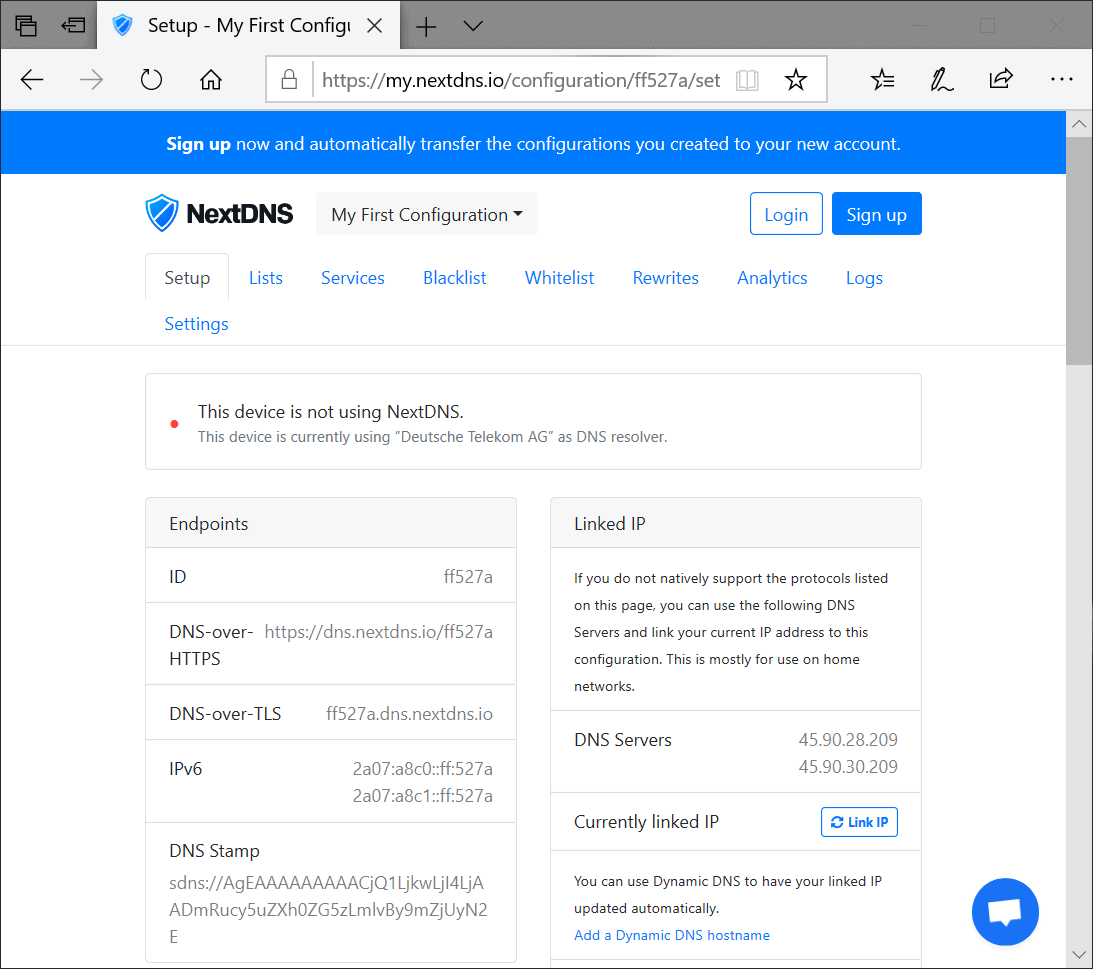
Mozilla announced yesterday that NextDNS has been added to the list of official partners for Firefox's DNS-over-HTTPS feature. NextDNS is a new DNS provider that launched in March 2019 that is "a fully customizable, modern, and secure DNS provider" according to Mozilla.
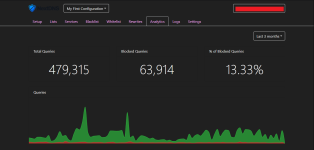
The service is listed as beta currently on the NextDNS website and is completely free during the beta period. NextDNS offers options to enable filtering lists to block known malicious sites, trackers, and other unwanted requests.
The company plans to introduce a paid option after the beta period ends for $1.99 per month for unlimited DNS queries. Free customers are limited to 300,000 DNS queries per month. It is unclear what is going to happen when the limit is reached.
 www.ghacks.net
www.ghacks.net
The service is listed as beta currently on the NextDNS website and is completely free during the beta period. NextDNS offers options to enable filtering lists to block known malicious sites, trackers, and other unwanted requests.
The company plans to introduce a paid option after the beta period ends for $1.99 per month for unlimited DNS queries. Free customers are limited to 300,000 DNS queries per month. It is unclear what is going to happen when the limit is reached.

NextDNS is new Firefox DNS-over HTTPS partner - gHacks Tech News
Mozilla has selected the DNS provider NextDNS as a new partner for its Trusted Recursive Resolvers Program. NextDNS is the second DNS provider (after Cloudflare) that has been accepted into the program.