Has anyone else had a problem with MS Outlook, that the pst. file gets corrupted? I am not sure if this is caused by OSA or by Windows Defender Exploit Guard, and it only happens once in a while.
NoVirusThanks OSArmor
- Thread starter Evjl's Rain
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
D
Deleted member 65228
OSA doesn't intercept the file-system activities. If a process is blocked by it then the block will happen before the process in question can execute any of it's own code.I am not sure if this is caused by OSA or by Windows Defender Exploit Guard
if it's narrowed down to OSA and WDEG only then look at WDEG IMO. Have you set any custom rules?
WDEG does sound like a likely culprit, because it restricts writes to the Documents folder, where Outlook stores the pst files by default.OSA doesn't intercept the file-system activities. If a process is blocked by it then the block will happen before the process in question can execute any of it's own code.
if it's narrowed down to OSA and WDEG only then look at WDEG IMO. Have you set any custom rules?
CORRECTION: It is Protected Folders that restricts writes to the Documents folder, not WDEG as I previously said.
Last edited:
Has anyone else had a problem with MS Outlook, that the pst. file gets corrupted? I am not sure if this is caused by OSA or by Windows Defender Exploit Guard, and it only happens once in a while.
Thanks bro for informing us regarding this issue. Let's hope OSArmor was not the source of MS Outlook issue since MS Outlook issues made me crazy during the last four months.
You can add Outlook to excluded applications in Controlled Folder Access.WDEG does sound like a likely culprit, because it restricts writes to the Documents folder, where Outlook stores the pst files by default.
CORRECTION: It is Protected Folders that restricts writes to the Documents folder, not WDEG as I previously said.
How effective is OSArmor against ransomware attacks without the need of a dedicated anti-ransomware software?
Thanks
Thanks
D
Deleted member 65228
There's not really a ball-mark estimation applicable to this question which is remotely close to being accurate or even half accurate.How effective is OSArmor against ransomware attacks without the need of a dedicated anti-ransomware software?
One monitors process execution whereas the other monitors file-system activity and takes in various other characters into account. One may detect things the other won't and one may trigger more FPs for your specific environment than the other, and it may be completely different for someone else. Depends on your environment, habits/the ransomware sample, specific product/s in question and how they work, version of products being used, among other factors.
OSA and other traditional standalone anti-ransomware utilities can't really be compared because of the huge differences between the internals and design.
But the execution of the ransomware is still a process, no?There's not really a ball-mark estimation applicable to this question which is remotely close to being accurate or even half accurate.
One monitors process execution whereas the other monitors file-system activity and takes in various other characters into account. One may detect things the other won't and one may trigger more FPs for your specific environment than the other, and it may be completely different for someone else. Depends on your environment, habits/the ransomware sample, specific product/s in question and how they work, version of products being used, among other factors.
OSA and other traditional standalone anti-ransomware utilities can't really be compared because of the huge differences between the internals and design.
Quote from opening post
"Monitor and block suspicious processes behaviors to prevent infections by malware, ransomware, and other threats."
The question is how effective OSArmor is against ransomware attacks?
"Monitor and block suspicious processes behaviors to prevent infections by malware, ransomware, and other threats."
The question is how effective OSArmor is against ransomware attacks?
Have not seen anyone report OSA dealing with ransomware here or over in Wilders where it is also being Beta tested. Maybe the NVT author will see this and respond.
I think that @cruelsister's test is probably the best indicator, wouldn't you say? I don't remember the details of her test, but I don't think she would forget ransomware.How effective is OSArmor against ransomware attacks without the need of a dedicated anti-ransomware software?
Thanks
Thanks. Just remembed that video. Re-watch it.I think that @cruelsister's test is probably the best indicator, wouldn't you say? I don't remember the details of her test, but I don't think she would forget ransomware.
So even if all the settings are maxed out OSA still not effective against some ransomware
Yup, it is a companion software, not a complete security solution.Thanks. Just remembed that video. Re-watch it.
So even if all the settings are maxed out OSA still not effective against some ransomware
OSA has improved after that video, @cruelsister executed ransomware on desktop and now OSA can block unsigned processes on desktop.Thanks. Just remembed that video. Re-watch it.
So even if all the settings are maxed out OSA still not effective against some ransomware
That's good, for sure. But the downloads folder is still unprotected.OSA has improved after that video, @cruelsister executed ransomware on desktop and now OSA can block unsigned processes on desktop.
D
Deleted member 65228
You're taking it out of context though.
NoVirusThanks OSArmor prevents execution of processes, it cannot and will not intercept anything else other than process execution. That is it, process execution interception which is handled system-wide via a kernel-mode device driver. Nothing more, nothing less. And it does it brilliantly, whilst demonstrating how effective filtering of process execution can really be when you put your mind to it. The configuration decides if specific processes can be executed or not entirely/with specific command line arguments, that is how the product works.
