- Mar 4, 2018
- 9
Hi there,
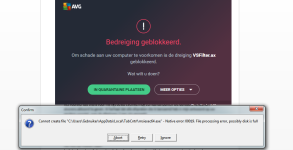
My problem is an svchost *32 file that has a strong hijack behind it, kicks in about 9 minutes after starting the pc. It kills every search for, or launch of antivirus software like adwcleaner / FRST.exe / Farbar and so on, it doesn't kill just any antivirus program just the ones that can do damage to the virus I guess. I think it's new virus because can't find any info that sounds just like mine except here on this site.
SOLVED - svchost.exe *32 Issue
My time window is small, 9 minutes before it kicks in and then it seems to become more active when I am active trying to locate and destroy. Very responsive like there is a person responding to what I do except that it's instant response. Cleverly made anyway..
How I got it.... totally my own doing, I tried to reactivate a copy of Word with the help of KMSpico. Umpf, stupid.
The one I think is the culprit is what I downloaded from:
KMSpico 10.2.0 Final + Portable (Office and Windows 10 Activator) | SadeemPC
After executing the downloaded file a notepad file was visible full of code.
I think that was the code I am fighting now, but not getting anywhere :
svchost*32 can't be terminated or the OS terminates, there are no services connected to that instance of svchost, it runs under "user", most of the time that I have been working on this there are 2 instances of the svchost*32 and 1 of them is taking up 50% of the cpu. If I shut down windows I get a blue screen.
That's about it.
I will attach the requested FRST.txt and Addition.txt BUT they are from before the 9 minutes mark when the virus kicks in. After that time window FRST will not run in any way.
Please advise!
Thank you,
Mark
My problem is an svchost *32 file that has a strong hijack behind it, kicks in about 9 minutes after starting the pc. It kills every search for, or launch of antivirus software like adwcleaner / FRST.exe / Farbar and so on, it doesn't kill just any antivirus program just the ones that can do damage to the virus I guess. I think it's new virus because can't find any info that sounds just like mine except here on this site.
SOLVED - svchost.exe *32 Issue
My time window is small, 9 minutes before it kicks in and then it seems to become more active when I am active trying to locate and destroy. Very responsive like there is a person responding to what I do except that it's instant response. Cleverly made anyway..
How I got it.... totally my own doing, I tried to reactivate a copy of Word with the help of KMSpico. Umpf, stupid.
The one I think is the culprit is what I downloaded from:
KMSpico 10.2.0 Final + Portable (Office and Windows 10 Activator) | SadeemPC
After executing the downloaded file a notepad file was visible full of code.
I think that was the code I am fighting now, but not getting anywhere :
svchost*32 can't be terminated or the OS terminates, there are no services connected to that instance of svchost, it runs under "user", most of the time that I have been working on this there are 2 instances of the svchost*32 and 1 of them is taking up 50% of the cpu. If I shut down windows I get a blue screen.
That's about it.
I will attach the requested FRST.txt and Addition.txt BUT they are from before the 9 minutes mark when the virus kicks in. After that time window FRST will not run in any way.
Please advise!
Thank you,
Mark