I think that you are right.

Furthermore, the whole terminology used by AV vendors to name particular detections is a mess. Some order was introduced by MITRE ATT&CK™ framework but it is rather a beginning of the long road.
The world of malware is very complex and changing. So, it will not be easy to make good order there.

More information about the current state of this topic can be found in some articles, for example:
Malware classification and composition analysis: A survey of recent developments.
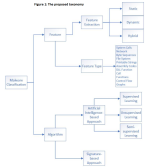
Here is an example, but it will be probably useful only for
@struppigel or professionals who are interested in malware classification: