So this is safe for general use on windows 10 home computer with defaults? Thks
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Wow what a great resource for Window's 10, I have to admit I was pretty sick of manually doing all these edit's on individual Window machines, and was too lazy to make a script. Glad to see someone took the time out to code something awesome, that will save many sysadmin's time in configuration.
While I am fairly comfortable manually doing it, I would mainly use these for client's who aren't too tech savvy, and who work in financials. So, security is important to them, or at least when it come's to their financials lol. Would me setting this up on their machine once be good enough, with a periodic monthly check in on the software, to see if anything need's to be changed. Keep them fairly protected from harming their machine's themselves?
Or, should I continue doing it the manual way?
Best,
Davi
While I am fairly comfortable manually doing it, I would mainly use these for client's who aren't too tech savvy, and who work in financials. So, security is important to them, or at least when it come's to their financials lol. Would me setting this up on their machine once be good enough, with a periodic monthly check in on the software, to see if anything need's to be changed. Keep them fairly protected from harming their machine's themselves?
Or, should I continue doing it the manual way?
Best,
Davi
@NoVirusThanks
Any thought about joining SysHardener with OsArmor? Reason being both programs perform hardening of OS and System, would be nice to install One program for a "perfect hardening solution" and save on Windows boot time with less programs...SysHardener, OsArmor, ERP, Registry Guard. Just Thinking, mabie SysArmor? Thanks Again!
Any thought about joining SysHardener with OsArmor? Reason being both programs perform hardening of OS and System, would be nice to install One program for a "perfect hardening solution" and save on Windows boot time with less programs...SysHardener, OsArmor, ERP, Registry Guard. Just Thinking, mabie SysArmor? Thanks Again!
Can you use a local account as indicated here?
Windows 10 telemetry - Open up, Sesame
"For instance, Cortana does not work with the local account"
Thanks for the assist, good website too. I was only being half serious in that post as I've read how intertwined Cortana has become unfortunately but this NVT gang seem to be pretty slick, ambitious at a minimum so you never know.
F
ForgottenSeer 58943
Thread author
How about disabling CPD Services on Windows and disabling their re-initialization? (Connected Devices Platform Service)
sc config CDPUserSvc start= disabled
sc config CDPSvc start= disabled
reg add "HKLM\System\CurrentControlSet\Services\PimIndexMaintenanceSvc" /v "Start" /t REG_DWORD /d "4" /f
reg add "HKLM\System\CurrentControlSet\Services\UserDataSvc" /v "Start" /t REG_DWORD /d "4" /f
reg add "HKLM\System\CurrentControlSet\Services\UnistoreSvc" /v "Start" /t REG_DWORD /d "4" /f
They basically assign a UID to each person, then use this to send data to other apps (and to spy). I've found no negative side effects to disabling it in almost a year but all privacy tools seem to miss it.
sc config CDPUserSvc start= disabled
sc config CDPSvc start= disabled
reg add "HKLM\System\CurrentControlSet\Services\PimIndexMaintenanceSvc" /v "Start" /t REG_DWORD /d "4" /f
reg add "HKLM\System\CurrentControlSet\Services\UserDataSvc" /v "Start" /t REG_DWORD /d "4" /f
reg add "HKLM\System\CurrentControlSet\Services\UnistoreSvc" /v "Start" /t REG_DWORD /d "4" /f
They basically assign a UID to each person, then use this to send data to other apps (and to spy). I've found no negative side effects to disabling it in almost a year but all privacy tools seem to miss it.
@ForgottenSeer 58943
How about disabling CPD Services on Windows and disabling their re-initialization? (Connected Devices Platform Service)
sc config CDPUserSvc start= disabled
sc config CDPSvc start= disabled
reg add "HKLM\System\CurrentControlSet\Services\PimIndexMaintenanceSvc" /v "Start" /t REG_DWORD /d "4" /f
reg add "HKLM\System\CurrentControlSet\Services\UserDataSvc" /v "Start" /t REG_DWORD /d "4" /f
reg add "HKLM\System\CurrentControlSet\Services\UnistoreSvc" /v "Start" /t REG_DWORD /d "4" /f
They basically assign a UID to each person, then use this to send data to other apps (and to spy). I've found no negative side effects to disabling it in almost a year but all privacy tools seem to miss it.
Are these settings Windoze 10 only or will they work on Windoze 7 64bit?
