Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,114
AVLab tested 1456 malware samples from honeypots around the world and some publicly available malware resources (data for one month in July 2020).
The tested products:
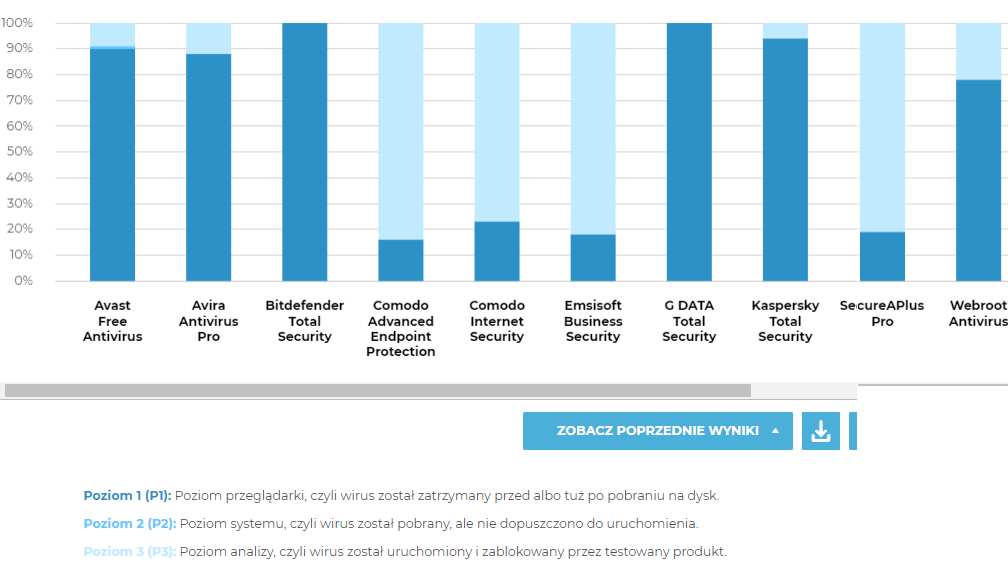
P1 - sample stopped by the web browser or automatically after it was downloaded to disk.
P2 - sample was not detected after download but the execution was blocked.
P3 - sample blocked after being executed.
Such products like Comodo, Emsisoft, and Securea blocked most malware on execution (P3 level). Other products were blocked most samples on the P1 level. Only a very small number of samples were stopped on the P2 level (about 1% for Avast).
The tests were conducted on Windows 10 Pro x64. Due to the testing procedure, the malware samples were tested with some delay (one day or more) which was necessary to download the files from honeypots and make the initial analysis.
The AVLab testing procedure does not test URLs. Although Chrome was used, the samples were not downloaded from original URLs, but from random URLs generated by the local server DNS and HTTP/S. As we can see this did not decrease the protection against the tested samples.
It is probable, that the delay between the file landing in honeypot and the moment of testing against AVs caused the excellent protection of tested products.
Edit1.
Added source links.
https://checklab.pl/en/recent-results
https://checklab.pl/en/publications...ing-checklab-website-dedicated-security-tests
https://checklab.pl/en/methodology
Edit2
There is an inconsistency in the presented results. The Polish article shows that Avira and Webroot missed one sample. The charts (Polish and English versions) show that these AVs did not miss any malware.
The tested products:
- Avast Free Antivirus
- Bitdefender Total Security
- Comodo Advanced Endpoint Protection
- Comodo Internet Security
- Emsisoft Business Security
- G Data Total Security
- Kaspersky Total Security
- SecureAPlus Pro
- Avira Antivirus Pro (one sample missed ????)
- Webroot Antivirus (one sample missed ????)
P1 - sample stopped by the web browser or automatically after it was downloaded to disk.
P2 - sample was not detected after download but the execution was blocked.
P3 - sample blocked after being executed.
Such products like Comodo, Emsisoft, and Securea blocked most malware on execution (P3 level). Other products were blocked most samples on the P1 level. Only a very small number of samples were stopped on the P2 level (about 1% for Avast).
The tests were conducted on Windows 10 Pro x64. Due to the testing procedure, the malware samples were tested with some delay (one day or more) which was necessary to download the files from honeypots and make the initial analysis.
The AVLab testing procedure does not test URLs. Although Chrome was used, the samples were not downloaded from original URLs, but from random URLs generated by the local server DNS and HTTP/S. As we can see this did not decrease the protection against the tested samples.
It is probable, that the delay between the file landing in honeypot and the moment of testing against AVs caused the excellent protection of tested products.
Edit1.
Added source links.
https://checklab.pl/en/recent-results
https://checklab.pl/en/publications...ing-checklab-website-dedicated-security-tests
https://checklab.pl/en/methodology
Edit2
There is an inconsistency in the presented results. The Polish article shows that Avira and Webroot missed one sample. The charts (Polish and English versions) show that these AVs did not miss any malware.
Last edited: