P
plat1098
No Windows Defender notification with version 42 here either. This version 42 cured the problem of the disabling of the NVTOSArmor service at startup--no issues over multiple startups and restarts. Perfect! 

WD can recognize files as dangerous depending on Defender configuration. @Av Gurus has very aggressive Defender settings, so Defender AI is more sensitive to the potential threats.No Windows Defender notification with version 42 here either. This version 42 cured the problem of the disabling of the NVTOSArmor service at startup--no issues over multiple startups and restarts. Perfect!
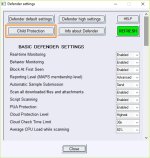
You can try ConfigureDefender tool:OK, I see. What aggressive Windows Defender settings would provoke this detection? Here is W10 Home with Smart Screen all set to "block," Cloud Protection, PUA in registry and all default Exploit Guards enabled. Only Controlled Folder Access is "off" because it's a pain. Would additional, more aggressive settings only be attainable by using a third party configurator? Edit: I have NVTSysHardener, for example, with some extra settings enabled, but there is also your application Hard_Configurator, right?
You can try ConfigureDefender tool:
ConfigureDefender utility for Windows 10
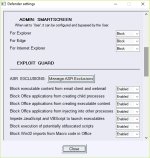
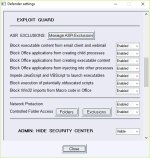
Those options would be welcome especially on the admin account."Block new and unknown UAC-bypass attempts (experimental)"
...
"Block known system processes used for UAC-bypass"
...
"Block ALL "autoelevate" system processes"
...
By experience can endorse that. Risky commands block for Basic User does not seem to cause Windows Update problemsThose options would be welcome especially on the admin account.
But, it would be much better to block processes executed as standard user and do not block processes executed with higher rights. The malware trying to bypass UAC is executed as standard user. When it is executed
emdorse thatwith administrative rights the UAC has been already bypassed. Furthermore, blocking processes executed with administrative rights can break system tasks and give many false positives.
I block 57 system processes in this way using SRP (configured by Hard_Configurator) and hardly can see any alert even when making Windows updates and upgrades to the higher Windows version.
Sometimes the same command line will get blocked by several different rules, and will need to be whitelisted for each rule separately.exclusions are ignored when "Block execution of suspicious executables"
I have added blocked executable to exclusion list and it keeps being blocked.
it's a simple exe execution from a usb drive, same block message.Sometimes the same command line will get blocked by several different rules, and will need to be whitelisted for each rule separately.
For instance, if cmd calls netsh, it will need an allow rule for cmd and another allow rule for netsh.
I am just guessing, but maybe the USB got a different drive letter the second time, so that the path changed?it's a simple exe execution from a usb drive, same block message.
nope, haven't unplugged the USB between tests, It just got blocked, I added it to exclusions, tried again, blocked again.I am just guessing, but maybe the USB got a different drive letter the second time, so that the path changed?