most probably behavioral detection.Avast wykrywa zagrożenie
Yeah, but Avast when installed has more cards up their sleeve compared to the VT Avast. Furthermore, it is able to track the context.Earlier was not detected by Avast on VT.
It seems BD submission form is broken. I uploaded the .zip file and when I clicked submit, nothing happened.
The plot thickens more and more…It seems BD submission form is broken. I uploaded the .zip file and when I clicked submit, nothing happened.
on VT based on signatures. Other mechanisms intercept the threat
You may also like...
-
Scams & Phishing News Black Cat Behind SEO Poisoning Malware Campaign Targeting Popular Software Searches
- Started by Parkinsond
- Replies: 5
-
Security News eScan confirms update server breached to push malicious update
- Started by andytan
- Replies: 43
-
-
Hot Take Korean malware removal tool I have never heard about before
- Started by Parkinsond
- Replies: 19
-