How about disabling CPD Services on Windows and disabling their re-initialization? (Connected Devices Platform Service)
sc config CDPUserSvc start= disabled
sc config CDPSvc start= disabled
reg add "HKLM\System\CurrentControlSet\Services\PimIndexMaintenanceSvc" /v "Start" /t REG_DWORD /d "4" /f
reg add "HKLM\System\CurrentControlSet\Services\UserDataSvc" /v "Start" /t REG_DWORD /d "4" /f
reg add "HKLM\System\CurrentControlSet\Services\UnistoreSvc" /v "Start" /t REG_DWORD /d "4" /f
They basically assign a UID to each person, then use this to send data to other apps (and to spy). I've found no negative side effects to disabling it in almost a year but all privacy tools seem to miss it.
Are these settings Windoze 10 only or will they work on Windoze 7 64bit?
F
ForgottenSeer 58943
Thread author
Also, I'd recommend putting in the option for disabling the security risk known as DNSClient.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache
(set START to 4, then: sc config Dnscache start= disabled)
Maybe even removing the stupid 3DObjects folder on File Explorer. Not a security risk but a huge annoyance.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MyComputer\NameSpace
Locate and delete
{0DB7E03F-FC29-4DC6-9020-FF41B59E513A}
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Explorer\MyComputer\NameSpace
Locate and delete
{0DB7E03F-FC29-4DC6-9020-FF41B59E513A}
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache
(set START to 4, then: sc config Dnscache start= disabled)
Maybe even removing the stupid 3DObjects folder on File Explorer. Not a security risk but a huge annoyance.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MyComputer\NameSpace
Locate and delete
{0DB7E03F-FC29-4DC6-9020-FF41B59E513A}
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Explorer\MyComputer\NameSpace
Locate and delete
{0DB7E03F-FC29-4DC6-9020-FF41B59E513A}
Have added an option to change the PowerShell Execution Policy on current user (unchecked by default):
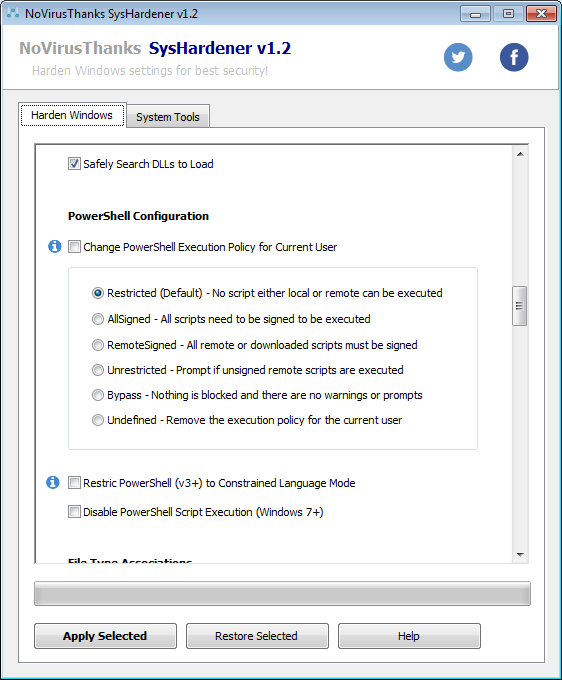
I've added also possibility to change it to Unrestricted\Bypass\Undefined.
What do you think about it? Better to allow the user to change it with all available options or just have a single checkbox:
Set PowerShell Execution Policy to Restricted for Current User
The "Restricted" is the default option (and more secure), more info here:
Set-ExecutionPolicy (Microsoft.PowerShell.Security)
Will add also 3 new options to disable these other Windows services (unchecked by default):
Turn Off HomeGroup Provider Service
Turn Off Program Compatibility Assistant (PCA) Service
Turn Off Windows Search Service
What do you think?
@Daviworld
You may want to apply SysHardener tweaks once and it should be fine.
In case Windows auto-upgrades to a major version, it may happen that it changes some tweaks made by SysHardener (i.e disabled services).
So you'll need to re-apply SysHardener tweaks.
@blueblackwow65
Yes, with default settings it should be fine and not cause issues.
@Darrin
We'll need to discuss about it (not a priority for now).
@ForgottenSeer 58943
About disabling DNSClient, can add it as disabled by default.
* I've read somewhere that if disabled, it may create issues with some firewall software (don't remember the link).
About UserDataSvc\UnistoreSvc, will check them later.
I've added also possibility to change it to Unrestricted\Bypass\Undefined.
