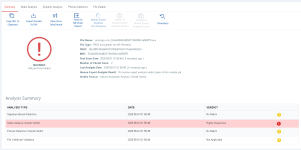
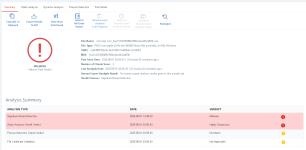
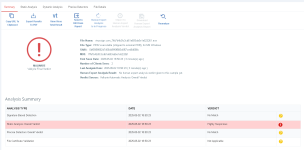
It is detected by Dynamic Analysis as Highly Suspicious(Xcitiums way of saying that is Malicious)
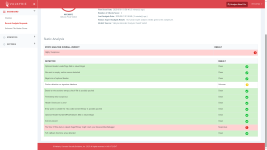
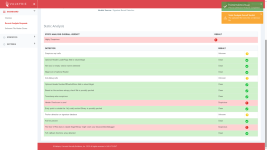
The dynamic analysis identified 3 behaviours, none of which is a clear sign of malicious intent.
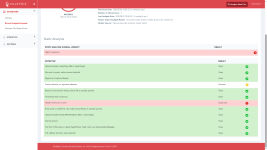
| Opens a file in a system directory | |
| Uses a function clandestinely | |
| Has no visible windows | |
Opens a file in system directory — the file is
C:\Windows\Microsoft.NET\Framework\v2.0.50727\config\machine.config (from the report).
This file contains system defaults, assembly binding rules, remote channels and cryptography settings amongst others. The file was just read and not modified.
Plenty of .net-based applications have valid reasons to read machine defaults.
In addition, the execution flow might contain variables that require the .net framework to read this file, so it may not be the application itself using this information — it could just be side effect of the programmer’s logic.
Uses a function
CLANDESTINELY.
There is no information what exactly is used clandestinely. Unable to comment here.
Has no visible window:
This could be a sign of a threat, specifically when file is downloaded from the web. However, the file contains strings like “Установка” (installation in Russian), “Далее” (which means next) and so on. The file is designed to
have a visible window, it’s just Comodo emulation was unable to fully cover virtual artefacts and the program terminated.
The program is also 12 years old and as stated earlier, will not work anymore.
All in all, very little, almost no behaviour was observed during Comodo emulation process to conclude whether or not the program is malicious in an efficient and accurate way. The program merely detected emulation and exited, which is typical for cracks, hacking tools, password brute-forcing tools and so on, as well as for malware. It is also typical for some fully legit packing tools and install builders.