CoolNo problem!
I'll post my firewall rules later today...
Basic Security ParaXY's Windows 10 desktop Config
- Thread starter ParaXY
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Cool
As promised, here are the incoming rules:
And outgoing rules:
To get to this point I started by deleting ALL the default rules after I reinstalling Windows. I then use WFC to stop apps auto creating rules on their own (ie: without my consent).
8
I will do the same as you when I can get WFC to work properly on the latest Insider build. The author is hopefully going to look at solution in a few days.
Thank again
Thanks for sharing your firewall rules. I like the idea of starting from scratch and then creating only the rules that are absolutely necessary.As promised, here are the incoming rules:
View attachment 147986
And outgoing rules:
View attachment 147987
To get to this point I started by deleting ALL the default rules after I reinstalling Windows. I then use WFC to stop apps auto creating rules on their own (ie: without my consent).
I will do the same as you when I can get WFC to work properly on the latest Insider build. The author is hopefully going to look at solution in a few days.
Thank again
No problem!
It took me aaaaages to get my AppLocker and Windows Firewall Rules to this stage. In fact the entire WIndows reinstall took me about a week or so to complete but that also included formatting all my data drives for ReFS and 256bit AES encryption for Bitlocker.
I've been researching this for months and I think all the effort has paid off as this build/install/configuration is a pleasure to use so far. ;-)
It took me aaaaages to get my AppLocker and Windows Firewall Rules to this stage. In fact the entire WIndows reinstall took me about a week or so to complete but that also included formatting all my data drives for ReFS and 256bit AES encryption for Bitlocker.
I've been researching this for months and I think all the effort has paid off as this build/install/configuration is a pleasure to use so far. ;-)
D
Deleted member 178
Yes , me too just cutomizing my WF took me a day (research + implementation) .It took me aaaaages to get my AppLocker and Windows Firewall Rules to this stage. I've been researching this for months and I think all the effort has paid off as this build/install/configuration is a pleasure to use so far. ;-)
me 3 bros. i downloaded WFC and set to medium filtering which blocked almost everything then allowed programs/processes as i needed them. and when i wasnt sure, i just googled them to find out if they were safe or not
I'm really pleased with WFC. It's the only third party security software I have installed on the machine so far. It's a fantastic front end to the built in Windows Firewall. I really like the connection log, it makes troubleshooting MUCH easier than reading the firewall log in notepad!
So I've made some changes to my AppLocker Microsoft exception Publisher Rules. I have now added the following so that they cannot run:
One thing that's worth doing is disabling Ease of access in Windows as this is such a security hole:
To disable Ease of access on login screen:
Change ownership of c:\windows\system32\utilman.exe to Administrators
cacls c:\windows\system32\utilman.exe /C /D Everyone
cacls c:\windows\syswow64\utilman.exe /C /D Everyone
The next thing I am considering for my secure build is to block/restrict removable devices/drives use Local Group Policy. More on that a bit later ;-)
So I've made some changes to my AppLocker Microsoft exception Publisher Rules. I have now added the following so that they cannot run:
- odbcconf.exe
- sdbinst.exe
One thing that's worth doing is disabling Ease of access in Windows as this is such a security hole:
To disable Ease of access on login screen:
Change ownership of c:\windows\system32\utilman.exe to Administrators
cacls c:\windows\system32\utilman.exe /C /D Everyone
cacls c:\windows\syswow64\utilman.exe /C /D Everyone
The next thing I am considering for my secure build is to block/restrict removable devices/drives use Local Group Policy. More on that a bit later ;-)
I'm a big fan of WFC too. Just waiting for a fix for running on the latest Insider buildI'm really pleased with WFC. It's the only third party security software I have installed on the machine so far. It's a fantastic front end to the built in Windows Firewall. I really like the connection log, it makes troubleshooting MUCH easier than reading the firewall log in notepad!
So I've made some changes to my AppLocker Microsoft exception Publisher Rules. I have now added the following so that they cannot run:
I've been thinking about adding regedit.exe to my exception list too so that my SUA can't run the Registry Editor.
