Yeah, Trooper is right, it is one license per computer.I asked on a different forum, but I'll ask here as well. I just looked on the Voodooshield website and could not locate the answer there. Does a VS Pro license work on only 1 PC or can you use it on multiple PC's assuming you own several PC's?
New Update VoodooShield CyberLock 7.0
- Thread starter danb
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Mail from @danb :
Hey Guys!
We have released the new version of VS to the public and have updated the website.
VS 7.08
https://voodooshield.com/Download/InstallVoodooShield.exe
SHA-256: 57727df43b8a47878423e8f4db9df6785069a2c16441e602195a9b041b71203d
Thank you guys,
Dan
I still have the free version VS 7.06. I'm not updating for the time being
Courtesy of danb
I am using the Pro version
I am using the Pro version
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Mail from @danb :
Hey Guys,
A couple users reported an error in VS’s registration / trial when the computer booted and there was not yet an internet connection. This version fixes this issue in a couple of ways, and also does not check the registration until 3 minutes after VS has started. If anyone had this issue, please try this version and let me know if it is fixed for you or not.
VS 7.09
https://voodooshield.com/Download/InstallVoodooShield709.exe
SHA-256: 2e3886e7a60e3d74b7741c84f80781909bb87beb82b60db983998b75745f6e4c
Thank you guys!
Dan
- Oct 25, 2014
- 2,636
- 7,291
- 3,588
- 40
And now Voodooshield 7.10 is out now
 voodooshield.com
voodooshield.com
With best Regards
Mops21
CyberLock - Automated and Effortless Zero-Trust Endpoint Protection
With best Regards
Mops21
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Thanks @Mops21And now Voodooshield 7.10 is out now
CyberLock - Automated and Effortless Zero-Trust Endpoint Protection
voodooshield.com
With best Regards
Mops21
Sent a mail to @danb asking for a changelog.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
An answer from @danb :
Besides the registration fix, there were a few insignificant WLC changes, but other than that it is the same as 7.09.
I was going to email the beta test group at some point, but I didn’t want to keep spamming their inbox.
Thank you,
Dan
@danb
Could you please consider to add the ability to auto-check on VT when a new popup appears and show the result in the popup?
This feature could be added as well as an aditional step in the rules section, for example.
If AI score < 10 then ok
If 20 > AI score >10 then check on VT
If AI score > 20 then bad
For this maybe each user should use its public API key which gives 4 queries per minute which is more than enough for this use case.
Could you please consider to add the ability to auto-check on VT when a new popup appears and show the result in the popup?
This feature could be added as well as an aditional step in the rules section, for example.
If AI score < 10 then ok
If 20 > AI score >10 then check on VT
If AI score > 20 then bad
For this maybe each user should use its public API key which gives 4 queries per minute which is more than enough for this use case.
@danb VS 7.10, Autopilot Aggressive. Happens after every reboot (atleast as long as I click block is my guess).
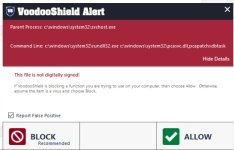

I just allowed this file as it is part of windows and the problem went away.@danb VS 7.10, Autopilot Aggressive. Happens after every reboot (atleast as long as I click block is my guess).
View attachment 266969
Thanks for the informationI just allowed this file as it is part of windows and the problem went away.
If I'm using software with a very small userbase I understand prompts but for stuff that's "part of windows" I hope for less (no) prompts to be honest.
Hey Guys,
Here is the latest version of VS.
There was a conflict between Microsoft Edge's Startup boost (Settings / System and Performance tab) and VS, but the issue is now resolved.
The cool thing is that VS's multithreading is a lot quicker and robust now.
A couple other optimizations are included as well.
VS 7.11
SHA-256: a4ca56e6f0680fca726aff758e215aca12d7bda955cd54ab6bde90c499a8b42b
I am going to wait a little while before releasing this version to the public, but it should be stable, and you can install over the top.
