No. Normally the files without MOTW and not executed are checked only by offline Defender features. When the file has got MOTW or has been executed (and recognized as suspicious), it is checked against the cloud backend.
Advice Request Windows Defender disabled by malware
- Thread starter Templarware
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
Microsoft recomends the below settings for the "Block at first sight" feature:
- Cloud-delivered protection: Enabled (required)
- File Blocking Level: High (recommended)
- Time extension for file scanning by the cloud: 50 (recommended)
- Prompt users before sample submission: Send all data without prompting (recommended)
Microsoft recomends the below settings for the "Block at first sight" feature:
The last three settings do matter for files unknown in the Microsoft cloud. The lower settings can lower the detection.
- Cloud-delivered protection: Enabled (required)
- File Blocking Level: High (recommended)
- Time extension for file scanning by the cloud: 50 (recommended)
- Prompt users before sample submission: Send all data without prompting (recommended)
Thank you Andy for all your efforts. Much appreciated!
Today, one variant of the POC has been blocked (for the first time) by the Defender ASR rule "Use advanced protection against ransomware" - not blocked on Defender's default settings. Of course, all variants with UAC bypass were also blocked from the beginning by the ASR rule "Block executable files from running unless they meet a prevalence, age, or trusted list criteria".Defender is still learning. I can see two new detections that now block the attack (POC worked well yesterday):
Trojan:Win32/Hynamer.A!ml
Trojan:Win32/MereTam.A
I did no submit the POC to Microsoft, so it is based on Defender's ML.
The first detection (behavior-based) is somehow related to my UAC bypass, but I am not sure if it can fully stop it. We will see after some testing.
Edit.
This anti-ransomware ASR rule blocks my UAC bypass (nice job Defender).
So, it must be modified again to bypass also ASR.
Last edited:
Have you noticed that the Windows Defender Browser Protection extension doesn't get updated since june 2020, and it says "currently supported regions: United States"?
MS little projects, they finish before they even start. At that time the team probably did not know, that Edge will be able to incorporate smartscreen, so no 3rd party extension needed.Windows Defender Browser Protection extension
But still, how would it only support United States?MS little projects, they finish before they even start. At that time the team probably did not know, that Edge will be able to incorporate smartscreen, so no 3rd party extension needed.
It does work outside of the US. The extension uses the cloud (in the background) for updates/checks, and it doesn't require constant extension updates to "make it effective".Have you noticed that the Windows Defender Browser Protection extension doesn't get updated since june 2020, and it says "currently supported regions: United States"?
If using Microsoft Edge:
Turn off SmartScreen in Edge settings
For other Chromium-based browsers:
Install Microsoft Defender Browser Protection
Visit test site: Microsoft Defender Browser Protection
The results are the exactly the same as Edge with built-in SmartScreen enabled.
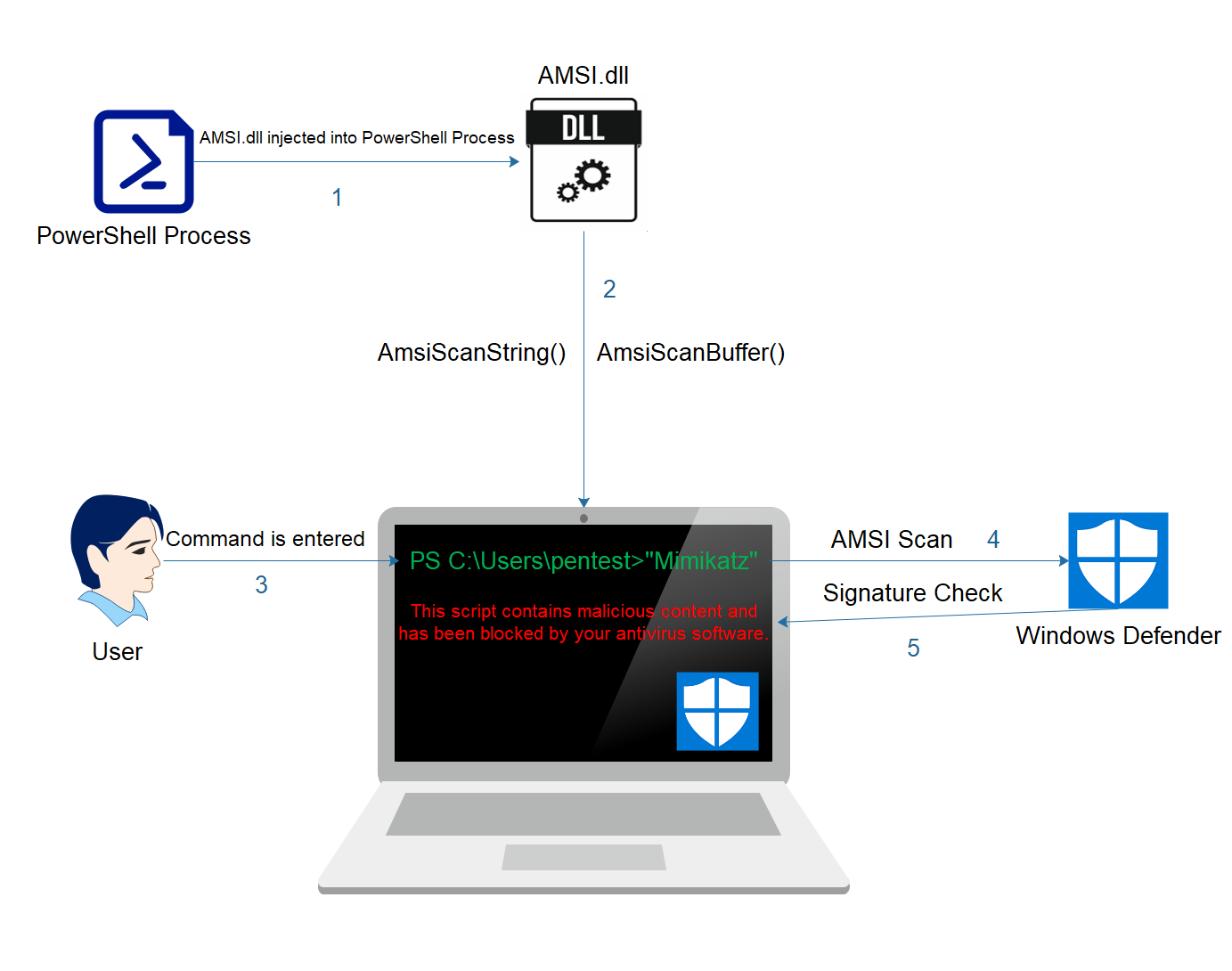
AMSI Bypass Methods
Microsoft has developed AMSI (Antimalware Scan Interface) as a method to defend against common malware execution and protect the end user. By default windows defender interacts with the AMSI API to…
Some bypasses are blocked by Defender (mostly from point 4), but the rest works (I did not test DLL hijacking).
AMSI Bypass Methods
Microsoft has developed AMSI (Antimalware Scan Interface) as a method to defend against common malware execution and protect the end user. By default windows defender interacts with the AMSI API to…pentestlaboratories.com
All bypasses performed via PowerShell in this article are blocked when using PowerShell in Constrained Language Mode.
How to do it though, when I tried this command, it no longer works.Some bypasses are blocked by Defender (mostly from point 4), but the rest works (I did not test DLL hijacking).
All bypasses performed via PowerShell in this article are blocked when using PowerShell in Constrained Language Mode.
Code:
%WINDIR%\System32\WindowsPowerShell\v1.0\powershell.exe "Set-ExecutionPolicy bypass - noprofile"
Code:
reg add "HKLM\Software\Microsoft\PowerShell\1\ShellIds\ScriptedDiagnostics" /v "ExecutionPolicy" /t REG_SZ /d "Restricted" /f
reg add "HKLM\Software\WOW6432Node\Microsoft\PowerShell\1\ShellIds\ScriptedDiagnostics" /v "ExecutionPolicy" /t REG_SZ /d "Restricted" /f
reg add "HKLM\Software\Policies\Microsoft\Windows\PowerShell" /v "EnableScripts" /t REG_DWORD /d "0" /f
reg add "HKLM\System\CurrentControlSet\Control\Session Manager\Environment" /v "__PSLockDownPolicy" /t REG_SZ /d "4" /fI did it as follows:How to do it though, when I tried this command, it no longer works.
- Run PowerShell console and execute the command:
Invoke-MimiKatz - The command should trigger the red alert:
"This script contains malicious content and has been blocked by your antivirus software."
This is a sign that AMSI works. - Copy/paste the content of any script with AMSI bypass to the PowerShell console and try to execute it. You will see the red alert related to Constrained Language Mode:
"Cannot invoke method. Method invocation is supported only on core types in this language mode." - If you see the alert from point 2 instead, then it is a sign that the code from AMSI bypass was detected by Defender. If you will disable the Defender real-time protection, then you will see the alert from the point 3.
Last edited:
Here is an example of rare malware that was not created directly for profit but was intended to destroy the victims' systems (Iranian trains). The attack was directed against the Iranian government.
The attackers managed to obtain high privileges on the victim's domain server, placed there a batch file (setup.bat), and created a task scheduler by Group Policy to execute this file. The original article about this attack can be found on the Padvish Malware Threats Database (Iranian AV):
https://threats.amnpardaz.com/malware/trojan-win32-breakwin/
https://labs.sentinelone.com/meteor...per-paralyzes-iranian-trains-with-epic-troll/
https://malwaretips.com/threads/new...alware-used-in-iranian-railway-attack.109331/
On this infection stage, the attackers could disable Defender, but they choose another way:
It is worth mentioning that the attackers invalidated Defender after compromising the server, so the network was already seriously compromised (probably via lateral movement).
The attackers managed to obtain high privileges on the victim's domain server, placed there a batch file (setup.bat), and created a task scheduler by Group Policy to execute this file. The original article about this attack can be found on the Padvish Malware Threats Database (Iranian AV):

https://threats.amnpardaz.com/malware/trojan-win32-breakwin/
https://labs.sentinelone.com/meteor...per-paralyzes-iranian-trains-with-epic-troll/
https://malwaretips.com/threads/new...alware-used-in-iranian-railway-attack.109331/
On this infection stage, the attackers could disable Defender, but they choose another way:
- Disabled network and logged off from Active Directory.
- Added Windows Defender exclusions to prevent the malware from being detected.
It is worth mentioning that the attackers invalidated Defender after compromising the server, so the network was already seriously compromised (probably via lateral movement).
Last edited by a moderator:
Today, one variant of the POC has been blocked (for the first time) by the Defender ASR rule "Use advanced protection against ransomware" - not blocked on Defender's default settings. Of course, all variants with UAC bypass were also blocked from the beginning by the ASR rule "Block executable files from running unless they meet a prevalence, age, or trusted list criteria".
Edit.
This anti-ransomware ASR rule blocks my UAC bypass (nice job Defender).
So, it must be modified again to bypass also ASR.
Finally, the author of Defender Control removed the CmdLine support. So, the new version of Defender Control cannot be used in my POC (or similar attack) to silently disable Defender on default settings (UAC bypassed) and infect the computer with any (even very old malware).
This is good news because, in my opinion, the response of Microsoft to this threat was not sufficient, even after submitting the POCs several times.
You may also like...
-
New Update Microsoft removing Defender Application Guard from Office
- Started by Parkinsond
- Replies: 1
-
Help Needed: Suspicious Activity & Possible Malware on Windows 10 PC
- Started by Thomas Ellias
- Replies: 4
-
-
Malware News New Multi-Stage Windows Malware Disables Microsoft Defender Before Dropping Malicious Payloads
- Started by Brownie2019
- Replies: 6