It does not intercept the file-system activity carried out by processes, the same way it doesn't protect the Master Boot Record. It simply is not designed to behave in this way, it blocks suspicious processes/process execution based on the configuration and it all evolves around blocking process X due to a rule (e.g. prevent execution from folder X) or the command line arguments for a process like bcdedit.exe.
Normal standalone anti-ransomware utilities tend to do things such as monitor how a program is accessing the file-system. For example, has a program just started enumerating through user documents and is now trying to write to such documents? Has the buffer of a document been read into memory, modified, and now the modified buffer is being written back to the file? Is the Master Boot Record being attacked?
If you want to compare this product to a product like RansomOff Anti-Ransomware, CheckMAL's AppCheck Anti-Ransomware, Kaspersky Anti-Ransomware then be my guest but it's completely pointless and makes no sense because it is not remotely close to any of them in terms of how it works. It's like trying to compare pasta to pizza... You might prefer one over the other but at the end of the day it is preference - one might be "better" in terms of "health" but to you as a person the other might be better for "taste" and a year later new research could suggest that the previously-deemed worse one is actually better.
NoVirusThanks OSArmor doesn't prevent a specific type of malware. The configuration provides the ability to block many different types of malware however it depends on forever changing factors such as the configuration being used and the attack in question (how the attack works) and the current circumstances on the environment. If you set the configuration to prevent usage of bcdedit.exe and then a ransomware sample were to mess with bcdedit.exe (highly unlikely but as an example) then this part of the payload would be stopped and this could happen before the encryption procedure - now the sample might not continue further, or it could continue it's payload anyway. Another example would be the location a Trojan Dropper has dropped to - execution of the dropped binary may be prevented due to the configuration regardless of whether it is even malicious or not, but it could have been malicious and could have been anything from a launcher for a rootkit to ransomware or adware.
A configuration with NVT OSArmor may lead to malicious software which went undetected to other products, and vice-versa. There's different factors which simply make it unpredictable. You could say that it is "good" at blocking X but a new day could change all of that because APTs are changing constantly - and the same goes for every other product out there.
It's a good concept, it's a good product, and it will keep improving. Whether it will benefit you at keeping your system safe depends on other mitigations being used as well as the setup configuration for the product (not to mention other factors such as your habits which always stands). It's not "better" than standalone utilities designed to prevent specific malware types and it's neither "worse". It's unpredictable. A new day or a new week could turn the tables of the results.
NoVirusThanks OSArmor prevents execution of processes, it cannot and will not intercept anything else other than process execution. That is it, process execution interception which is handled system-wide via a kernel-mode device driver. Nothing more, nothing less. And it does it brilliantly, whilst demonstrating how effective filtering of process execution can really be when you put your mind to it. The configuration decides if specific processes can be executed or not entirely/with specific command line arguments, that is how the product works.
It does not intercept the file-system activity carried out by processes, the same way it doesn't protect the Master Boot Record. It simply is not designed to behave in this way, it blocks suspicious processes/process execution based on the configuration and it all evolves around blocking process X due to a rule (e.g. prevent execution from folder X) or the command line arguments for a process like bcdedit.exe.
Normal standalone anti-ransomware utilities tend to do things such as monitor how a program is accessing the file-system. For example, has a program just started enumerating through user documents and is now trying to write to such documents? Has the buffer of a document been read into memory, modified, and now the modified buffer is being written back to the file? Is the Master Boot Record being attacked?
If you want to compare this product to a product like RansomOff Anti-Ransomware, CheckMAL's AppCheck Anti-Ransomware, Kaspersky Anti-Ransomware then be my guest but it's completely pointless and makes no sense because it is not remotely close to any of them in terms of how it works. It's like trying to compare pasta to pizza... You might prefer one over the other but at the end of the day it is preference - one might be "better" in terms of "health" but to you as a person the other might be better for "taste" and a year later new research could suggest that the previously-deemed worse one is actually better.
NoVirusThanks OSArmor doesn't prevent a specific type of malware. The configuration provides the ability to block many different types of malware however it depends on forever changing factors such as the configuration being used and the attack in question (how the attack works) and the current circumstances on the environment. If you set the configuration to prevent usage of bcdedit.exe and then a ransomware sample were to mess with bcdedit.exe (highly unlikely but as an example) then this part of the payload would be stopped and this could happen before the encryption procedure - now the sample might not continue further, or it could continue it's payload anyway. Another example would be the location a Trojan Dropper has dropped to - execution of the dropped binary may be prevented due to the configuration regardless of whether it is even malicious or not, but it could have been malicious and could have been anything from a launcher for a rootkit to ransomware or adware.
A configuration with NVT OSArmor may lead to malicious software which went undetected to other products, and vice-versa. There's different factors which simply make it unpredictable. You could say that it is "good" at blocking X but a new day could change all of that because APTs are changing constantly - and the same goes for every other product out there.
