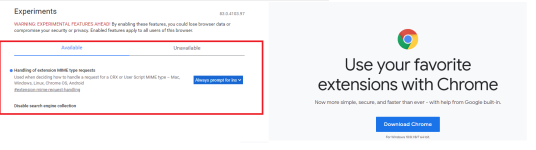
I am using ungoogled chromium as my hardened browser (using Edge as main browser to visit bookmarked websites). I am using Marmaduke's ungoogled version from Woolyss because it updates faster. I download extensions from hxxp://crxextractor.com/ I have no search engine in the taskbar. Together with the 'Auto history delete' extension this gives me a clean new tab page after every restart of ungoogled chrome.
Because I have "Validate Admin Signatures" to block UAC elevation of unsigned binaries, Chromium (like edge with flag de-elevate on launch) also runs in a standard user container (Chromium's chrome.exe is unsigned).
I have all settings to off (except showing home page button with startpage.com search engine) and all site permissions to block except:
- cookies: default allow, block third-party cookies
- images: default allow
- sound: default allow
- javascript: default allow, specifically block HTTP://* and [*.]startpage.com (does not show ads on startpage search results)
I run ublockOrigin in easy medium mode, meaning I only allow safe third-party content from HTTP (insecure) websites plus third-party scripts and frames from top level domains I normally visit (whitelisted: com, nl, uk, net, org, io) and explicitely block all some much abused TopLevelDomains.
My Rules
no-cosmetic-filtering: * true
no-csp-reports: * true
* * 3p-frame block
* * 3p-script block
* com * noop
* net * noop
* io * noop
* nl * noop
* org * noop
* uk * noop
My Filters
! Block plugin objects (e.f. flash) and (hyperling auditing & sending beacons) pings
||*$object,ping
! Block insecure third-party content except stylesheet, image and media
||HTTP://*$third-party,~stylesheet,~image,~media
! Block all on much abused generic TLD's
||*.bid^$all
||*.buzz^$all
||*.club^$all
||*.country^$all
||*.date^$all
||*.download^$all
||*.fun^$all
||*.gdn^$all
||*.host^$all
||*.icu^$all
||*.jetz^$all
||*.kim^$all
||*.loan^$all
||*.men^$all
||*.mobi^$all
||*.mom^$all
||*.party^$all
||*.pics^$all
||*.racing^$all
||*.ren^$all
||*.rest^$all
||*.review^$all
||*.ryukyu^$all
||*.science^$all
||*.shop^$all
||*.site^$all
||*.stream^$all
||*.top^$all
||*.trade^$all
||*.vip^$all
||*.wang^$all
||*.win^$all
||*.work^$all
||*.xin^$all
!
! Block all on much abused country code TLD's. (apologize when your country is mentioned here)
||*.am^$all
||*.cc^$all
||*.cf^$all
||*.cn^$all
||*.fm^$all
||*.ga^$all
||*.gg^$all
||*.ir^$all
||*.ki^$all
||*.kp^$all
||*.la^$all
||*.ml^$all
||*.pw^$all
||*.ru^$all
||*.tk^$all
||*.ua^$all
||*.ug^$all
||*.vn^$all
UBlock blocking a top level domain from VX-Vault
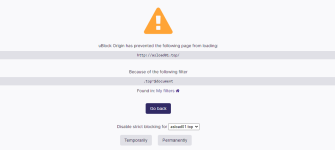
Because first party is always allowed on HTTPS, even a website with an suffix which I have not whitelisted for easy-medium mode (e.g. hardware.INFO) works well with above rules
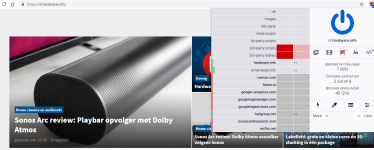
Note: When you google for most high level country domains or top levels domains with most malware, phishing, spam, etc be sure to exclude the countries you visit a lot (e.g. The Netherlands is on third spot of bot net command & control servers, since I am from the Netherlands it is not a good idea to add the reule ||*.NL$all since that woudl block Dutch websites)
(source Spamhouse)