BTW, I will catch up on all of the posts I missed asap.
Have a great weekend!
Thank you,
Dan
Here is the latest version of VS.
There was a conflict between Microsoft Edge's Startup boost (Settings / System and Performance tab) and VS, but the issue is now resolved.
The cool thing is that VS's multithreading is a lot quicker and robust now.
A couple other optimizations are included as well.
VS 7.11
SHA-256: a4ca56e6f0680fca726aff758e215aca12d7bda955cd54ab6bde90c499a8b42b
I am going to wait a little while before releasing this version to the public, but it should be stable, and you can install over the top.
BTW, I will catch up on all of the posts I missed asap.
Have a great weekend!
Thank you,
Dan
Hey Guys,
Sorry to bug you, but I just found a bug in 7.11 that is causing VS to write a lot of entries to the C:\ProgramData\VoodooShield\DeveloperServiceLog.log file. So please check the C:\ProgramData\VoodooShield\ directory for extra DeveloperServiceLog.log files, and delete the extra ones (they end in a number).
And for now please install 7.10.
Sorry about that, I will have it fixed this weekend.
Thank you,
Dan
Sorry to bug you, but I just found a bug in 7.11 that is causing VS to write a lot of entries to the C:\ProgramData\VoodooShield\DeveloperServiceLog.log file. So please check the C:\ProgramData\VoodooShield\ directory for extra DeveloperServiceLog.log files, and delete the extra ones (they end in a number).
And for now please install 7.10.
Sorry about that, I will have it fixed this weekend.
Thank you,
Dan
Hey Guys,
Here is the latest version of VS. It should be completely stable, but please keep in mind there were a lot of changes under the hood, so if you notice anything that is not quite right, please let me know.
I really will catch up on the posts asap, sorry for the delay.
VS 7.12
SHA-256: c72790a9ef1a7a59938e25b3c6c8e1829d1326a7940d1ddddfc0062f09650b3e
Here is the latest version of VS. It should be completely stable, but please keep in mind there were a lot of changes under the hood, so if you notice anything that is not quite right, please let me know.
I really will catch up on the posts asap, sorry for the delay.
VS 7.12
SHA-256: c72790a9ef1a7a59938e25b3c6c8e1829d1326a7940d1ddddfc0062f09650b3e
VS 7.10 here. I did a rightclick and "VS Scan" on the drivers for my keyboard before install. Two mins later still no result so I checked them with VT (clean).
Then I wanted to install them with VS on Autopilot/Agressive. During the install I got two prompts for other exes which both VS couldn't decide on also within two mins each (no VS or WLC results within two mins). So I used VT again both times. So for all three exes I had to use VT since VS couldn't decide at all.
Logitech Gaming Software (driver download)
Since it is a signed driver from logitech I had expected VS wouldn't give me a "blank result" time installing. Internet had to be working because VT worked.
Then I wanted to install them with VS on Autopilot/Agressive. During the install I got two prompts for other exes which both VS couldn't decide on also within two mins each (no VS or WLC results within two mins). So I used VT again both times. So for all three exes I had to use VT since VS couldn't decide at all.
Logitech Gaming Software (driver download)
Since it is a signed driver from logitech I had expected VS wouldn't give me a "blank result" time installing. Internet had to be working because VT worked.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Mail from @danb :
Hey Guys,
Just a quick note… we just released 7.12 to the public.
We also just finished upgrading the WLC servers, so they should a lot faster now.
Have a great weekend!
Thank you,
Dan
Hey Guys!
Here is the latest version of VS, it should be perfectly stable.
When testing Follina, I discovered a bug in VS’s command lines when I did a repair install of Office 2013. It had nothing to do with Follina, but it was a very odd bug that had never been reported before. Basically, VS was unable to parse one of the command lines of the Office 2013 repair, so it created an exception. Anyway, that is fixed now, and I am assuming that if anyone had any issues with command lines in the last couple of years, that the issue is fixed now.
The Follina tests went great, and VS properly blocked the exploit with its Antimalware Contextual Engine / Anti-Exploit mechanism (as opposed to blocking the command line). It is okay to block exploits via suspicious command lines, but the only problem is that if there is not a rule for a certain suspicious command line, then there will be a bypass. This is why we prefer blocking by the Anti-Exploit mechanism, you are pretty much 100% certain it is going to block the attack.
But I did find two optimizations that I implemented in 7.13. First, when VS was OFF, it did not block Follina. This could go either way, simply because when the user downloads the exploit, they will either be running a web browser or email client. But just to be sure, VS now blocks exploits when it is OFF. And actually, before the Antimalware Contextual Engine, VS did block potential exploits even when it was OFF. I just never got around to implementing the potential exploit feature into the Antimalware Contextual Engine. The other change I made is that now when VS blocks a potential exploit, it will show the appropriate user prompt that does not provide VoodooAi or WhitelistCloud verdicts. Again, this is how VS used to work as well, and the reason we do not want to provide VoodooAi or WhitelistCloud verdicts is, for example, if VS blocks calc.exe via a potential exploit, then the VoodooAi or WhitelistCloud verdicts will both be Safe, making the user think that it is okay to allow.
There were a few other small optimizations as well.
VS 7.13
SHA-256: 576280b93a4d9d40309586d688e539d84c9437fc4670770716221947a509387c
Thank you,
Dan
Here is the latest version of VS, it should be perfectly stable.
When testing Follina, I discovered a bug in VS’s command lines when I did a repair install of Office 2013. It had nothing to do with Follina, but it was a very odd bug that had never been reported before. Basically, VS was unable to parse one of the command lines of the Office 2013 repair, so it created an exception. Anyway, that is fixed now, and I am assuming that if anyone had any issues with command lines in the last couple of years, that the issue is fixed now.
The Follina tests went great, and VS properly blocked the exploit with its Antimalware Contextual Engine / Anti-Exploit mechanism (as opposed to blocking the command line). It is okay to block exploits via suspicious command lines, but the only problem is that if there is not a rule for a certain suspicious command line, then there will be a bypass. This is why we prefer blocking by the Anti-Exploit mechanism, you are pretty much 100% certain it is going to block the attack.
But I did find two optimizations that I implemented in 7.13. First, when VS was OFF, it did not block Follina. This could go either way, simply because when the user downloads the exploit, they will either be running a web browser or email client. But just to be sure, VS now blocks exploits when it is OFF. And actually, before the Antimalware Contextual Engine, VS did block potential exploits even when it was OFF. I just never got around to implementing the potential exploit feature into the Antimalware Contextual Engine. The other change I made is that now when VS blocks a potential exploit, it will show the appropriate user prompt that does not provide VoodooAi or WhitelistCloud verdicts. Again, this is how VS used to work as well, and the reason we do not want to provide VoodooAi or WhitelistCloud verdicts is, for example, if VS blocks calc.exe via a potential exploit, then the VoodooAi or WhitelistCloud verdicts will both be Safe, making the user think that it is okay to allow.
There were a few other small optimizations as well.
VS 7.13
SHA-256: 576280b93a4d9d40309586d688e539d84c9437fc4670770716221947a509387c
Thank you,
Dan
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Had a command line block with VS 7.13:
Is this okay, to allow ?
Code:
rundll32.exe c:\windows\system32\davclnt.dll,davsetcookie localhost http://localhost/d%24/onedrive/documentenGandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Answer from @danb by mail:Had a command line block with VS 7.13:
Is this okay, to allow ?Code:rundll32.exe c:\windows\system32\davclnt.dll,davsetcookie localhost http://localhost/d%24/onedrive/documenten
Yeah, that is okay to allow, I will have to fix that.
You may also like...
-
-
App Review Old Norton vs New Norton - Engine Comparatif
- Started by Shadowra
- Replies: 51
-
-
SOpera One R3 arrives with new AI, Google integrations, and more
- Started by Santiago Benavides García
- Replies: 0