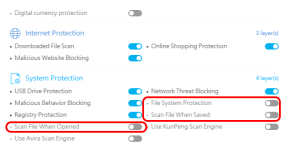
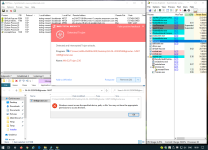
I try the 360TSEssentials from the morning. This version has no bloads but is older version from 360TS. Has olny the Avira engine. Is very light on my system .With malware samples i have good results. But with ransomware not good. If i clicked very fast to block I see some damage. If i clicked late ...totaly infection. I will wait your test with ransomware . Maybe the 360TS have improvement at HIPS.
And the extension still rubbish.I try the 360TSEssentials from the morning. This version has no bloads but is older version from 360TS. Has olny the Avira engine. Is very light on my system .With malware samples i have good results. But with ransomware not good. If i clicked very fast to block I see some damage. If i clicked late ...totaly infection. I will wait your test with ransomware . Maybe the 360TS have improvement at HIPS.