So the * SMB Protocols * setting should be visible as Restricted SMB1. This is a usual Windows built-in restriction on Windows 10 (SMB1 not installed) which was not set by SWH. Does WD TV Play Media Player work well now? Can you see anything blocked via <Blocked Events>?I could not turn it off:
New Update Simple Windows Hardening
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
My WD TV Play Media Player cannot connect to my computer using Simple Windows Hardening.So the * SMB Protocols * setting should be visible as Restricted SMB1. This is a usual Windows built-in restriction on Windows 10 (SMB1 not installed) which was not set by SWH. Does WD TV Play Media Player work well now? Can you see anything blocked via <Blocked Events>?
They are enabled. If I turn them of, I cannot connect at all.View attachment 268280
Enable this.
Let's sum up.My WD TV Play Media Player cannot connect to my computer using Simple Windows Hardening.
- You are in shadow mode.
- Just before running SWH the WD TV Play Media Player works well.
- Just after running SWH the WD TV Play Media Player stops working.
- There are no blocked events when using <Blocked Events> button (for SRP and PowerShell).
Correct.Let's sum up.
Did you try restoring the Windows defaults via Menu >> Restore Windows Defaults?
- You are in shadow mode.
- Just before running SWH the WD TV Play Media Player works well.
- Just after running SWH the WD TV Play Media Player stops working.
- There are no blocked events when using <Blocked Events> button (for SRP and PowerShell).
"Did you try restoring the Windows defaults via Menu >> Restore Windows Defaults?"Correct.
No I did not, should I?
Yes. This will remove all changes made by SWH. Try to Log off the account and log in. Next, try the WD TV Play Media Player."Did you try restoring the Windows defaults via Menu >> Restore Windows Defaults?"
No I did not, should I?
But when I restore with my Macrium image from earlier, it does the same. It makes no different, it works before I try SWH and after, it does not.Yes. This will remove all changes made by SWH. Try to Log off the account and log in. Next, try the WD TV Play Media Player.
If you will restore Windows defaults via SWH (Menu >> Restore Windows Defaults), then only SWH changes will be removed. When you use Macrium image then you also remove all changes made by other programs, system tasks, and updates.But when I restore with my Macrium image from earlier, it does the same. It makes no different, it works before I try SWH and after, it does not.
I understand what you asked of me now. I did that earlier before I installed a new image again, and funny enough, it did not work after either. Something had change that was not been reversed.If you will restore Windows defaults via SWH (Menu >> Restore Windows Defaults), then only SWH changes will be removed. When you use Macrium image then you also remove all changes made by other programs, system tasks, and updates.
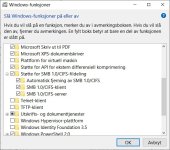
I found a difference. With SMB1 installed like on the below picture:I understand what you asked of me now. I did that earlier before I installed a new image again, and funny enough, it did not work after either. Something had change that was not been reversed.
SWH setting * SMB Protocols * shows on my computer that SMB123 are allowed:
From your post, it follows that on your machine it is not the case and SWH shows that SMB is Restricted. Is this true?
This is my machine before end after installation of SWH. The windows features did not change, and the settings is what you see on the picture.I found a difference. With SMB1 installed like on the below picture:
View attachment 268285
SWH setting * SMB Protocols * shows on my computer that SMB123 are allowed:
View attachment 268286
From your post, it follows that on your machine it is not the case and SWH shows that SMB is Restricted. Is this true?
Attachments
This is my machine before end after installation of SWH. The windows features did not change, and the settings is what you see on the picture.
These settings are like on my machine, but they are different from the settings you have posted here:
https://malwaretips.com/threads/possible-ways-to-harden-windows.112933/post-997939
So, the previous testing was done on different Windows settings. In previous settings, SMB1 was not installed and now it is. Now, you can Restrict or Allow SMB via SWH (Settings >> * SMB Protocols *) without the alert that SMB1 is not installed. The SWH restrictions for SMB do not install/uninstall SMB.
It seems that something changed the SMB features. This can be a source of your problem.
Anyway, now the SMB1 is installed and SWH shows that SMB protocols are allowed. If you still cannot use WD TV Play Media Player, then something else is involved here.
Edit.
@upnorth, is it possible to move the posts related to SWH and WD TV Play Media Player to the SWH thread?