- odbcconf.exe
- sdbinst.exe
One thing that's worth doing is disabling Ease of access in Windows as this is such a security hole:
To disable Ease of access on login screen:
Change ownership of c:\windows\system32\utilman.exe to Administrators
cacls c:\windows\system32\utilman.exe /C /D Everyone
cacls c:\windows\syswow64\utilman.exe /C /D Everyone
The next thing I am considering for my secure build is to block/restrict removable devices/drives use Local Group Policy. More on that a bit later ;-)
Really enjoying your updates. You do realise I'm going to let you do all the work and then steal your ideas?
I'm a big fan of WFC too. Just waiting for a fix for running on the latest Insider build
Really enjoying your updates. You do realise I'm going to let you do all the work and then steal your ideas?
Hehe, I don't mind at all if you "steal" my ideas. It'll save you loads of time as my build has taken me months to research. I'm quite pedantic and fussy about what I want/like. I'm always open to ideas or things I can improve/change. I'm sure there are things I have missed or other items that can be improved.
I'll next post some of the important registry settings I changed to improve my security. Basically I made notes of my entire build from beginning until the end so I don't forget what I did. It helps with troubleshooting too.
Glad this is helping someone!
So some of the security registry changes I have made are as follows:
Some local group policy changes:
I've also disabled auto play for all media and devices.
The book: "Troubleshooting with the Windows Sysinternals Tools - 2nd Edition" arrived yesterday so I have been tinkering with Process Explorer quite a bit from Sysinternals. What an amazing tool! I was keen on using it to replace Task Manager but unfortunately PE doesn't show Network IO when launched as a SUA account which is a shame. Disk IO is also not available for a SUA account. The books really good if anyone's considering it.
Code:
;Set SmartScreen to warn:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer]
"SmartScreenEnabled"="Prompt"
;Turn off Remote Assistance:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Remote Assistance]
"fAllowToGetHelp"=dword:00000000
;Turn UAC to max setting:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"PromptOnSecureDesktop"=dword:00000001
"EnableLUA"=dword:00000001
"ConsentPromptBehaviorAdmin"=dword:00000002
;Enable PUP in Defender:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\MpEngine]
"MpEnablePus"=dword:00000001
;Deny elevation of unsigned executables:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"ValidateAdminCodeSignatures"=dword:00000001
;Enable Secure Sign in screen (Ctrl + Alt + Del:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon]
"DisableCAD"=dword:00000000
[HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon]
"DisableCAD"=-
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"DisableCAD"=-
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System]
"DisableCAD"=-
;Ask for user name and password at log on screen:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System]
"dontdisplaylastusername"=dword:00000001
;Disable cmd.exe for SUA account:
[HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System]
"DisableCMD"=dword:00000001Some local group policy changes:
Code:
1) Disable Network UI from login screen:
Computer Configuration - Administrative Templates - System - Logon: Change Do not display network selection UI to Enable
2) Disable app notifications on lock screen:
Computer Configuration - Administrative Templates - System - Logon: Change Turn off app notifications on the lock screen to EnableI've also disabled auto play for all media and devices.
The book: "Troubleshooting with the Windows Sysinternals Tools - 2nd Edition" arrived yesterday so I have been tinkering with Process Explorer quite a bit from Sysinternals. What an amazing tool! I was keen on using it to replace Task Manager but unfortunately PE doesn't show Network IO when launched as a SUA account which is a shame. Disk IO is also not available for a SUA account. The books really good if anyone's considering it.
D
Deleted member 178
@ParaXY about the reg tweaks , you should make a batch file and share it 
@ParaXY about the reg tweaks , you should make a batch file and share it
It's funny you should ask
I have a .reg file I can share but it has ALL (or most) of the changes I have made to my machine. Happy to share it but it also includes non-security changes (like modifying File Explorers view to remove all the bloat).
I can post if interested?
D
Deleted member 178
I copied your reg tweaks there : Windows' Security Tweaks
It's the first time I read the Windows Security Tweaks section of this forum so thanks for the link! I'm really keen on enabling the LSA Protection but nervous that you can't disable it if you have UEFI Secure Boot enabled (like I do). So how do I know if enabling this option will cause any issues for me and is there ANY way to disable it afterwards if I have problems?
I'll try posting my registry tweaks later today which include most of the changes I made to secure/customise my secure build. I used registry tweaks rather than making the changes in the local group policy as its just easier to implement.
UPDATE: So after enabling audit more for protecting the LSA process I decided to enable it for real and in Event Viewer I can now see:
I didn't even know this option existed until this morning so thanks for sharing this!
I also decided to block ftp.exe, cmd.exe and regedit.exe for my SUA in the Microsoft Publisher Exception rule in AppLocker.
IGMP was also disabled using:
Code:
Netsh interface ipv4 set global mldlevel=noneThis is great having IGMP disabled as it was flooding my firewall logs.
Last edited:
After tidying up my notes a bit I have attached my registry file (Windows10Customisations.txt) for (most) of the tweaks/changes I have made to my Windows 10 Enterprise setup (including some changes I made this morning). This includes security changes as well as look and feel changes. There is a brief description for each registry modification but if you are going to run this I would review the file first as I'm sure there are many settings that aren't suitable for some people/machines. I'd test it in a VM if you are interested in running this .reg file. NB: Some settings like the telemetry will only work on Enterprise versions.
I'll also include a screenshot of my "Programs and Features" so you can see what I uninstalled after installing Windows 10:
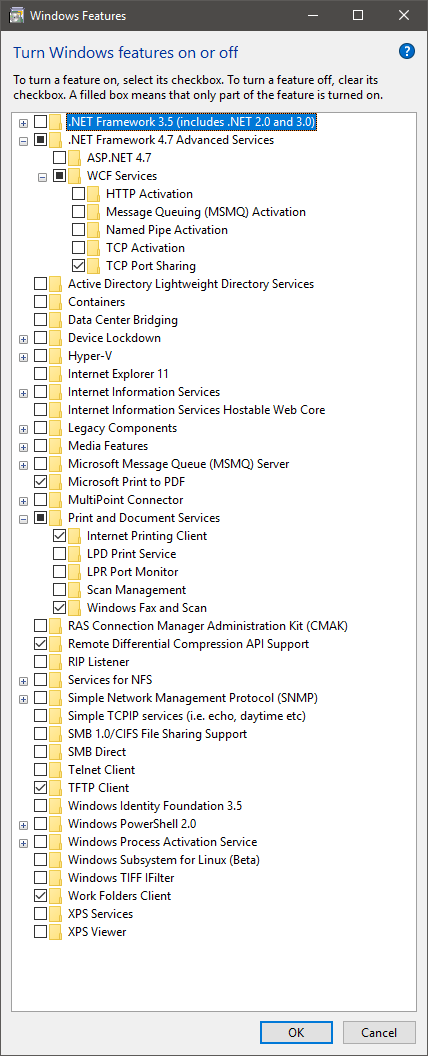
Guess I could remove "Windows Fax and Scan".
One change I made this morning was to enable cmd.exe again in the registry since I have an AppLocker rule to block this for my SUA account:
I've also attached a batch file containing some of the services I have disabled called "Services.txt". Basically I disable the following services:
I'll also include a screenshot of my "Programs and Features" so you can see what I uninstalled after installing Windows 10:
Guess I could remove "Windows Fax and Scan".
One change I made this morning was to enable cmd.exe again in the registry since I have an AppLocker rule to block this for my SUA account:
Code:
;Disable cmd.exe for current user:
[HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System]
"DisableCMD"=dword:00000000I've also attached a batch file containing some of the services I have disabled called "Services.txt". Basically I disable the following services:
- Connected User Experiences and Telemetry
- Windows Error Reporting
- dmwappushservice
- SSDP Discovery (UPnP)
- Network Connection Broker
- WinHttpAutoProxySvc
Attachments
Awesome! Many thanks for sharing the efforts of all your research and testing. Much appreciatedAfter tidying up my notes a bit I have attached my registry file (Windows10Customisations.txt) for (most) of the tweaks/changes I have made to my Windows 10 Enterprise setup (including some changes I made this morning). This includes security changes as well as look and feel changes. There is a brief description for each registry modification but if you are going to run this I would review the file first as I'm sure there are many settings that aren't suitable for some people/machines. I'd test it in a VM if you are interested in running this .reg file. NB: Some settings like the telemetry will only work on Enterprise versions.
I'll also include a screenshot of my "Programs and Features" so you can see what I uninstalled after installing Windows 10:
View attachment 148288
Guess I could remove "Windows Fax and Scan".
