Yes, in the home environment (against widespread attacks). It can be partially done in businesses by reducing the attack surface. But, the larger/complex the local network (and Internet integration) the bigger are chances of breaches. Nowadays, one has to accept the Zero Trust security model, which assumes that the Enterprise can be compromised. But anyway, the security has to quickly identify the breach, prevent lateral movement and data leak.From what I typically read in malware analysis reports, the malware usually lands in user space, so wouldn't a properly configured HIPS or other such system hardening tool prevent the malware from launching and subsequently gaining elevated permissions?
Advice Request Windows Defender disabled by malware
- Thread starter Templarware
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
UserSpace is still protected in Recommended_Settings. The exceptions are two hidden folders (ProgramData and AppData). Normally, the EXE (TMP) and MSI files from the Internet can land there via drive-by downloads (when web browsing), opening these files directly from the email client, opening these files directly via archiver application (7-Zip, Winzip, WinRar, etc.), or exploiting some application. The first three are protected in Recommended_Settings, too (SmartScreen Application Reputation, <Harden Archivers>, <Harden Email Clients>). Anyway, If there is a fair possibility of exploiting then "Windows_*_Strict_Recommended_Settings can be useful.Would there be benefit in switching to If the user switches to profile "Windows_*_Strict_Recommended_Settings.hdc" to block also EXE (TMP) and MSI files in UserSpace? @Andy Ful
Generally, using the more and more restricted system always can add some protection. But usually, this covers the malware which will probably never happen on your computer. If you want to add something to Recommended_Settings then you have to be sure that it is necessary for some reason.
Last edited:
Either I am blind or nobody is mentioning the option to run MD in a sandbox... Wouldn't that be the best option to ensure Defender isn't getting disabled by malware?
Thanks Andy. Was just checking if it would help prevent WD being disabled since there was mention of the executable in the userspace in previous posts on this topic. I'm protected enough with the default recommended settings, I'll stick with those.UserSpace is still protected in Recommended_Settings. The exceptions are two hidden folders (ProgramData and AppData). Normally, the EXE (TMP) and MSI files from the Internet can land there via drive-by downloads (when web browsing), opening these files directly from the email client, opening these files directly via archiver application (7-Zip, Winzip, WinRar, etc.), or exploiting some application. The first three are protected in Recommended_Settings, too (SmartScreen Application Reputation, <Harden Archivers>, <Harden Email Clients>). Anyway, If there is a fair possibility of exploiting then "Windows_*_Strict_Recommended_Settings can be useful.
Generally, using the more and more restricted system always can add some protection. But usually, this covers the malware which will probably never happen on your computer. If you want to add something to Recommended_Settings then you have to be sure that it is necessary for some reason.
Either I am blind or nobody is mentioning the option to run MD in a sandbox... Wouldn't that be the best option to ensure Defender isn't getting disabled by malware?
I was wondering the same thing.
My tests were already done with enabled Defender Sandbox.Either I am blind or nobody is mentioning the option to run MD in a sandbox... Wouldn't that be the best option to ensure Defender isn't getting disabled by malware?
Last edited:
Defender is still learning. I can see two new detections that now block the attack (POC worked well yesterday):...
I did not submit the POC with UAC bypass yet. I am curious if Microsoft will be able to recognize from telemetry that something successfully bypasses UAC to disable Defender (it would be welcome). Usually, such bypasses are not urgent to Microsoft.
Trojan:Win32/Hynamer.A!ml
Trojan:Win32/MereTam.A
I did no submit the POC to Microsoft, so it is based on Defender's ML.
The first detection (behavior-based) is somehow related to my UAC bypass, but I am not sure if it can fully stop it. We will see after some testing.
Where to enable Sandobx in settings? And how does it affect performance?

Run Windows Defender inside a sandbox - Xenit
Last week Microsoft released the news that they have added a new feature to Windows Defender Antivirus. The new feature allows Windows Defender Antivirus to run within a sandbox.
 xenit.se
xenit.se
Never really used MD so I can't answer your second question.
F
ForgottenSeer 85179
I don't see any differences since long time usage.And how does it affect performance?
@Templarware
if you have Process Explorer installed in place of Task manager, you can see if Defender is sandboxed by opening it as Administrator, then you should see the MsMpEngCP.exe process running with integrity: AppContainer.
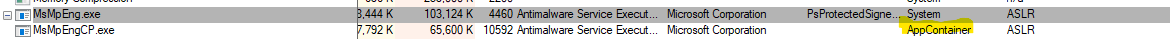
if you have Process Explorer installed in place of Task manager, you can see if Defender is sandboxed by opening it as Administrator, then you should see the MsMpEngCP.exe process running with integrity: AppContainer.
The container process uses abot 60 megs of RAM but it's not really showed any perfomance impact on my old laptop.Where to enable Sandobx in settings? And how does it affect performance?
So, in 2021 we need to run a CMD command to activate an important AV feature?
Run Windows Defender inside a sandbox - Xenit
Last week Microsoft released the news that they have added a new feature to Windows Defender Antivirus. The new feature allows Windows Defender Antivirus to run within a sandbox.xenit.se
Never really used MD so I can't answer your second question.
Why isn't this in the security settings? Same could be said for MAPS...
Well, I can't answer that question either...So, in 2021 we need to run a CMD command to activate an important AV feature?
Why isn't this in the security settings? Same could be said for MAPS...
Read all replies and didn't learn a thing, I am fine with disabling WD manually via group policy whenever i would need that, but as for speaking that malware can do that, safe and aware computer users, especially participants in security forums are most likely to never encounter such malware at all, if any. I know that some of you run on-demand scanners daily just for "safety", but it has nothing to do with safety, it's called a security software addiction which can be seen clearly when arguing. Learn and study the operating system you are using, not the additional software to manage it.
So, in 2021 we need to run a CMD command to activate an important AV feature?
Why isn't this in the security settings? Same could be said for MAPS...
Defender sandbox is not an important security feature and Defender has already its cloud submit feature enabled by default. Though, in both cases it sends the file only if it has MOTW tag.
Cloud delivered protection works also for files without MOTW if these files are executed (and are recognized as suspicious). The MOTW is necessary for the "Block at first sight" feature, which works on access for all files with MOTW (does not require file execution).Defender sandbox is not an important security feature and Defender has already its cloud submit feature enabled by default. Though, in both cases it sends the file only if it has MOTW tag.
I think malware or even legit programs adding themselves into the exclusions is another unsettling thing. If you install McAfee then for some reason McAfee put itself into Microsoft Defender's exclusions. A year ago when I installed Acronis True Image, it put itself into Defender's exclusion which I discovered 4-5 days later after I uninstalled the program. Both required admin rights but when trusted programs ask for that while installing then surely we will allow that.
I also found a malware today which added something to Defender's exclusion while it was executed. The sample is at least 10 days old and the payload is detected by every AV, so Defender also detected and removed it, but the exclusions remained. The malware is a combination of 4 files. One .bat, two .dat, one .dll.
Interestingly the exclusion was not for any files, instead the Defender UI was showing file type, "exe" and "dat" into the exclusion.
Microsoft makes it easy to manage it via registry modification, powershell, group policy etc. for ease of use I assume.
One of the plus point of Microsoft Defender is that it's very much integrated into the system, but this plus point is also one of its main weak point. Adding exclusions shouldn't be so easy.
I never encounter any malware in my real world usage so Defender is more than enough for me, but I hope Microsoft do something in the future to counter these issues.
I also found a malware today which added something to Defender's exclusion while it was executed. The sample is at least 10 days old and the payload is detected by every AV, so Defender also detected and removed it, but the exclusions remained. The malware is a combination of 4 files. One .bat, two .dat, one .dll.
Interestingly the exclusion was not for any files, instead the Defender UI was showing file type, "exe" and "dat" into the exclusion.
Microsoft makes it easy to manage it via registry modification, powershell, group policy etc. for ease of use I assume.
One of the plus point of Microsoft Defender is that it's very much integrated into the system, but this plus point is also one of its main weak point. Adding exclusions shouldn't be so easy.
I never encounter any malware in my real world usage so Defender is more than enough for me, but I hope Microsoft do something in the future to counter these issues.
F
ForgottenSeer 85179
Why did you say that? It harden Defender against manipulation and increase his security.Defender sandbox is not an important security feature
This is done intentionally, to prevent changes made by home users. It is a somewhat strange point of view, but it is fully consistent with Microsoft's security philosophy. If Defender Sandbox will work without any issues then it will be integrated with Security Center.So, in 2021 we need to run a CMD command to activate an important AV feature?
Why isn't this in the security settings? Same could be said for MAPS...
So MOTW only matters in the step 6?Cloud delivered protection works also for files without MOTW if these files are executed (and are recognized as suspicious). The MOTW is necessary for the "Block at first sight" feature, which works on access for all files with MOTW (does not require file execution).
I'm guessing that any exploit advanced enough to leverage the AV engine itself would rather be used in the targeted attacks. This is just not in my threat model. But still I keep it enabled as it doesn't cause any harm.Why did you say that? It harden Defender against manipulation and increase his security.
By the manipulation if you meant scripts, I never heard that sandboxing would prevent such scenario.
You may also like...
-
New Update Microsoft removing Defender Application Guard from Office
- Started by Parkinsond
- Replies: 1
-
Help Needed: Suspicious Activity & Possible Malware on Windows 10 PC
- Started by Thomas Ellias
- Replies: 4
-
-
Malware News New Multi-Stage Windows Malware Disables Microsoft Defender Before Dropping Malicious Payloads
- Started by Brownie2019
- Replies: 6