What do you think about it? Better to allow the user to change it with all available options or just have a single checkbox:
Set PowerShell Execution Policy to Restricted for Current User
The "Restricted" is the default option (and more secure), more info here:
Set-ExecutionPolicy (Microsoft.PowerShell.Security)
Will add also 3 new options to disable these other Windows services (unchecked by default):
Turn Off HomeGroup Provider Service
Turn Off Program Compatibility Assistant (PCA) Service
Turn Off Windows Search Service
What do you think?
@Daviworld
You may want to apply SysHardener tweaks once and it should be fine.
In case Windows auto-upgrades to a major version, it may happen that it changes some tweaks made by SysHardener (i.e disabled services).
So you'll need to re-apply SysHardener tweaks.
@blueblackwow65
Yes, with default settings it should be fine and not cause issues.
@Darrin
We'll need to discuss about it (not a priority for now).
@ForgottenSeer 58943
About disabling DNSClient, can add it as disabled by default.
* I've read somewhere that if disabled, it may create issues with some firewall software (don't remember the link).
About UserDataSvc\UnistoreSvc, will check them later.
F
ForgottenSeer 58943
Thread author
@ForgottenSeer 58943
About disabling DNSClient, can add it as disabled by default.
* I've read somewhere that if disabled, it may create issues with some firewall software (don't remember the link).
About UserDataSvc\UnistoreSvc, will check them later.
I am unaware of any product requiring DNSClient, especially on Windows 10 because Windows 10 defaults to Multi-Homed DNS (which you should add an option to disable that as well, as this can faciliate DNS hijacking by a quantum sourced DNS lookup injecting itself as a fast response hijacking DNS). SO you are probably safe at the very least, providing the option, but default should work for virtually everyone just fine.
There is one product that I know of called Windows Firewall Control made by binisoft that requires DNS Client Service; As per Binisoft site...
Windows Firewall Control
System Requirements
√ Microsoft .NET Framework version 4.5 or a newer version.
√ Compatible with all x86 and x64 versions of Windows 10, 8.1, 8, 7, Server 2016, Server 2012.
√ Windows Firewall service is required to be enabled for Windows Firewall Control to run.
√ DNS Client service is required to be enabled for the notifications to work properly.
Windows Firewall Control
System Requirements
√ Microsoft .NET Framework version 4.5 or a newer version.
√ Compatible with all x86 and x64 versions of Windows 10, 8.1, 8, 7, Server 2016, Server 2012.
√ Windows Firewall service is required to be enabled for Windows Firewall Control to run.
√ DNS Client service is required to be enabled for the notifications to work properly.
F
ForgottenSeer 58943
Thread author
There is one product that I know of called Windows Firewall Control made by binisoft that requires DNS Client Service; As per Binisoft site...
Windows Firewall Control
System Requirements
√ Microsoft .NET Framework version 4.5 or a newer version.
√ Compatible with all x86 and x64 versions of Windows 10, 8.1, 8, 7, Server 2016, Server 2012.
√ Windows Firewall service is required to be enabled for Windows Firewall Control to run.
√ DNS Client service is required to be enabled for the notifications to work properly.
Required for notifications, so they're sourcing DNSClient for notifications of DNS activity, essentially using it as a text file to push notifications. Not really a proper use of DNSClient, and the first I have heard of it being required. The negatives far outweigh the benefits of DNSClient, it's also an awesome tool to use for malware to spy, steal your website activity and redirect your DNS.