One change I made this morning was to enable cmd.exe again in the registry since I have an AppLocker rule to block this for my SUA account:
Code:;Disable cmd.exe for current user: [HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System] "DisableCMD"=dword:00000000
I've also attached a batch file containing some of the services I have disabled called "Services.txt". Basically I disable the following services:
Rename Windows10Customisations.txt to Windows10Customisations.reg and Services.txt to Services.bat.
- Connected User Experiences and Telemetry
- Windows Error Reporting
- dmwappushservice
- SSDP Discovery (UPnP)
- Network Connection Broker
- WinHttpAutoProxySvc
Awesome! Many thanks for sharing the efforts of all your research and testing. Much appreciated
No problem! I've really enjoyed researching all this. This is the result of many months of research and reading but the results have been worth it.
I thought I'd mention a couple other items too. I use Roboform (the locally installed version, not the cloud version) as my password manager and I also use KeePass for storing passwords.
There are some interesting security options worth mentioning here for these products:
- In KeePass in options you can enable: Enter master key on a secure desktop. Enabling this option will dim the desktop when you open KeePass and are prompted for credentials
- Once in KeePass click File and then Change Master Key and tick Windows user account:
This essentially "locks" or "restricts" access to your KeePass file/database to ONLY your Windows user account. It's worth reading up about this first before enabling as if you rebuild your machine or delete your user account you'll be locked out of your KeePass database. I took a backup of my database BEFORE enabling this option.
But the reason I *really* like this option is because, if someone logs into your machine as an admin or even another SUA account they can't open your KeePass database. They could of course reset your password if they had their own admin account but I also use a Key file to protect my database.
In Roboform I use the "Store Master Password in system protected storage":
With this option I don't need to enter my master password every time I need to enter a password into a website or application.
Again, if someone logs into the machine with their own account they can't open my Roboform passwords as it's tied to my user account. If someone else had admin access to your machine you wouldn't want to enable this option but since I am the only person using this machine I have enabled it as it makes things more convenient for me.
I've also found it quite useful to enable the column in task manager in the details tab called "Elevation". This allows you to see at a glance what processes are running as an admin or as your logged in account:
In my firewall logs I have loads of these outgoing requests being blocked:

Does anyone know what these are? Should I leave them blocked or allow them through the firewall?
I did a quick search online but didn't find anything helpful but these two entries seem to be flooding the logs.
Does anyone know what these are? Should I leave them blocked or allow them through the firewall?
I did a quick search online but didn't find anything helpful but these two entries seem to be flooding the logs.
The second one is Applocker attempting to validate the certificates of applications in the Applocker Policies.In my firewall logs I have loads of these outgoing requests being blocked:
View attachment 149456
Does anyone know what these are? Should I leave them blocked or allow them through the firewall?
I did a quick search online but didn't find anything helpful but these two entries seem to be flooding the logs.
Microsoft Windows Security | Microsoft Press Store
So I would expect this needs to be allowed.The service also monitors the local machine trusted root certificate store, and it invokes a user-mode task (%SystemRoot%\System32\AppIdCertStoreCheck.exe) to reverify the certificates at least once per day and whenever there is a change to the certificate store.
The second one is Applocker attempting to validate the certificates of applications in the Applocker Policies.
Microsoft Windows Security | Microsoft Press Store
So I would expect this needs to be allowed.
Aaah, many thanks for this! I came up empty handed when researching this but now that I know its for AppLocker to check the certs I have allowed it through the firewall.
Any idea what searchprotocolhost.exe is for?
Also, I have backgroundtaskhost.exe being blocked, do you know what this is used for?
And another one: C:\windows\system32\consent.exe. Is this one used when UAC is used to check certs for signed software?
Last edited:
You may also like...
-
Advice Request COMODO blocks Windows Updates with error 0x80070005
- Started by TheMalwareMaster
- Replies: 217
-
Advanced Plus Security Divine_Barakah's PC Security Config 2026
- Started by Divine_Barakah
- Replies: 20
-
Andy Ful's Software + Microsoft Defender + Malwarebytes Antimalware... How my PC Responds.
- Started by annaegorov
- Replies: 19
-
Technology Microsoft: Windows bug blocks Microsoft 365 desktop app installs
- Started by Brownie2019
- Replies: 3
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18