Many AVs seem to give signed malware a pass. What solutions have you adopted for this attack vector ? Is there a second opinion AV which ignores the ‘signed’ ?
Signed Malware & Antivirus Detection
- Thread starter notabot
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Voodooshield Pro in Smart mode.Many AVs seem to give signed malware a pass. What solutions have you adopted for this attack vector ? Is there a second opinion AV which ignores the ‘signed’ ?
comodo firewall with cs settings + disabling cloud lookup
comodo firewall with cs settings + disabling cloud lookup
What are cs settings ?
What are cs settings ?
ı use this one watch after 6.25 its include deny elevation request
ı use this one watch after 6.25 its include deny elevation request
Thanks !
CS setting on Comodo Firewall seem to be the best for this, including Ransomware.
~LDogg
~LDogg
If the digital signature is in the trusted vendor list, comodo will let it run even if you disable the cloud lookup.comodo firewall with cs settings + disabling cloud lookup
As Cruelsister said:
Just because a malware sample is signed doesn't mean it's signed with a certificate from a trusted vendor, so If you're using a Comodo product that uses the Trusted Vendors List, signed malware isn't something you should be concerned about. High-quality certificates from vendors on the TVL are far too costly and difficult for most blackhats to get their hands on and too useful to waste on the general populace.Note that the bulk of signed malware will be from some inconsequential publisher that will be from some fly-by-night Mook and would NEVER (never ever) make it to any TVL list.
Last edited:
RoboMan
Level 38
Verified
Honorary Member
Top Poster
Content Creator
Well-known
High Reputation
Forum Veteran
Signatures nowadays are BS. Everybody can get one. That's why anti-executables and antivirus with AC modules generate a trusted vendor list, which will work as a guarantee of which signed software can be run. Of course this doesn't cover when a trusted vendor gets hacked (such as Avast with CCleaner), and this could be avoided by not trusting any signature, wether it's a trusted vendor or not. Nevertheless, the CCleaner's kind of attack is unpredictable and will probably catch you. There's no way any software can prevent that.
F
ForgottenSeer 69673
This didn't stop CS from bypassing Appguard but she was running in protected mode and had access to one of the trusted vendors cert and didn't set up any other options. I always run in locked down mode with other settings.If the digital signature is in the trusted vendor list, comodo will let it run even if you disable the cloud lookup.
Take this exampleAs Cruelsister said:
Just because a malware sample is signed doesn't mean it's signed with a certificate from a trusted vendor, so If you're using a Comodo product that uses the Trusted Vendors List, signed malware isn't something you should be concerned about. High-quality certificates from vendors on the TVL are far too costly and difficult for most blackhats to get their hands on and too useful to waste on the general populace.
https://malwaretips.com/threads/signed-malware-25-12-2018.88860/
The digital signature belongs to Skype technologies. Do you think Skype technologies isn't included in comodo TVL ?
Then, if that signed malware downloads another unsigned exe, the security product can block it, but the original signed exe will run freely
True, but there's still three things that can stop this kind of malware:Take this example
https://malwaretips.com/threads/signed-malware-25-12-2018.88860/
The digital signature belongs to Skype technologies. Do you think Skype technologies isn't included in comodo TVL ?
Then, if that signed malware downloads another unsigned exe, the security product can block it, but the original signed exe will run freely
- If the certificate is revoked then Comodo will block/sandbox it regardless of if the certificate is from a vendor on the TVL
- Comodo's cloud database, which assigns each file a trust rating. If it's rated as malicious it'll be quarantined regardless of the certificate
- Viruscope, which will conduct behavioural analysis and quarantine anything that it determines as malicious
Last edited:
Signatures nowadays are BS. Everybody can get one. That's why anti-executables and antivirus with AC modules generate a trusted vendor list, which will work as a guarantee of which signed software can be run. Of course this doesn't cover when a trusted vendor gets hacked (such as Avast with CCleaner), and this could be avoided by not trusting any signature, wether it's a trusted vendor or not. Nevertheless, the CCleaner's kind of attack is unpredictable and will probably catch you. There's no way any software can prevent that.
This is exactly the type of attack I’m looking to eliminate though - so in a sense I’m looking for software which won’t follow a whitelist approach for something like this
You could run VoodooShield with these two options disabled:This is exactly the type of attack I’m looking to eliminate though - so in a sense I’m looking for software which won’t follow a whitelist approach for something like this
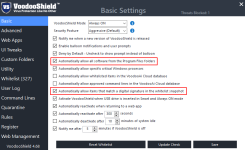
This way you'll have to approve the execution of absolutely every application on your system besides Windows components used to run the OS.
I used to run VS like this but it caused way too much irritation for whatever added protection it gave. If you're fine with dealing with a lot of prompts then feel free to give it a go.
You could run VoodooShield with these two options disabled:
View attachment 204331
This way you'll have to approve execution of absolutely every application on your system besides Windows components used to run the OS.
I used to run VS like this but it caused way too much irritation for whatever added protection it gave. If you're fine with dealing with a lot of prompts then feel free to give it a go.
Thanks - the too many prompts bit is a no go unfortunately, for the same reasons as you I’ll need to pass on this setup
True, it is basically the matter of money, which hackers have. Interestingly, most of those valid signatures are issued by Comodo. Still, there is only a handful of signed malware, most with invalid or outdated certificates, so blocking an unsigned malware works pretty effectively, for now.Signatures nowadays are BS. Everybody can get one.
Disabling just the digital signature option isn't too bad; you get far less prompts than disabling both. It'd mean that anything inside your Program Files folders would be allowed to run freely but anything outside - including executables related to those applications inside the Program Files folders - would trigger a prompt. (Some applications like Discord or Spotify run from AppData so it'd be those that mainly trigger prompts.)Thanks - the too many prompts bit is a no go unfortunately, for the same reasons as you I’ll need to pass on this setup
Last edited:
1. I don't think so, everything in the TVL or trusted by the user can run freelyTrue, but there's still three things that can stop this kind of malware:
Add to the fact that a lot of people run Comodo Firewall alongside an AV - which has the opportunity to detect it as well - and it's still not something I'd worry about. But hey, if anyone's still concerned they can easily mass-delete vendors from the TVL (and turn off cloud rating lookup if they're worried about whitelisted malware).
- If the certificate is revoked then Comodo will block/sandbox it regardless of if the certificate is from a vendor on the TVL
- Comodo's cloud database, which assigns each file a trust rating. If it's rated as malicious it'll be quarantined regardless of the certificate
- Viruscope, which will conduct behavioural analysis and quarantine anything that it determines as malicious
2. If the file is on TVL or trusted by the user, it won't be checked on cloud
3. Only if you set Viruscope to check files outside the sandbox too
Edit: Trusted Vendors, PC Firewall, Internet Protection | Internet Security Help
If the vendor is on the 'Trusted Software Vendor List 'AND the user has enabled 'Trust Applications signed by Trusted Vendors' in the 'File Rating Settings' panel, THEN the application will be trusted and allowed to run.
Last edited:
You may also like...
-
Malware News Malware bypassed macOS Gatekeeper by abusing Apple's notarization proccess
- Started by enaph
- Replies: 1
-
-
From Phishing to Malware: AI Becomes Russia's New Cyber Weapon in War on Ukraine
- Started by Brownie2019
- Replies: 1
-
Malware News System Utilities decompilation - detected as PUP by most AV vendors but is it actually just a PUP?
- Started by Khushal
- Replies: 2