Anti-malware tests regularly confirm, that ~99% of infections come via an email (65%) or via a browser (35%).
My browser uses Quad9 (DoH) and Netcfraft blocking malicious links and I open emails in a plain txt only.
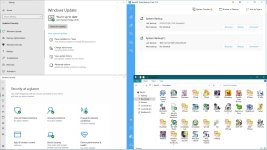
Windows Firewall is set to block all traffic except allowed apps, so it is default deny without notifications.
Disabled IPv6, Telemetry, WSH, some vulnerable services, all Windows features, except NET Framework.
I turn off PC with Wise Cleaners + tweaks, to remove startup entries/policies and to restore my settings.
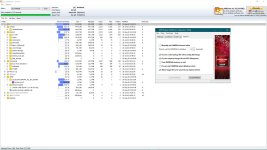
Anti-ransomware - backup partition - denied access to SYSTEM, Users permissions set to read only.
I use PatchMyPC/DriverEasy to keep software/drivers updated + Softpedia's Notifier for the rest.
Windows Repair Toolbox (+Malware Removal) + custom tools, take care of basic necessitates.
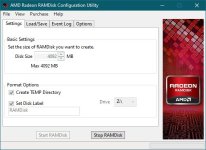
Browser with cache, Desktop, Downloads and Temp folders are stored in the RAMDisk, where malware tends to hide.
In case of an emergency (ransomware) I can hit Reset and Windows will boot with all those reset to the previous state.
EDIT: Since MS is moving Windows towards a scripted nightmare, I had no choice, but to ease down my tweaks, enable store, etc.
EDIT 2: I had to enable DNS Cache in order to use DoH, so I limited svchost.exe (+Windows apps) to connect only to MS servers IPs.
My browser uses Quad9 (DoH) and Netcfraft blocking malicious links and I open emails in a plain txt only.
Windows Firewall is set to block all traffic except allowed apps, so it is default deny without notifications.
Disabled IPv6, Telemetry, WSH, some vulnerable services, all Windows features, except NET Framework.
I turn off PC with Wise Cleaners + tweaks, to remove startup entries/policies and to restore my settings.
Anti-ransomware - backup partition - denied access to SYSTEM, Users permissions set to read only.
I use PatchMyPC/DriverEasy to keep software/drivers updated + Softpedia's Notifier for the rest.
Windows Repair Toolbox (+Malware Removal) + custom tools, take care of basic necessitates.
Browser with cache, Desktop, Downloads and Temp folders are stored in the RAMDisk, where malware tends to hide.
In case of an emergency (ransomware) I can hit Reset and Windows will boot with all those reset to the previous state.
Disabled #disable-oow-video
Disabled #heavy-ad-privacy-mitigations
Enabled #disable-yandex-extensions
Enabled #dns-httpssvc
Enabled #dns-over-https
Enabled #enable-heavy-ad-intervention
Enabled #enable-quic
Disabled #heavy-ad-privacy-mitigations
Enabled #disable-yandex-extensions
Enabled #dns-httpssvc
Enabled #dns-over-https
Enabled #enable-heavy-ad-intervention
Enabled #enable-quic
EDIT: Since MS is moving Windows towards a scripted nightmare, I had no choice, but to ease down my tweaks, enable store, etc.
EDIT 2: I had to enable DNS Cache in order to use DoH, so I limited svchost.exe (+Windows apps) to connect only to MS servers IPs.
Attachments
Last edited: