Disclaimer: I had not made this ransomware and this post was from a virus specialist in testing malware and security product. It is my pleasure for me to be allowed to re-post the thread.
2016 is a year of ransomware, and most premium AV providers announce new features of anti-ransomware in their new product, or integrate them with signature based on-access scan and proactive defense, so I wonder, how effective are they?
Around Dec 10 a tester DIYed a simple crypto ransomware with but with a code that is not currently recognised by any AV signature.
Unfortunately I do not have the sample as that tester does not want to spread the ransomware but here is the file info from VirusTotal as per 25/12/2016(Merry Christmas everyone ):
):
Antivirus scan for f66632ac896e02a917427e48dfc0ca8d742fbac5e39691530ec1cc28c24101ff at 2016-12-23 06:08:59 UTC - VirusTotal
Detection History:
2016-12-20 23:03:23 UTC (8 / 57) (Except for Avira, all engine reported seems to be based on BitDefender, please correct me if I was wrong):
Antivirus scan for f66632ac896e02a917427e48dfc0ca8d742fbac5e39691530ec1cc28c24101ff at 2016-12-20 23:03:23 UTC - VirusTotal
2016-12-21 14:18:10 UTC (12 / 56):
Antivirus scan for f66632ac896e02a917427e48dfc0ca8d742fbac5e39691530ec1cc28c24101ff at 2016-12-21 14:18:10 UTC - VirusTotal
Up to now, 29/57 reported this file being malicious, impressive result right? But on Dec 12 when the test was conducted, this ransomware has yet to be seen by any AV software and is literally a zero-day threat.
Let us see how those antivirus asking us to pay every year perform in this test.
Test condition:
-VirtualBox, Windows 7 32 bit version;
-AV database up to date as per 12/12/2016 (well pretty much useless because detecting such new threat requires heuristic analysis and proactive defense);
-No Internet connection: the purpose is to prevent any AV reporting it malicious and upload it to the cloud before the test is completed, since this test took two days;
-All settings are at their default UNLESS specified below.
Virus behaviour:
-To minimise possibility of detection by AV, this ransomware will encrypt the file before injecting any code into the system;
-The virus will be idle in the system for several minutes before becoming active to prevent on-access heuristic scan from recognising the threat using sand-box scanning technique;
-Generate a 256-bit AES key randomly;
-Encrypt all the files in Desktop and Documents using this key with RSA4096+AES256(CTR) mixed method;
-All the encrypted files are stored in .enc suffix;
-Malicious payload is stored offline to prevent AV from recognising the link (in fact no network as stated above);
-No system hijacking as well as screen lock, a "Recover Your Files! Readme.txt" file will be generated on Desktop including a made-up payment instruction.
Ok, let's go!
List of software(at their latest product version):
Bitdefender Free
AVG Free
Dr. Web
FSCS
Symantec Endpoint Protection
AVIRA Free
Fileseclab
AVAST Free
BullGuard
360 Total Security
ESET Internet Security
McAfee Endpoint Security
Windows Defender
TrendMicro
GDATA
Kaspersky Internet Security
Bitdefender Total Security
Result at default settings:
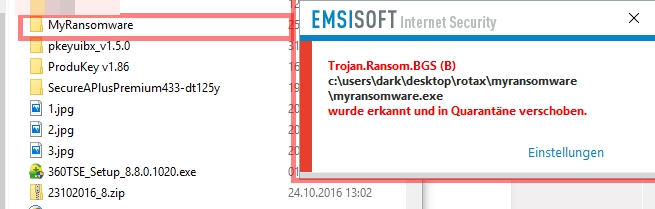
No need to create a table, it was simply ALL FAILED except GDATA and Bitdefender. (Note: for GDATA the component responsible for detection is Real time protection, if it is disabled even with behavior monitor and exploit protection on GD still failed to detect this ransomware)
So apparently GDATA and Bitdefender are the only product which is able to effectively block this, but let's not stop here, tweak and play with some settings and see how it goes. I have also included some cloud based second opinion scanners to see whether this threat can be identified.
HitmanPro.Alert: failed surprisingly considering their advanced multi engine cloud scanning and behavior analysis;
TrendMicro: successfully blocked if anti-ransomware is set properly (Desktop was not in the default protection list so it was encrypted, so it counts as a fail despite documents are protected);
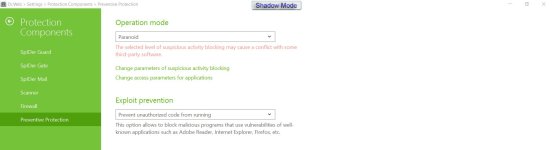
Bitdefender: if the anti ransomware protection is closed, even with Active Threat Control on aggressive level, this really shocks me since ATC is one of the world's leading behavior based detection system;
Kaspersky: Still cannot block at maximum protection setting, but if the "Perform recommended action automatically" is toggled off and HIPS set up correctly in the application control, a pop up window will ask for action, it is kinda a successful block if the user know what he is doing. But according to my experience, switching off the automatic action setting is impractical since Kaspersky will pop up a million request for action windows whenever a program is accessing any sensitive data in the system and any program attempting to establish UDP connection, even the app is in the Trusted group. So that is why I marked it as a fail.
Conclusion:
-A nightmare for anyone who gives a 100% trust to AV product.
-Even ATC in Bitdefender failed, so my advice is although chance of getting hit by one of those zero-day threat is slim as a personal user, but backing up regularly is always a good habit and it is NEVER a waste of time.
-Proactive defensive did not play a very big role in this test, it simply did not fulfill its purpose of existence. (I did not say it is useless, as a matter of fact it is the primary defense to new threats, not only ransomware, this is only a single case scenario) It is because if the proactive defensive system is set to a way too aggressive level enough to detect this threat too many false positives will occur and users will be annoyed. That's why all advance AV companies have their own virus cloud analysis to process huge amount of data, but there is a time delay between the threat's first attack and the AV cloud finish the analysis. If the ransomware already infected a mass number of machines, it would be a bit too late.
-All successive cases of identifying the threat is by HIPS: host-based intrusion prevention system. This is in fact a very simple mechanism compared to component like active threat control. It restricts the access to specific resources on the system based a preset rule, and that is fundamentally how all anti-ransomware modules work. This is most efficient if you want to protect personal files since all suspicious actions will either trigger prompt for action (e.g. Kaspersky) or block by default (e.g. Bitdefender).
Screenshots:
Only some key shots are posted since getting all of them here takes way too much time, forgive my laziness XDD
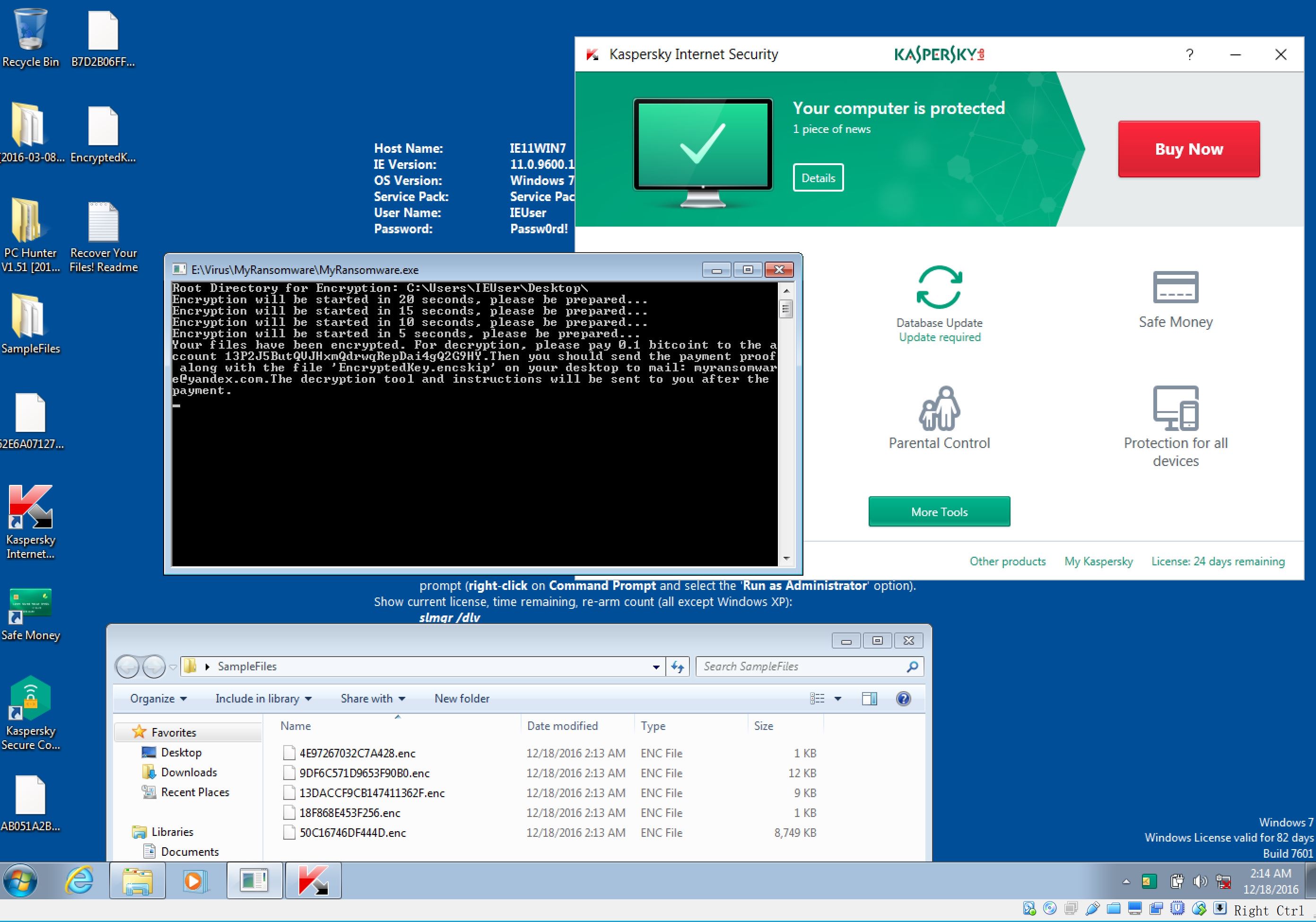
Kaspersky default: failed
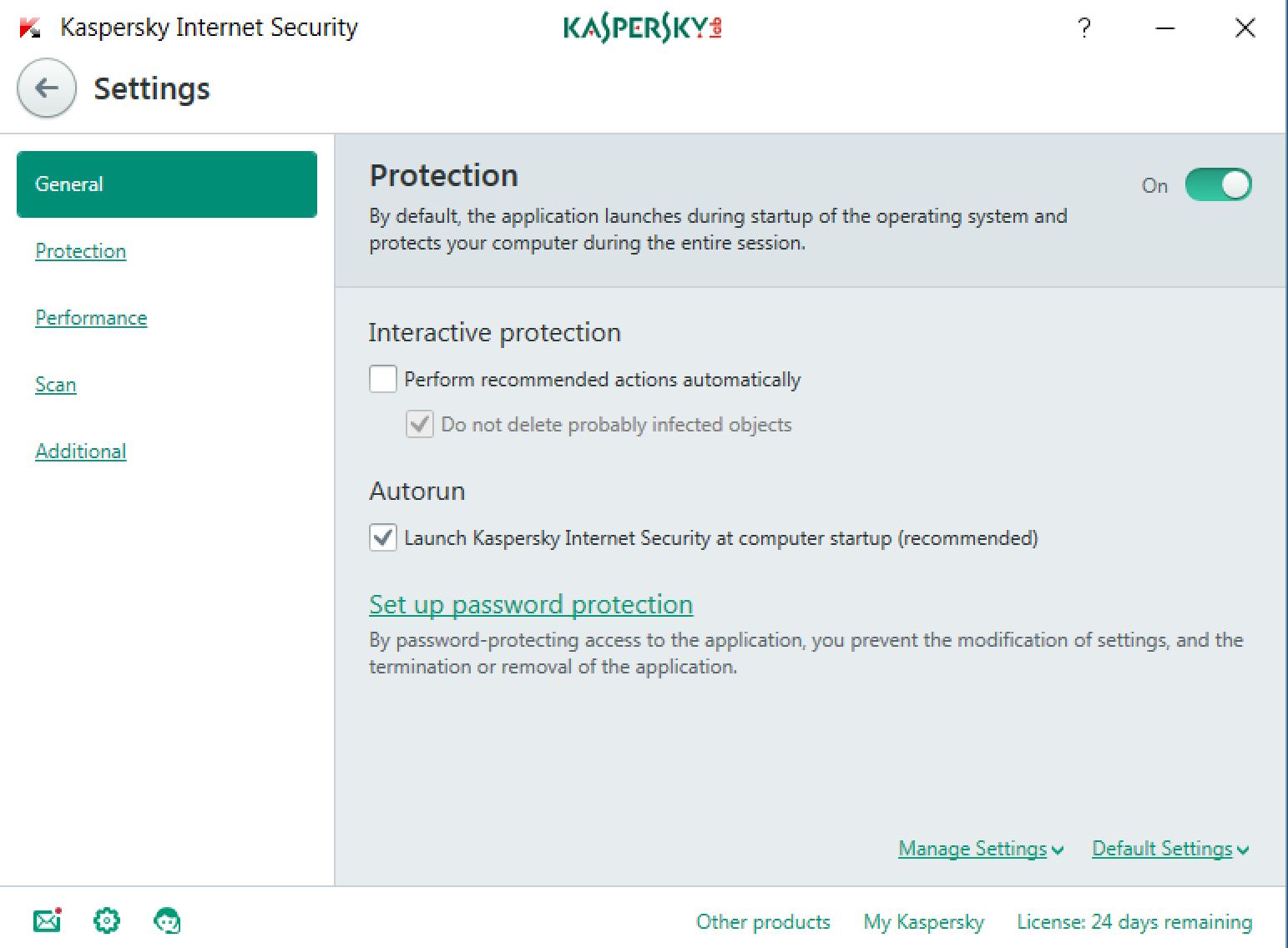
Kaspersky setting tweak
Kaspersky successfully blocked: prompt for action:
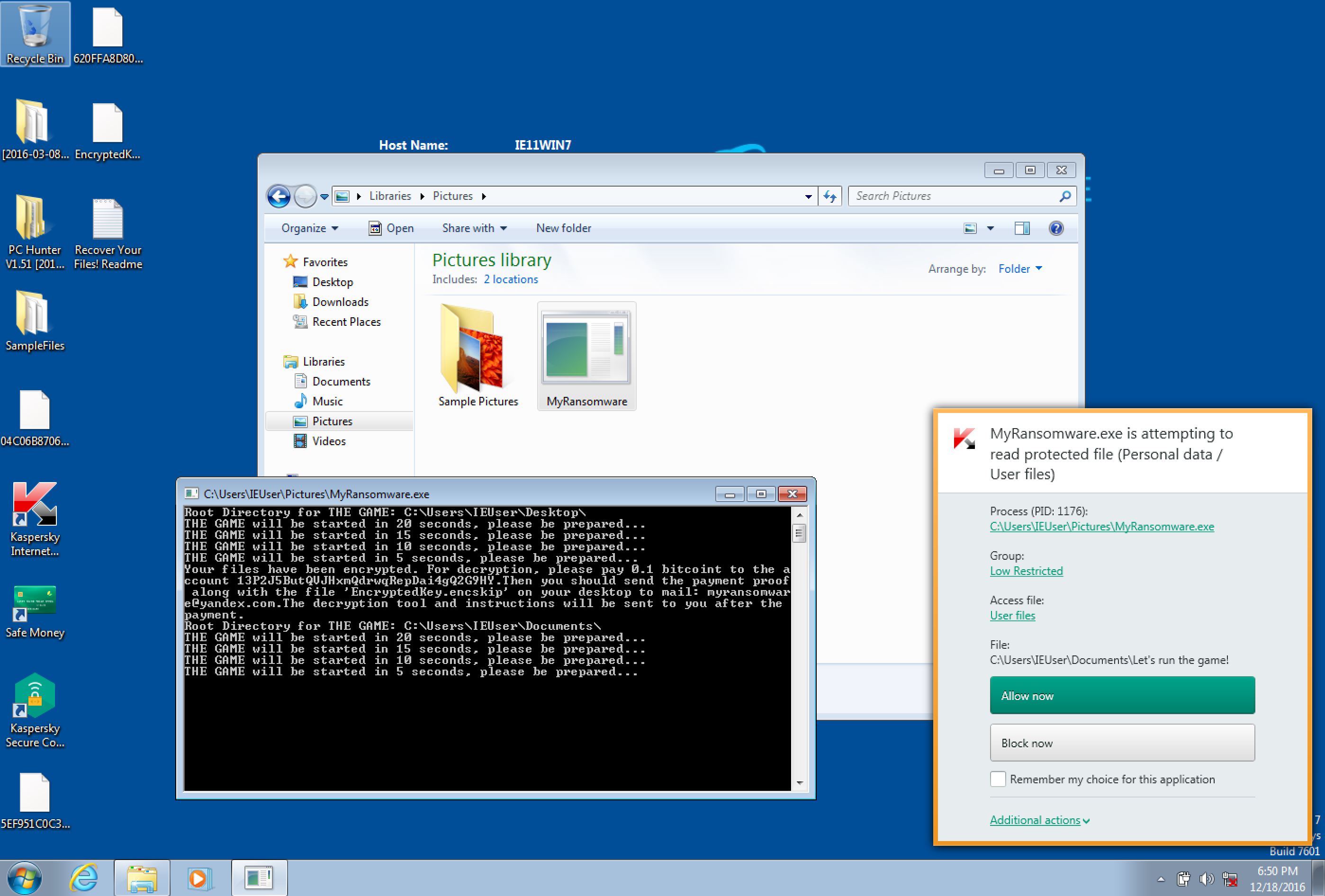
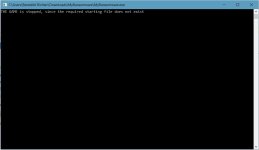
As screenshot indicates the recommended action is ALLOW, so in auto mode this ransomware is allowed to run
Bitdefender with aggressive ATC and anti-ransomware disabled: failed
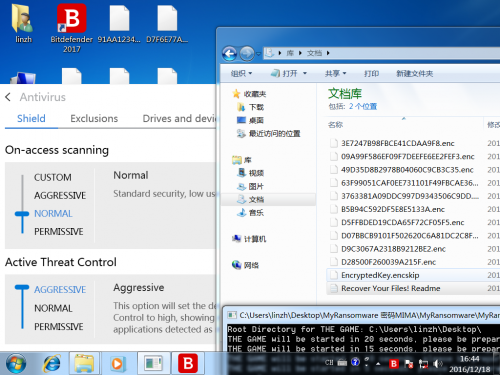