Released a new version SysHardener v1.2:
Harden Windows Settings with SysHardener | NoVirusThanks
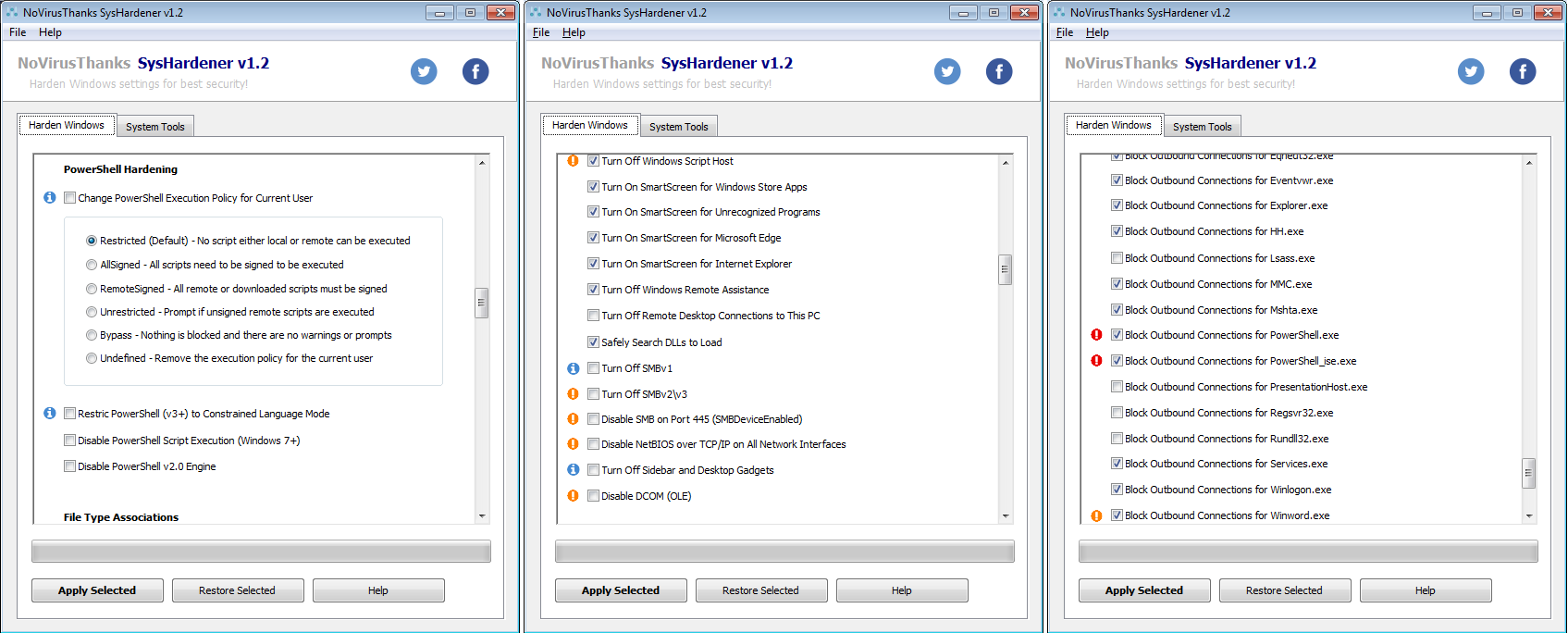
This is the changelog:
+ Fixed disabling of WinHTTP Web Proxy Auto-Discovery Service
+ Fixed enabling of PowerShell Constrained Language Mode
+ Fixed disabling of PowerShell Script Execution
+ Added button "Windows Features" on "System Tools" tab
+ Added button "Active Connections" on "System Tools" tab
+ Added button "Event Viewer" on "System Tools" tab
+ Added button "DCOMCNFG" on "System Tools" tab
+ New option "Turn Off HomeGroup Provider Service"
+ New option "Turn Off Program Compatibility Assistant Service"
+ New option "Change PowerShell Execution Policy for Current User"
+ New option "Turn Off DNS Client (Dnscache) Service"
+ New option "Turn Off Windows Search Service"
+ New option "Turn Off SMBv1"
+ New option "Turn Off SMBv2\v3"
+ New option "Disable SMB on Port 445 (SMBDeviceEnabled)"
+ New option "Disable NetBIOS over TCP/IP on All Network Interfaces"
+ New option "Turn Off Sidebar and Desktop Gadgets"
+ New option "Disable DCOM (OLE)"
+ New option "Turn Off Server (LanmanServer) Service"
+ New option "Block Oubound Connections for Eventvwr.exe"
+ New option "Block Oubound Connections for MMC.exe"
+ New option "Block Oubound Connections for Wmic.exe"
+ New option "Disable PowerShell v2.0 Engine"
+ New option "Block Outbound Connections for Rundll32.exe"
+ New option "Block Outbound Connections for PresentationHost.exe"
+ Disabled by default some Windows Firewall options
+ Added top-menu (File\Help) to the main window
+ Minor fixes and optimizations
+ Updated help file
Harden Windows Settings with SysHardener | NoVirusThanks
This is the changelog:
+ Fixed disabling of WinHTTP Web Proxy Auto-Discovery Service
+ Fixed enabling of PowerShell Constrained Language Mode
+ Fixed disabling of PowerShell Script Execution
+ Added button "Windows Features" on "System Tools" tab
+ Added button "Active Connections" on "System Tools" tab
+ Added button "Event Viewer" on "System Tools" tab
+ Added button "DCOMCNFG" on "System Tools" tab
+ New option "Turn Off HomeGroup Provider Service"
+ New option "Turn Off Program Compatibility Assistant Service"
+ New option "Change PowerShell Execution Policy for Current User"
+ New option "Turn Off DNS Client (Dnscache) Service"
+ New option "Turn Off Windows Search Service"
+ New option "Turn Off SMBv1"
+ New option "Turn Off SMBv2\v3"
+ New option "Disable SMB on Port 445 (SMBDeviceEnabled)"
+ New option "Disable NetBIOS over TCP/IP on All Network Interfaces"
+ New option "Turn Off Sidebar and Desktop Gadgets"
+ New option "Disable DCOM (OLE)"
+ New option "Turn Off Server (LanmanServer) Service"
+ New option "Block Oubound Connections for Eventvwr.exe"
+ New option "Block Oubound Connections for MMC.exe"
+ New option "Block Oubound Connections for Wmic.exe"
+ New option "Disable PowerShell v2.0 Engine"
+ New option "Block Outbound Connections for Rundll32.exe"
+ New option "Block Outbound Connections for PresentationHost.exe"
+ Disabled by default some Windows Firewall options
+ Added top-menu (File\Help) to the main window
+ Minor fixes and optimizations
+ Updated help file
"+ Disabled by default some Windows Firewall options"
