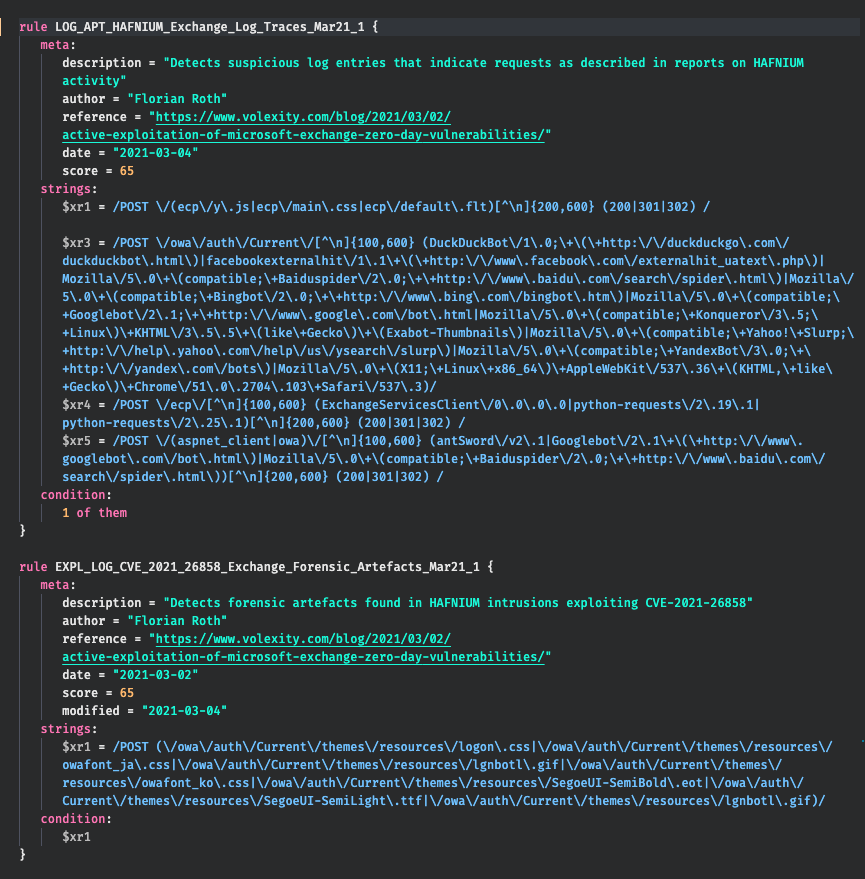
Meet our new fast and flexible multi-platform IOC and YARA scanner THOR in a reduced free version named THOR Lite. THOR Lite includes the file system and process scan module as well as module that extracts “autoruns” information on the different platforms.
While our enterprise scanner THOR uses VALHALLA‘s big YARA rule base, the free THOR Lite version ships with the Open Source signature base, which is also part of our free Python scanner LOKI.
- Free scanner for Windows, Linux and macOS
- Precompiled and encrypted open source signature set
- Update utility to download tested versions with signature updates
- Documentation
- Option add your custom IOCs and signatures
- Different output formats: text log, SYSLOG (udp/tcp/tcp+tls), JSON to file, JSON via Syslog
- Scan throttling to limit the CPU usage
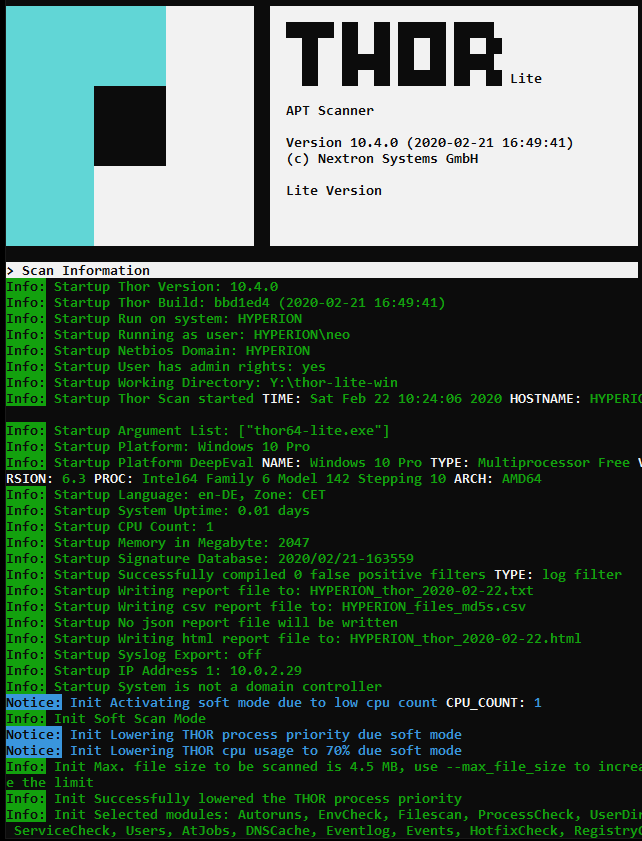

THOR Lite: Free Multi-Platform IOC and YARA Scanner - Nextron Systems
Free IOC and YARA Scanner - Meet our fast and flexible multi-platform IOC and YARA scanner THOR in a community version named THOR Lite.
 www.nextron-systems.com
www.nextron-systems.com

THOR Lite: Free Multi-Platform IOC and YARA Scanner - Nextron Systems
Free IOC and YARA Scanner - Meet our fast and flexible multi-platform IOC and YARA scanner THOR in a community version named THOR Lite.
 www.nextron-systems.com
www.nextron-systems.com
Not to be confused with the Danish company Heimdal Securitys Thor products.
Disclaimer
You use THOR lite on your own risk.
Last edited: