Why a seperate thread?
I got a few questions of the uB0 settings I posted in Old School's uB0 tips and tricks. In stead of stealing that thread I thought it might be better to create a new thread to explain these settings. I also got a question how to apply this on other browsers, so I left out the chromium specific settings, so members using Firefox can also apply these settings.
1. Stronger and lighter medium protection on HTTP websites.
Since let’s encrypt.org provides free DomainValidation certificates, 50% of the websites are encrypted now. Encrypted or secure websites have a padlock sign and have HTTPS before the domain, while unencrypted or insecure websites have HTTP (no last S of Secure) before the websites domain name.
While the DV-certificate ‘only’ guarantees that the website is operated by the person or organization claiming owning the domain, this low-level formality provides enough hassle for cyber criminals to choose the easy way and setup a HTTP website to source their malware. In the Netherlands a valid bank account and first payment to an official ISP is required to get a DV-certificate for your website.
uB0 alllows to write custom AdBlockPlus rules in the My Filters tab, lets write a AdBlockPlus rule to block nasty stuff from insecure/unsafe HTTP websites only (see picture below).
View attachment 215406
This simple single rule blocks all third-party requests (including XMLHTTPrequest, WebSocket, WebRTC, Ping, Object and ObjectSubrequests and Other e.g. beacons), so it provides more protection than uB0 medium mode protection which ‘only’ blocks third-party scripts and (i)frames (subdocuments in AdBlockPlus syntax).
When you enable this, you can disable the Malware Domain blacklist which are enabled by default in uB0, since 95% of the malicious websites are HTTP (insecure) websites. There are as many websites as there are people living on this planet, so a community maintained blacklist with 300.000 URL’s is only a water drop on a hot glowing plate. Also malicious websites are only active for days, so half of these Malware Domain URL’s are dead links anyway.
So with just one simple rule you can make uB0 lighter and have stronger than medium mode protection on HTTP websites! Together with Google's Safe browsing or Microsoft's SmartScreen this will provide excellent protection against malicious websites.
2. Less hassle and maintenance medium mode protection (on HTTPS websites)
Medium mode protection (blocking third-party scripts and frames) enhances security since it protects against cross site scripting on the websites you visit. It is much harder to completely take over a website (and plant first party scripts) than to use vulnerabilities in CMS systems or JavaScript Libraries to redirect to a websites which is operated by cyber criminals. Sadly uB0 medium mode also breaks most websites since most websites use third-party services to build, manage and operate their website.

Due to the increased popularity of adblock extensions many advertising and tracking services use URL, pixel and image-tags and other behind-the-scene tricks to circumvent third-party java script and (i)frame blocking. This reduces the effectiveness of medium-mode blocking against tracking and advanced advertising redirects. So medium-mode blocking breaks many websites while the benefits are declining in real world practice with modern day advertising and tracking services.

So why bother to enable medium mode protection anyway? Well when you look at data provided by Domain Name Services 50 percent of the malware originates from fancy Top Level Domains (like website.download, website.link, website.review, website.xys, website.zip, etc) and some country domains (e.g. Palua, Tokelau, Sint Maarten, Russia, Turkey, etc).
Most people only visit websites in their own or English language. So for me living in the Netherlands and not speaking Turkish,Russion, Ukraine or Chinese there is no much need to visit websites originating from these countries or having fancy (general) TLD’s.
With my internet habits most of the websites I visit have the TLD of NL (Netherlands), COM, NET and ORG. So by adding an exception (NOOP = no operant) for third-party requests to these TLD’s, I cut down the risk of malware on HTTPS websites by half again (this sounds spectacular but only reduces the risk from 5 to 2.5%

),
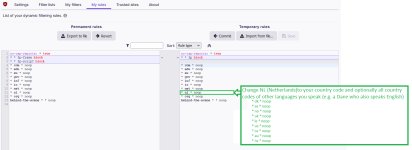
You need to enable advanced protection and add only a few rules to the default medium mode rules in My Rules tab (in my case only four NOOP rules to allow the COM, NET, NL and ORG Top Level Domains):
View attachment 215405
When you are English speaking in stead of NL (Netherlands), you could allow CA, IE, NZ, SA, UK, US or when you are German speaking in stead of NL you could NOOP the country codes D, AT, CH, when you are from Scandinavian language country (Denmark, Norway, Sweden or Iceland) you could allow DK, IS, NO, SE and when you are from Portugal you could enable the country codes of Portugal, Brasil, Angola, Mozambique, Cape Verde, Guinee-Bissau and so on.
So how does this work in practice? Let;s look at at website marked as malware
Let's use the Malware Domains List to evaluate the impact of these settings.
View attachment 215411
1. Stronger and lighter medium protection on HTTP websites.
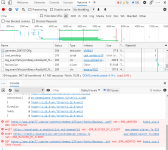
When we go to the first active link 4dexports.com the website is displayed and it appears to look fine, because images and style sheets are allowed and all other third-party stuff is blocked by our single My Filters rule (HTTP://*^$third-party,~image,~stylesheet) as shown in uB0's logger which only see's the top document, CSS-style sheets and images (which are allowed by our single HTTP block rule)
View attachment 215409
2. Less hassle and maintenance medium mode protection
When we click on the uB0 icon, we can see that the third party references to the Google fonts is allowed (nooped because it is grey). When there was malware on this site it would be paralyzed (by our single HTTP block third-party rule) and only (remaining HTTPS) third-party references to COM, NET, NL and ORG Top Level Domains would be allowed by our Dynamic uB0 rules.
View attachment 215410
So how does this work in practice? Let;s look at at website known as goodware
1. Stronger and lighter medium protection on HTTP websites.
Because BBC.com is a HTTPS website, the static AdBlockPlus rule in My Filters has no effect
View attachment 215412
2. Less hassle and maintenance medium mode protection
Hey Kees, you promised less hassle, now the website seems to be broken! Yes that is easily explained by clicking on the uB0 icon. It seems that BBC.COM uses third party sources from CO.UK domains which we have not NOOPed (BBC.COM is dark grey means NOOPed, the two CO.UK domains are light grey, so have no exception)
View attachment 215413
How to fix BBC.COM?
Simply add a NOOP rule for the UK Top Level Domain.
View attachment 215414
BBC.COM will now render properly as third-party references to (country code) UK websites are allowed now
View attachment 215415
Less hassle and maintenance?
From now on all websites with third-party UK are NOOPed
View attachment 215417
But also websites with another TLD (e.g. INFO) which just use COM, NET, as third--party sources will render properly as this example shows. By clicking on the uB0 icon it shows that this INFO website only uses third-party references to COM and NET (and NL). Reason is that most web services have COM or NET or ORG as TLD, so even websites with a general fancy TLD (like hardware.info) will render properly (without adding a NOOP rule for INFO)
View attachment 215418
I only use My Filters (with most used add and tracking services) and DisConnect malvertising filter. Because Disconnect is used as default blocker in Firefox this list is clean and breaks near to zero websites.
View attachment 215419
I have attached my uBlock static filter list, so you can check how this ultra light uB0 setup works out for your browsing behavior.
My blocklist is based on WSTech research on most used ad and tracking networks and is offered as a default list in SmartAdBlock extension (the WsTech200 list), so it is not my determined by me (I would love to take the credits, but I just collected them and changed it in AdBlockplus format) 
uB0 does not provide download protection, this is why uB0 was rated badly in a test. When you use a Chromium variant you can add a flag to close down the risk of drive-by's or unintended download of executables from HTTP websites.
View attachment 215421
TROUBLE SHOOTING TIP
Problem CNN.COM does not play VIDEO's.
STEP 1 NOOP 3rd-party scripts FOR THIS WEBSITE (you still have uB0 EASY and HTTP third-party protection )
in this example that was enough to allow videos to play (culprit was CNN.IO which was also blocked)
View attachment 215429
STEP 2 ALSO NOOP 3rd-party frames FOR THIS WEBSITE (you still have HTTP third-party protection)
View attachment 215430