- Content source
- https://youtu.be/zrpOzV-5ekM
App Review The Zone Alarm challenge.
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It is advised to take all reviews with a grain of salt. In extreme cases some reviews use dramatization for entertainment purposes.
- Content created by
- Andy Ful
I created this video as the continuation of the AVs challenge to show that Antimalware kernel drivers and protected services of popular AVs can be tampered with (from Userland with high privileges), assuming that they are not protected by VBS.
The presented method could be used in the wild because the most important part of it is documented. If so, it was used rarely because I did not see any reference on the web.
It does not use vulnerable drivers and does not abuse PPL.
The presented method is not a full attack, and it is not probable that it can affect home users. However, it can probably be used as a part of targeted attacks in businesses.
Zone Alarm is taken only as an example. The presented method was tested by the author on several well-known Antiviruses, with similar effects.
App Review - Microsoft Defender's challenge.
The presented method could be used in the wild because the most important part of it is documented. If so, it was used rarely because I did not see any reference on the web.
It does not use vulnerable drivers and does not abuse PPL.
The presented method is not a full attack, and it is not probable that it can affect home users. However, it can probably be used as a part of targeted attacks in businesses.
Zone Alarm is taken only as an example. The presented method was tested by the author on several well-known Antiviruses, with similar effects.
App Review - The Comodo's challenge.
App Review - Comodo's challenge part 2.
App Review - Eset's challenge.
App Review - Microsoft Defender's challenge.
App Review - Bitdefender's challenge.
In this case, the real-time protection and the file scan do not work after attack. But Zone Alarm cannot see it.
Thank you for performing this test and I wasn’t aware there is now emulation on demand. This has been added recently.
Last edited:
That sounds good, I'll give it another try. The last time I used it, it was quite buggy and had performance issues.Thank you for performing this test and I wasn’t aware there is now emulation on demand. This has been added recently.
There is an update coming soon.That sounds good, I'll give it another try. The last time I used it, it was quite buggy and had performance issues.
What will it have. You wrote that like "Just wait and see". You've got me interested.There is an update coming soon.
In this case, the real-time protection and the file scan do not work after attack. But Zone Alarm cannot see it.
Not only that, but ZA's settings interface gives no indication to the user that it's been crippled by malware.
Last edited:
Yeah, I have escalated that with ZoneAlarm and will now escalate with Check Point as well, because Harmony Endpoint will be vulnerable too.Not only that, but ZA's settings interface gives no indication to the user that it's been crippled by malware.
F
ForgottenSeer 109138
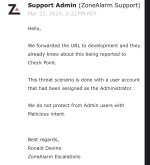
lol choose your admins wisely!The reply from ZoneAlarm is:
View attachment 282408
That is what I noted in my second post.
That is why the Zero Trust Model is recommended for Enterprises.
There are many key principles behind it, for example (from Wikipedia):
- Single strong source of user identity
- User authentication
- Machine authentication
- Additional context, such as policy compliance and device health
- Authorization policies to access an application
- Access control policies within an application
Last edited:
Speaking of that, it is what I proposed to Check Point as well.Additional context, such as policy compliance and device health
Under “Compliance” a new rule to ensure software drivers are working correctly should be implemented. Upon computer startup, software should check drivers state.
If compliance is not met, it should be communicated to admins and they should be able to push a fix quickly.
That’s assuming that HEP, just like ZA, will be displaying green checkmarks when filter drivers are disabled.
Speaking of that, it is what I proposed to Check Point as well.
Under “Compliance” a new rule to ensure software drivers are working correctly should be implemented. Upon computer startup, software should check drivers state.
If compliance is not met, it should be communicated to admins and they should be able to push a fix quickly.
That’s assuming that HEP, just like ZA, will be displaying green checkmarks when filter drivers are disabled.
If the attacker can get high privileges, the Windows OS can be hardly protected. There are too many possibilities for hiding the malicious code and attacking the Windows kernel. You cannot be sure that the system is clean after disinfection. All AV vendors know it, but it seems that not all security-aware people know it too.
I think that sooner or later the AV vendors must cooperate with Microsoft to protect the antimalware drivers via VBS. But, I have no idea how this could affect the functionality of AVs.
Last edited:
It seems that Zone Alarm and Kaspersky staff are interested in taking a closer look at the attack method. So, I will send them the details.
I am not sure if that method will be covered, but I did my best.
I am not sure if that method will be covered, but I did my best.
ZoneAlarm or Check Point? Well they are the same company anyway. I’ve provided your email address to Check Point.It seems that Zone Alarm and Kaspersky staff are interested in taking a closer look at the attack method. So, I will send them the details.
I am not sure if that method will be covered, but I did my best.
ZoneAlarm or Check Point? Well they are the same company anyway. I’ve provided your email address to Check Point.
Check Point asked about the details of the ZoneAlarm challenge.
If the attack includes something they don’t monitor yet, they will need to update hooks and kernel drivers, most probably it will be fixed with the early March update. In Israel the working week starts from Sunday so they will probably review it today.Check Point asked about the details of the ZoneAlarm challenge.
If they already monitor and record what’s used in this attack, they will just update the T1562.001 IoCs and will write rules for the emulation. This will be very quick.
Update: Check Point working on a fix which will be implemented soon.
You may also like...
-
-
App Review Bitdefender Free vs ZoneAlarm free Antivirus
- Started by Pat MacKnife
- Replies: 12
-
AV-Comparatives False Alarm Test - September 2025
- Started by Spartan
- Replies: 7
-
App Review iDefender Pro (Présentation & Reviews)
- Started by Shadowra
- Replies: 8
-
App Review iDefender Free (Presentation & Reviews)
- Started by Shadowra
- Replies: 14