Article by @Fabian Wosar (Emsisoft):
Software as a service (or SaaS) is a relatively new model of how a lot of software companies are conducting their business today – often to great success. So it comes as no surprise that malware writers and cyber crooks are attempting to adopt this model for their own nefarious purposes. In the past year a whole bunch of these “Ransomware as a Service” campaigns appeared, like for example Tox, Fakben or Radamant. Today we want to spotlight the newest of these campaigns.
Meet Ransom32
At first glance Ransom32 looks like a dime a dozen among many similar malware campaigns. Signups are handled via a hidden server in the Tor network. A simple Bitcoin address where you want the funds generated by your ransomware to be sent to is enough to signup.
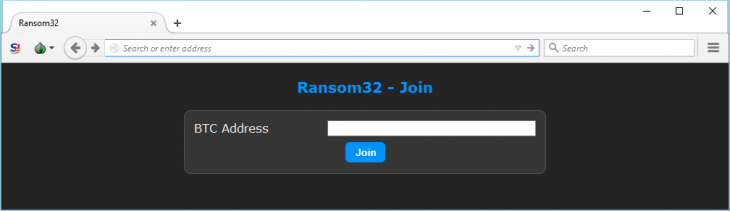
All you need to get your own customized ransomware is a Bitcoin address to send your earnings to
After you type in your Bitcoin address, you will get access to the rudimentary administration panel. In the admin panel, you can get various statistics, like for example how many people already paid or how many systems were infected. You can also configure your “client”, which is their term for the actual malware. It is possible to change the amount of Bitcoins the malware will ask for, as well as configure parameters like fake message boxes the malware is supposed to show during install.
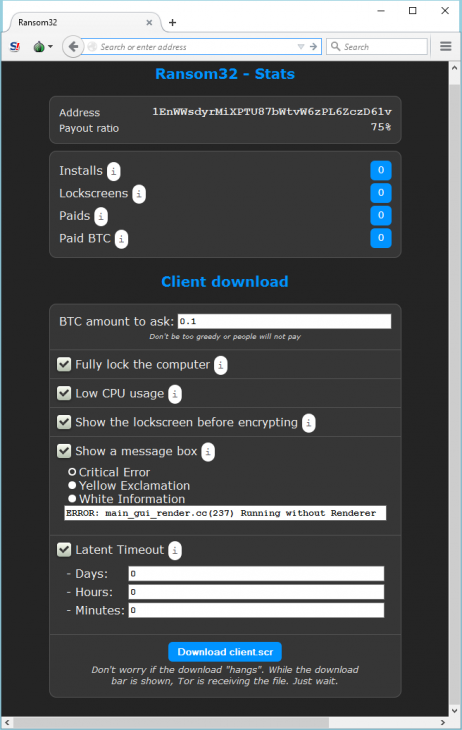
A web interface allows you to see how many systems the malware has infected, how many Bitcoins it earned and allows you to further customize the malware
A click on “Download client.scr” will then generate the malware according to the specifications and will start the download of the more than 22 MB large malware file. At this point it becomes evident that Ransom32 is very different to other ransomware, which rarely exceed 1 MB in size. In fact, most ransomware authors use the small size of their malicious files as some kind of unique selling point when advertising their campaigns in underground hacker communities. Ransom32 definitely had our interest.
Unwrapping the behemoth
After further examination the downloaded file turned out to be a WinRAR self-extracting archive:
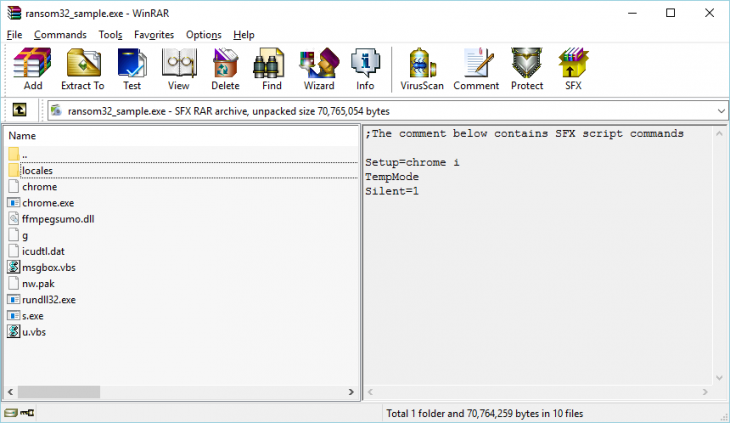
The content of the Ransom32 SFX archive
The malware uses the script language implemented in WinRAR to automatically unpack the content of the archive into the user’s temporary files directory and execute the “chrome.exe” file contained in the archive. The files within the archive have the following purposes:
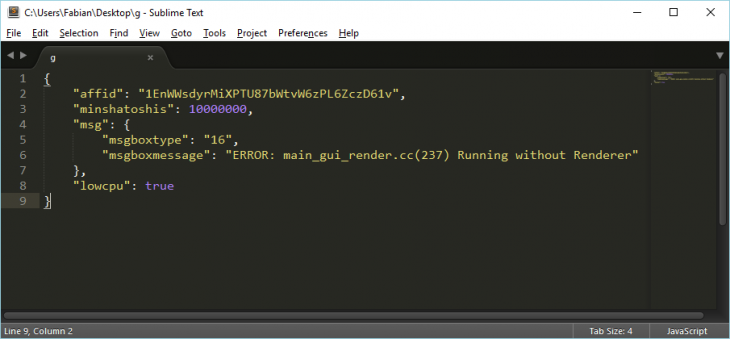
The “g” file contains the malware’s configuration formatted as JSON
The most interesting part by far in that package is the “chrome.exe”. Upon first inspection, “chrome.exe” looks suspiciously like a copy of the actual Chrome browser. Only the lack of a proper digital signature and version information hints that this file is not the actual Chrome browser. Upon further inspection, it turned out that this file is a packaged NW.js application.
Read more: Meet Ransom32: The first JavaScript ransomware
Software as a service (or SaaS) is a relatively new model of how a lot of software companies are conducting their business today – often to great success. So it comes as no surprise that malware writers and cyber crooks are attempting to adopt this model for their own nefarious purposes. In the past year a whole bunch of these “Ransomware as a Service” campaigns appeared, like for example Tox, Fakben or Radamant. Today we want to spotlight the newest of these campaigns.
Meet Ransom32
At first glance Ransom32 looks like a dime a dozen among many similar malware campaigns. Signups are handled via a hidden server in the Tor network. A simple Bitcoin address where you want the funds generated by your ransomware to be sent to is enough to signup.
All you need to get your own customized ransomware is a Bitcoin address to send your earnings to
After you type in your Bitcoin address, you will get access to the rudimentary administration panel. In the admin panel, you can get various statistics, like for example how many people already paid or how many systems were infected. You can also configure your “client”, which is their term for the actual malware. It is possible to change the amount of Bitcoins the malware will ask for, as well as configure parameters like fake message boxes the malware is supposed to show during install.
A web interface allows you to see how many systems the malware has infected, how many Bitcoins it earned and allows you to further customize the malware
A click on “Download client.scr” will then generate the malware according to the specifications and will start the download of the more than 22 MB large malware file. At this point it becomes evident that Ransom32 is very different to other ransomware, which rarely exceed 1 MB in size. In fact, most ransomware authors use the small size of their malicious files as some kind of unique selling point when advertising their campaigns in underground hacker communities. Ransom32 definitely had our interest.
Unwrapping the behemoth
After further examination the downloaded file turned out to be a WinRAR self-extracting archive:
The content of the Ransom32 SFX archive
The malware uses the script language implemented in WinRAR to automatically unpack the content of the archive into the user’s temporary files directory and execute the “chrome.exe” file contained in the archive. The files within the archive have the following purposes:
- “chrome” contains a copy of the GPL license agreement.
- “chrome.exe” is a packaged NW.js application and contains the actual malware code as well as the framework required to run the malware.
- “ffmpegsumo.dll”, “nw.pak”, “icudtl.dat” and “locales” contain data that are required by the NW.jsframework to function properly.
- “rundll32.exe” is a renamed copy of the Tor client.
- “s.exe” is a renamed copy of Optimum X Shortcut, a utility to create and manipulate Desktop and start menu shortcuts.
- “g” contains the malware’s configuration information as configured in the web interface.
- “msgbox.vbs” is a small script that displays a customizable popup message and is used to display the configured message box.
- “u.vbs” is a small script that enumerates, and deletes all files and folders in a given directory.
The “g” file contains the malware’s configuration formatted as JSON
The most interesting part by far in that package is the “chrome.exe”. Upon first inspection, “chrome.exe” looks suspiciously like a copy of the actual Chrome browser. Only the lack of a proper digital signature and version information hints that this file is not the actual Chrome browser. Upon further inspection, it turned out that this file is a packaged NW.js application.
Read more: Meet Ransom32: The first JavaScript ransomware