Last edited:
"If you still cannot use WD TV Play Media Player, then something else is involved here."These settings are like on my machine, but they are different from the settings you have posted here:
https://malwaretips.com/threads/possible-ways-to-harden-windows.112933/post-997939
So, the previous testing was done on different Windows settings. In previous settings, SMB1 was not installed and now it is. Now, you can Restrict or Allow SMB via SWH (Settings >> * SMB Protocols *) without the alert that SMB1 is not installed. The SWH restrictions for SMB do not install/uninstall SMB.
It seems that something changed the SMB features. This can be a source of your problem.
Anyway, now the SMB1 is installed and SWH shows that SMB protocols are allowed. If you still cannot use WD TV Play Media Player, then something else is involved here.
Edit.
@upnorth, is it possible to move the posts related to SWH and WD TV Play Media Player to the SWH thread?
It looks like it. Thank you anyway
I installed f-secure Safe again instead of Bitdefender Total Security, and everything work fine with SWH installed.These settings are like on my machine, but they are different from the settings you have posted here:
https://malwaretips.com/threads/possible-ways-to-harden-windows.112933/post-997939
So, the previous testing was done on different Windows settings. In previous settings, SMB1 was not installed and now it is. Now, you can Restrict or Allow SMB via SWH (Settings >> * SMB Protocols *) without the alert that SMB1 is not installed. The SWH restrictions for SMB do not install/uninstall SMB.
It seems that something changed the SMB features. This can be a source of your problem.
Anyway, now the SMB1 is installed and SWH shows that SMB protocols are allowed. If you still cannot use WD TV Play Media Player, then something else is involved here.
Edit.
@upnorth, is it possible to move the posts related to SWH and WD TV Play Media Player to the SWH thread?
The problem was Bitdefender.
It is good that you managed to solve this problem. Be safe.I installed f-secure Safe again instead of Bitdefender Total Security, and everything work fine with SWH installed.
The problem was Bitdefender.

Thank you for the program and for your helpIt is good that you managed to solve this problem. Be safe.
F
ForgottenSeer 95367
SWH vs. Magniber CPL variant
https://www.socinvestigation.com/magniber-ransomware-payload-extension-changed-detection-response/
The infection chain:
typosquatting --> malicious website ---> Magniber downloaded directly as CPL file or in ZIP archive ---> user opens CPL file (Magniber is executed via LOLBins: control.exe & rundll32.exe)
SWH blocks by default opening CPL files (SRP restrictions). But, the rest will depend on the user. Magniber is often promoted as a digitally signed update/upgrade, so many users can be fooled to turn off the protection. This is probable especially when they are looking for pirated content. Anyway, the false alarms for updates/upgrades are very low with SWH settings, so many users can be also suspicious about these updates/upgrades. In such rare & unclear situations, the best solution is to wait one day (or more). In most cases, the AVs are able to correctly recognize threats after one day.
https://www.socinvestigation.com/magniber-ransomware-payload-extension-changed-detection-response/
Researchers at Asec Lab have observed the new indicators of Magniber. Since February 2022, Magniber has been using a Windows installer package file (.msi) instead of IE browser vulnerability for its distribution. The ransomware includes a valid certificate and was distributed in DLL form inside the MSI file. However, starting from July 20th (Wednesday), it is now being distributed as a CPL file extension instead of MSI.
As the cases of using an MSI file for distribution are decreasing, the attacker of Magniber likely has changed the method of distribution.
(...)
Magniber is currently being distributed in a typosquatting method that exploits typos made when entering domains, targeting Chrome and Edge users with the latest Windows version. As users may download ransomware by entering incorrect domains, extra caution is required.
The infection chain:
typosquatting --> malicious website ---> Magniber downloaded directly as CPL file or in ZIP archive ---> user opens CPL file (Magniber is executed via LOLBins: control.exe & rundll32.exe)
SWH blocks by default opening CPL files (SRP restrictions). But, the rest will depend on the user. Magniber is often promoted as a digitally signed update/upgrade, so many users can be fooled to turn off the protection. This is probable especially when they are looking for pirated content. Anyway, the false alarms for updates/upgrades are very low with SWH settings, so many users can be also suspicious about these updates/upgrades. In such rare & unclear situations, the best solution is to wait one day (or more). In most cases, the AVs are able to correctly recognize threats after one day.
Last edited:
You may also like...
-
New Update Defender Hardening Console (part of Hawk Eye Analysis Platform)
- Started by Trident
- Replies: 62
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
-