It's a good concept, it's a good product, and it will keep improving. Whether it will benefit you at keeping your system safe depends on other mitigations being used as well as the setup configuration for the product (not to mention other factors such as your habits which always stands). It's not "better" than standalone utilities designed to prevent specific malware types and it's neither "worse". It's unpredictable. A new day or a new week could turn the tables of the results.
Evjl's Rain
Level 47
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
- Apr 18, 2016
- 3,676
- 28,872
- 4,599
I received this message when trying to run chrome portable from portableapps -> blocked -> disabled OSA manually -> ran the file, installation completed -> enabled OSA -> run chromeportable -> blocked
why is it classified as SuspiciousProcesses?
why is it classified as SuspiciousProcesses?
Date/Time: 1/24/2018 7:07:45 PM
Process: [3068]C:\Users\evjlsrain\Desktop\GoogleChromePortable_63.0.3239.132_online.paf.exe
Parent: [4244]C:\Windows\explorer.exe
Rule: BlockSuspiciousProcesses
Rule Name: Block execution of suspicious processes
Command Line: "C:\Users\evjlsrain\Desktop\GoogleChromePortable_63.0.3239.132_online.paf.exe"
Signer: Rare Ideas, LLC
Parent Signer: Microsoft Windows
Date/Time: 1/24/2018 7:10:51 PM
Process: [5792]E:\GoogleChromePortable\GoogleChromePortable.exe
Parent: [7860]E:\sandboxie\Start.exe
Rule: BlockSuspiciousProcesses
Rule Name: Block execution of suspicious processes
Command Line: "E:\GoogleChromePortable\GoogleChromePortable.exe"
Signer: Rare Ideas, LLC
Parent Signer:
Process: [3068]C:\Users\evjlsrain\Desktop\GoogleChromePortable_63.0.3239.132_online.paf.exe
Parent: [4244]C:\Windows\explorer.exe
Rule: BlockSuspiciousProcesses
Rule Name: Block execution of suspicious processes
Command Line: "C:\Users\evjlsrain\Desktop\GoogleChromePortable_63.0.3239.132_online.paf.exe"
Signer: Rare Ideas, LLC
Parent Signer: Microsoft Windows
Date/Time: 1/24/2018 7:10:51 PM
Process: [5792]E:\GoogleChromePortable\GoogleChromePortable.exe
Parent: [7860]E:\sandboxie\Start.exe
Rule: BlockSuspiciousProcesses
Rule Name: Block execution of suspicious processes
Command Line: "E:\GoogleChromePortable\GoogleChromePortable.exe"
Signer: Rare Ideas, LLC
Parent Signer:
D
Deleted member 65228
It should work fine.Does OS armor work with Windows Server 2016?
Here is a new v1.4 (pre-release) (test27):
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test27.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved support for Fast User Switching and Logouts
+ Many internal improvements
+ Integrated a smart caching mechanism
+ Prevent flooding of the notification dialog
+ Fixed opening of the Configurator in certain situations
+ Fixed some false positives
+ Block execution of unsigned processes on Downloads folder
+ Added Tor Brower, Comodo Dragon and MSPub on Anti-Exploit tab
+ Block execution of Sysprep.exe (UAC Bypass)
+ The alert icon on Configurator is red for some options
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install test 27
Thanks to the new caching mechanism, CPU usage should be lower now when executing many processes. All issues related to "timeout 30000 on the service", "Configurator doesn't show up", "when switching users icon is not present", etc should also be fixed.
@Evjl's Rain
FP is fixed now.
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test27.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved support for Fast User Switching and Logouts
+ Many internal improvements
+ Integrated a smart caching mechanism
+ Prevent flooding of the notification dialog
+ Fixed opening of the Configurator in certain situations
+ Fixed some false positives
+ Block execution of unsigned processes on Downloads folder
+ Added Tor Brower, Comodo Dragon and MSPub on Anti-Exploit tab
+ Block execution of Sysprep.exe (UAC Bypass)
+ The alert icon on Configurator is red for some options
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install test 27
Thanks to the new caching mechanism, CPU usage should be lower now when executing many processes. All issues related to "timeout 30000 on the service", "Configurator doesn't show up", "when switching users icon is not present", etc should also be fixed.
@Evjl's Rain
FP is fixed now.
Evjl's Rain
Level 47
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
- Apr 18, 2016
- 3,676
- 28,872
- 4,599
@NoVirusThanks hello, conflict with avast hasn't still been fixed yet in test 27. Avast still makes OSA not functioning. I ticked block cmd and execute cmd to test it
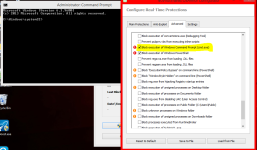

Last edited:
You may also like...
-
On Sale! Avast Premium Security 1 Device 1 Year 9.99€
- Started by Brownie2019
- Replies: 0
-
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
Privacy News Windows 11 24H2/25H2 Flaw Keeps Task Manager Running After You Close It
- Started by Brownie2019
- Replies: 5