Can you tell us which ones? I am using Windows Firewall Control and wonder what the effect will be. TY
Can you tell us which ones? I am using Windows Firewall Control and wonder what the effect will be. TY
These Windows Firewall rules are disabled (unchecked) by default:
Block Outbound Connections for Bitsadmin.exe
Block Outbound Connections for Csrss.exe
Block Outbound Connections for DeviceDisplayObjectProvider.exe
Block Outbound Connections for Lsass.exe
Block Outbound Connections for PresentationHost.exe
Block Outbound Connections for Regsvr32.exe
Block Outbound Connections for Rundll32.exe
Block Outbound Connections for Wsmprovhost.exe
Block Outbound Connections for Bitsadmin.exe
Block Outbound Connections for Csrss.exe
Block Outbound Connections for DeviceDisplayObjectProvider.exe
Block Outbound Connections for Lsass.exe
Block Outbound Connections for PresentationHost.exe
Block Outbound Connections for Regsvr32.exe
Block Outbound Connections for Rundll32.exe
Block Outbound Connections for Wsmprovhost.exe
P
plat1098
Thread author
This error in Event Viewer--see below--persists after SysHardener is uninstalled and machine is restarted. This corresponds to the setting 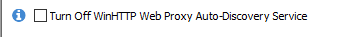 which I believe is enabled by default. Shouldn't this setting revert to its original state when SysHardener is removed?
which I believe is enabled by default. Shouldn't this setting revert to its original state when SysHardener is removed?
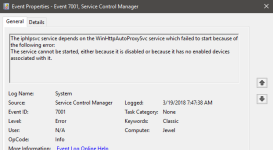
Edit: The checkbox for the WinHTTPAutoProxySvc is cleared and machine is restarted but the above error in Event Viewer persists. I searched for methods to get rid of the error and results yielded things like running a batch file but would rather wait for further info.

Edit: The checkbox for the WinHTTPAutoProxySvc is cleared and machine is restarted but the above error in Event Viewer persists. I searched for methods to get rid of the error and results yielded things like running a batch file but would rather wait for further info.
Last edited by a moderator:
P
plat1098
Thread author
@upnorth : Windows 10 latest--16299.309. Not installed on my alternate workstation at the moment. The setting in SysHardener seems to be irreversible on here unless you know how to manually re-enable the service or you reset the machine entirely. 
Edit: Since I can restore from an older image, I'm going to clarify my above issue. Seeing this WinHTTPAutoProxy setting is enabled when SysHardener is first installed, could it instead be default-disabled, with the user choosing to enable it instead? You're stuck with the irreversible setting otherwise, it seems. @NoVirusThanks?
Edit: Since I can restore from an older image, I'm going to clarify my above issue. Seeing this WinHTTPAutoProxy setting is enabled when SysHardener is first installed, could it instead be default-disabled, with the user choosing to enable it instead? You're stuck with the irreversible setting otherwise, it seems. @NoVirusThanks?
Last edited by a moderator:
You may also like...
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
Serious Discussion Orion Malware Cleaner (OMC) - By Trident
- Started by Trident
- Replies: 23
-
App Review Testing Orion Malware Cleaner Designed by Me
- Started by Trident
- Replies: 8