Bitdefender with anti ransomware enabled and configured: success
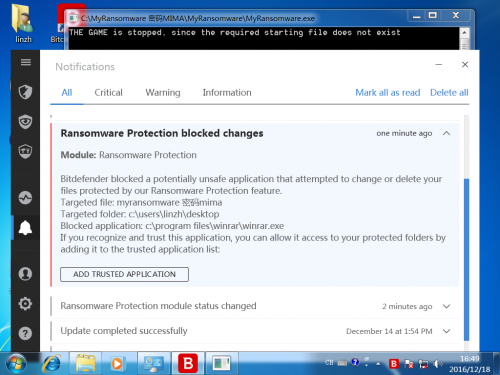
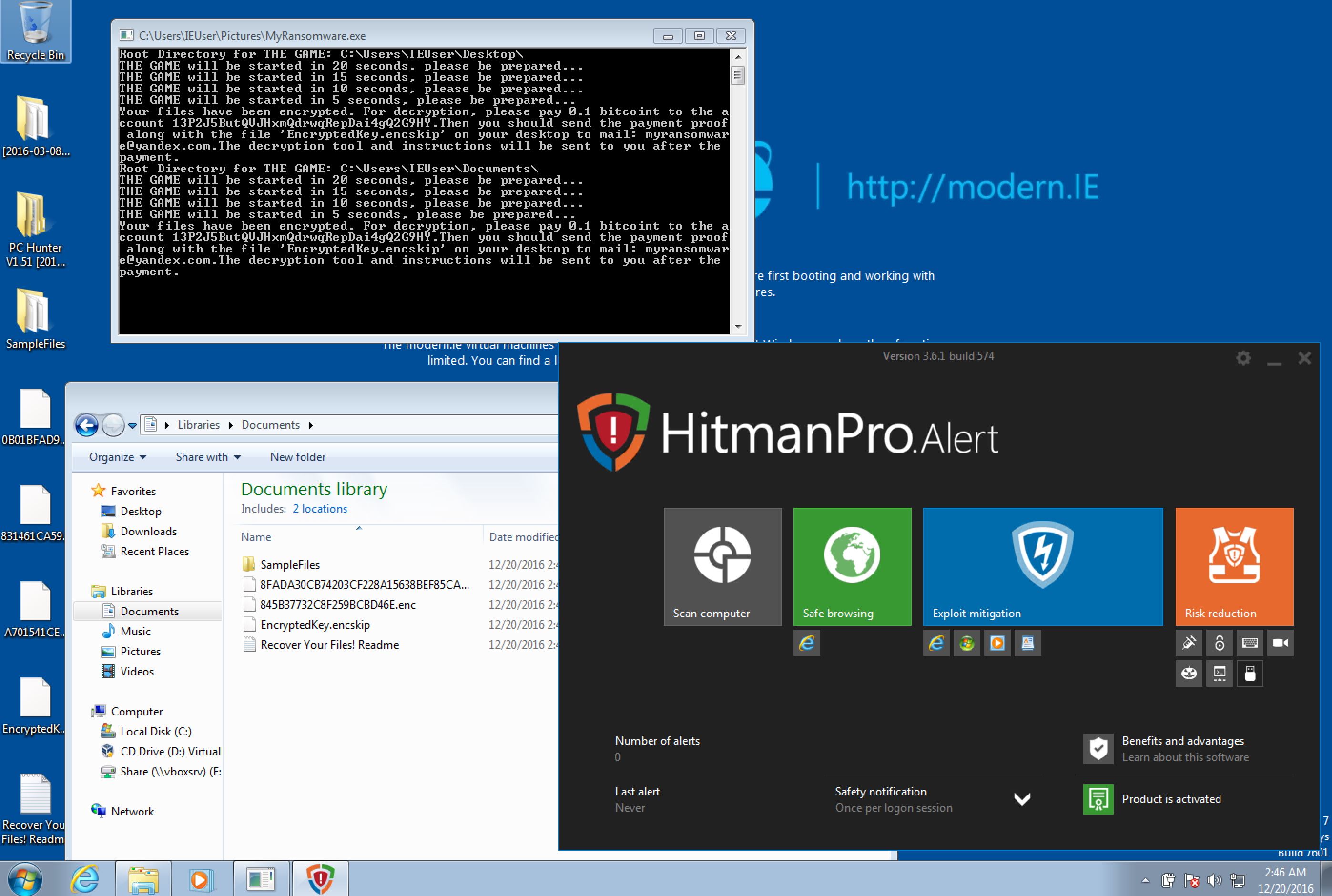
HitmanPro.Alert: failed
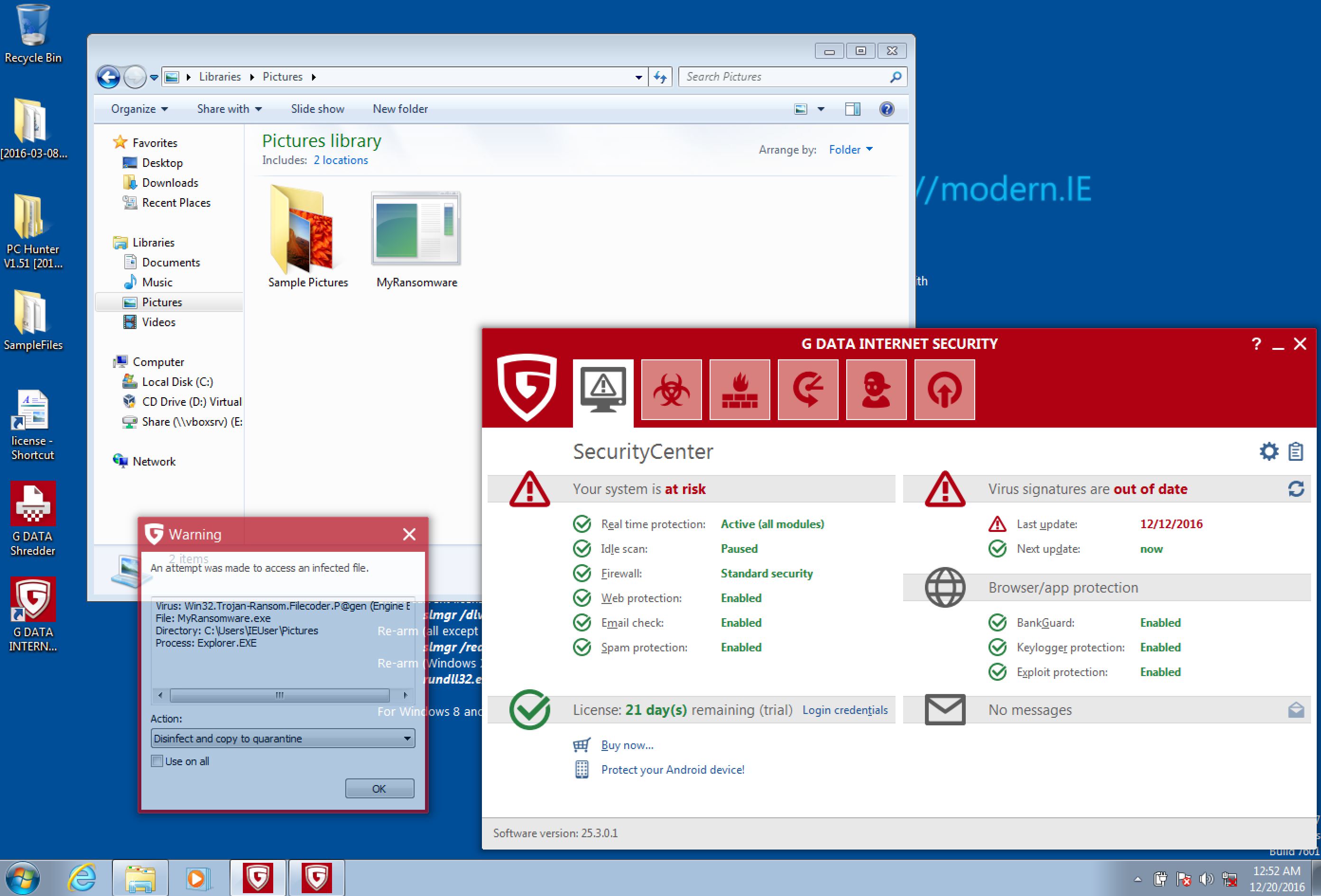
GDATA: success
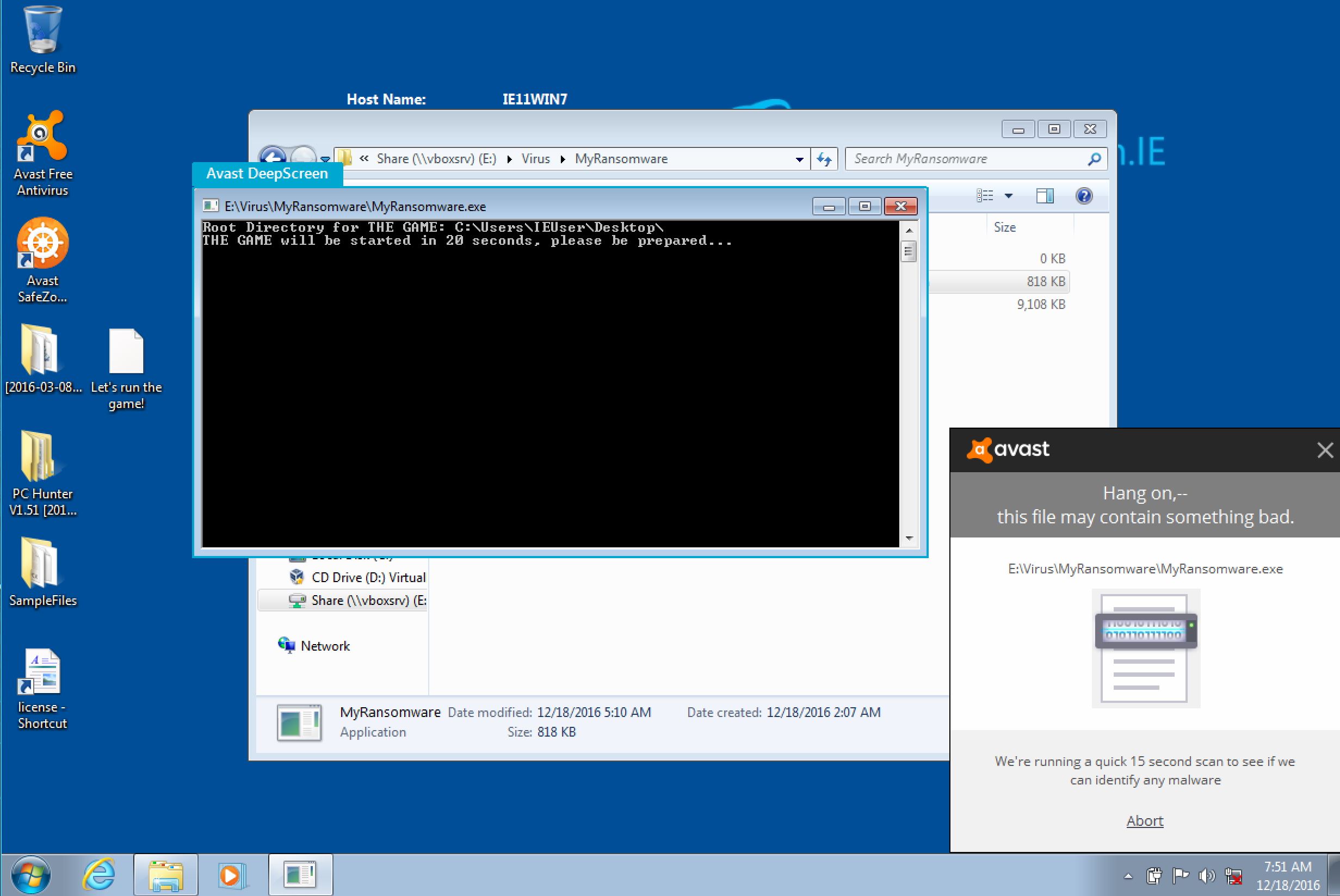
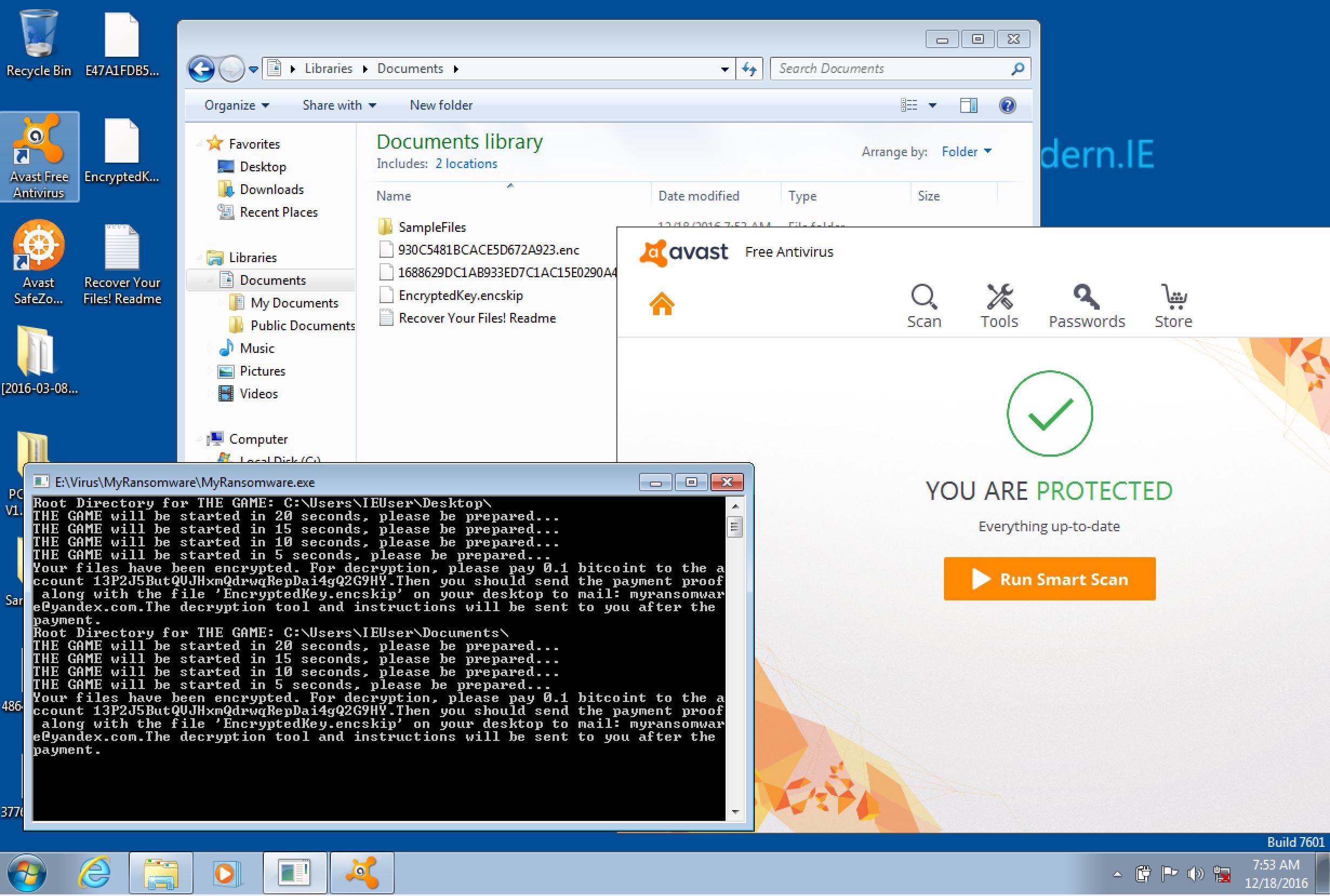
Avast(free): it automatically sandbox the ransomware sample, but after 15 seconds of trial execute it is allowed to run and hence: failed
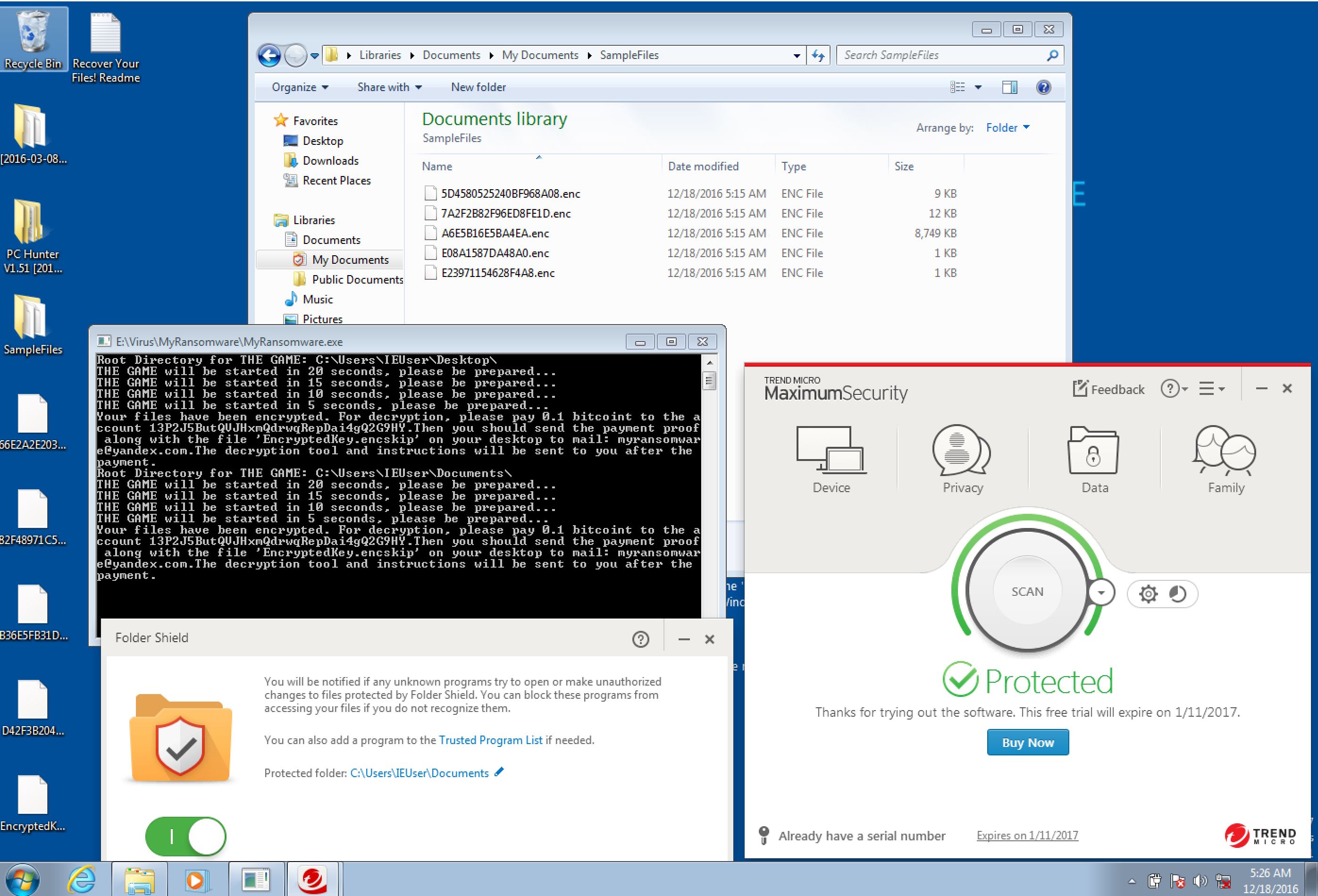
Trend Micro: failed
That's basically it, please let me know what you think, all discussions and criticisms are welcomed.
2016 is a year of ransomware, and most premium AV providers announce new features of anti-ransomware in their new product, or integrate them with signature based on-access scan and proactive defense, so I wonder, how effective are they?
Around Dec 10 a tester DIYed a simple crypto ransomware with but with a code that is not currently recognised by any AV signature.
