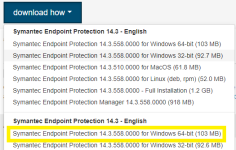
Download unmanaged from the link below

 www.comss.ru
www.comss.ru
System requirements :
* An additional 135 MB is required during installation.
Symantec Endpoint Protection client for Windows available hard drive system requirements when installed to an alternate drive
* An additional 135 MB is required during installation.
** If the program data folder is the same as the alternate installation drive, add 15 MB to the program data drive for your total. However, the installer still needs the full 150 MB to be available on the alternate installation drive during installation.
Symantec Endpoint Protection client for Windows Embedded system requirements
Want to run a free SPEM server to manage your family computers, PM me for a license file (.SLF) (works up to 10 years ).

Symantec Endpoint Protection
Symantec Endpoint Protection – комплексный антивирус и фаервол с несколькими уровнями безопасности. Антивирусная и превентивная защита, защита от сетевых угроз и эксплойтов нулевого дня, система предотвращения вторжений
 www.comss.ru
www.comss.ru
System requirements :
Software
Hardware
| Component | Requirements |
|---|---|
| Operating system (desktop) |
|
| Operating system (server) |
|
| Browser Intrusion Prevention | Browser Intrusion Prevention support is based on the version of the Client Intrusion Detection System (CIDS) engine. For more information, see Supported browsers for Browser Intrusion Prevention in Endpoint Protection. |
| Component | Requirements | ||
|---|---|---|---|
| Processor (for physical computers) |
| ||
| Processor (for virtual computers) | One virtual socket and one core per socket at 1 GHz minimum (one virtual socket and two cores per socket at 2 GHz recommended)
| ||
| Physical RAM | 1 GB (2 GB recommended) or higher if required by the operating system | ||
| Display | 800 x 600 or larger | ||
| Hard drive | Disk space requirements depend on the type of client you install, which drive you install to, and where the program data file resides. The program data folder is usually on the system drive in the default location C:\ProgramData. Available disk space is always required on the system drive, regardless of which installation drive you choose. Hard drive system requirements:
|
| Client type | Requirements |
|---|---|
| Standard | With the program data folder located on the system drive:
|
| Embedded / VDI | With the program data folder located on the system drive:
|
| Dark network | With the program data folder located on the system drive:
|
Symantec Endpoint Protection client for Windows available hard drive system requirements when installed to an alternate drive
| Client type | Requirements |
|---|---|
| Standard | With the program data folder located on the system drive:
|
| Embedded / VDI | With the program data folder located on the system drive:
|
| Dark network | With the program data folder located on the system drive:
|
** If the program data folder is the same as the alternate installation drive, add 15 MB to the program data drive for your total. However, the installer still needs the full 150 MB to be available on the alternate installation drive during installation.
Symantec Endpoint Protection client for Windows Embedded system requirements
| Component | Requirements |
|---|---|
| Processor | 1 GHz Intel Pentium |
| Physical RAM | 256 MB |
| Hard drive | The Symantec Endpoint Protection Embedded / VDI client requires the following available hard disk space:
These figures assume that the program data folder is on the system drive. For more detailed information, or for the requirements of the other client types, see the Symantec Endpoint Protection client for Windows system requirements. |
| Embedded operating system |
|
| Required minimum components |
|
| Templates |
The Enhanced Write Filter (EWF) and the Unified Write Filter (UWF) are not supported. The recommended write filter is the File Based Write Filter (FBWF) installed along with the Registry Filter. |
| Component | Requirements |
|---|---|
| Processor | 64-Bit Intel Core 2 Duo or later |
| Physical RAM | 2 GB of RAM |
| Hard drive | 500 MB of available hard disk space for the installation |
| Display | 800 x 600 |
| Operating system | Mac OS X 10.10, 10.11; macOS 10.12, 10.13 macOS 10.14 (Added for 14.2 MP1) Note: If you intend to upgrade to macOS 10.14.5 when it releases, 14.2 MP1 does not support kernel notarization. Review the following document for more information: Endpoint Protection 14.2 RU1 and kext notarization for macOS 10.14.5 |
| Component | Requirements |
|---|---|
| Hardware |
|
| Operating systems | For a list of supported operating system kernels, see Supported Linux kernels for Symantec Endpoint Protection. |
| Graphical desktop environments | You can use the following graphical desktop environments to view the Symantec Endpoint Protection for Linux client:
|
| Other environmental requirements |
|