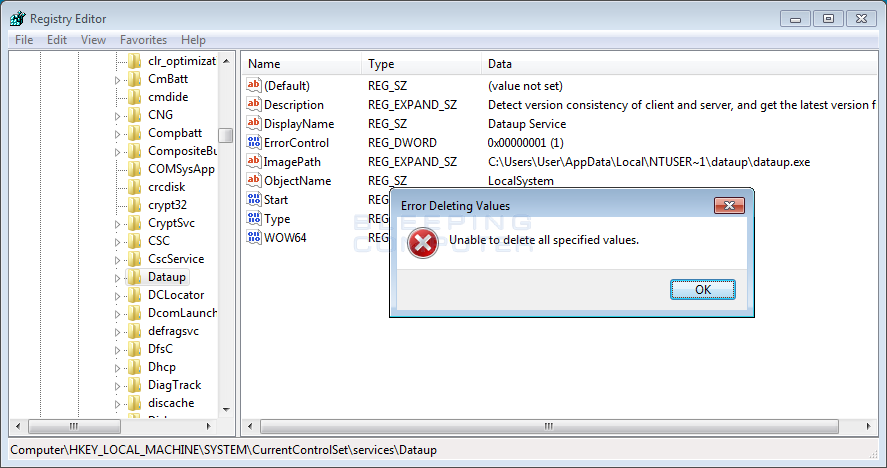
One of my kids downloading something and what it did was open multiple instances of fake programs to eat up memory. Also, it's currently blocking chrome from working and not allowing me to open any antivirus or malware protection and in most cases also not letting me even install the programs. I was able to find and delete most of the fake programs. Not sure if their are any more, but there's still something in the system that's making the system not act right. Also it's adding data to a drive partition to a drive that's segmented for computer recovery. Also the only time chrome will work is when it's hijacked by a fake chrome exe file.
Virus that's blocking anti-malware and antivirus from loading.
- Thread starter MoeB74
- Start date



:max_bytes(150000):strip_icc()/advanced-boot-options-5c757354c9e77c0001f57ae1.jpg)