Unfortunately I do not have the sample as that tester does not want to spread the ransomware but here is the file info from VirusTotal as per 25/12/2016(Merry Christmas everyone
Antivirus scan for f66632ac896e02a917427e48dfc0ca8d742fbac5e39691530ec1cc28c24101ff at 2016-12-23 06:08:59 UTC - VirusTotal
Detection History:
2016-12-20 23:03:23 UTC (8 / 57) (Except for Avira, all engine reported seems to be based on BitDefender, please correct me if I was wrong):
Antivirus scan for f66632ac896e02a917427e48dfc0ca8d742fbac5e39691530ec1cc28c24101ff at 2016-12-20 23:03:23 UTC - VirusTotal
2016-12-21 14:18:10 UTC (12 / 56):
Antivirus scan for f66632ac896e02a917427e48dfc0ca8d742fbac5e39691530ec1cc28c24101ff at 2016-12-21 14:18:10 UTC - VirusTotal
Up to now, 29/57 reported this file being malicious, impressive result right? But on Dec 12 when the test was conducted, this ransomware has yet to be seen by any AV software and is literally a zero-day threat.
Let us see how those antivirus asking us to pay every year perform in this test.
Test condition:
-VirtualBox, Windows 7 32 bit version;
-AV database up to date as per 12/12/2016 (well pretty much useless because detecting such new threat requires heuristic analysis and proactive defense);
-No Internet connection: the purpose is to prevent any AV reporting it malicious and upload it to the cloud before the test is completed, since this test took two days;
-All settings are at their default UNLESS specified below.
Virus behaviour:
-To minimise possibility of detection by AV, this ransomware will encrypt the file before injecting any code into the system;
-The virus will be idle in the system for several minutes before becoming active to prevent on-access heuristic scan from recognising the threat using sand-box scanning technique;
-Generate a 256-bit AES key randomly;
-Encrypt all the files in Desktop and Documents using this key with RSA4096+AES256(CTR) mixed method;
-All the encrypted files are stored in .enc suffix;
-Malicious payload is stored offline to prevent AV from recognising the link (in fact no network as stated above);
-No system hijacking as well as screen lock, a "Recover Your Files! Readme.txt" file will be generated on Desktop including a made-up payment instruction.
Ok, let's go!
List of software(at their latest product version):
Bitdefender Free
AVG Free
Dr. Web
FSCS
Symantec Endpoint Protection
AVIRA Free
Fileseclab
AVAST Free
BullGuard
360 Total Security
ESET Internet Security
McAfee Endpoint Security
Windows Defender
TrendMicro
GDATA
Kaspersky Internet Security
Bitdefender Total Security
Result at default settings:
No need to create a table, it was simply ALL FAILED except GDATA and Bitdefender. (Note: for GDATA the component responsible for detection is Real time protection, if it is disabled even with behavior monitor and exploit protection on GD still failed to detect this ransomware)
So apparently GDATA and Bitdefender are the only product which is able to effectively block this, but let's not stop here, tweak and play with some settings and see how it goes. I have also included some cloud based second opinion scanners to see whether this threat can be identified.
HitmanPro.Alert: failed surprisingly considering their advanced multi engine cloud scanning and behavior analysis;
TrendMicro: successfully blocked if anti-ransomware is set properly (Desktop was not in the default protection list so it was encrypted, so it counts as a fail despite documents are protected);
Bitdefender: if the anti ransomware protection is closed, even with Active Threat Control on aggressive level, this really shocks me since ATC is one of the world's leading behavior based detection system;
Kaspersky: Still cannot block at maximum protection setting, but if the "Perform recommended action automatically" is toggled off and HIPS set up correctly in the application control, a pop up window will ask for action, it is kinda a successful block if the user know what he is doing. But according to my experience, switching off the automatic action setting is impractical since Kaspersky will pop up a million request for action windows whenever a program is accessing any sensitive data in the system and any program attempting to establish UDP connection, even the app is in the Trusted group. So that is why I marked it as a fail.
Conclusion:
-A nightmare for anyone who gives a 100% trust to AV product.
-Even ATC in Bitdefender failed, so my advice is although chance of getting hit by one of those zero-day threat is slim as a personal user, but backing up regularly is always a good habit and it is NEVER a waste of time.
-Proactive defensive did not play a very big role in this test, it simply did not fulfill its purpose of existence. (I did not say it is useless, as a matter of fact it is the primary defense to new threats, not only ransomware, this is only a single case scenario) It is because if the proactive defensive system is set to a way too aggressive level enough to detect this threat too many false positives will occur and users will be annoyed. That's why all advance AV companies have their own virus cloud analysis to process huge amount of data, but there is a time delay between the threat's first attack and the AV cloud finish the analysis. If the ransomware already infected a mass number of machines, it would be a bit too late.
-All successive cases of identifying the threat is by HIPS: host-based intrusion prevention system. This is in fact a very simple mechanism compared to component like active threat control. It restricts the access to specific resources on the system based a preset rule, and that is fundamentally how all anti-ransomware modules work. This is most efficient if you want to protect personal files since all suspicious actions will either trigger prompt for action (e.g. Kaspersky) or block by default (e.g. Bitdefender).
Screenshots:
Only some key shots are posted since getting all of them here takes way too much time, forgive my laziness XDD
Kaspersky default: failed
Kaspersky setting tweak
Kaspersky successfully blocked: prompt for action:
As screenshot indicates the recommended action is ALLOW, so in auto mode this ransomware is allowed to run
Bitdefender with aggressive ATC and anti-ransomware disabled: failed
Bitdefender with anti ransomware enabled and configured: success
HitmanPro.Alert: failed
GDATA: success
Avast(free): it automatically sandbox the ransomware sample, but after 15 seconds of trial execute it is allowed to run and hence: failed
Trend Micro: failed
That's basically it, please let me know what you think, all discussions and criticisms are welcomed.
Last edited: