@Marko :), You get a free legacy plan with a maximum of 3 locations when you create an account with no payment info. The updated free plan provides 50 locations and additional features and requires payment details.
I believe you kept the defaults when creating locations. You can disable IPv4 and IPv6 if you plan to use DoH and DoT. Cloudflare evaluates policies from top to bottom; it applies the first policy a query matches, and evaluation stops.
I suggest using the mrrfv repo; its guide is simple and quicker than using AIs. You can experiment once you get the overall feel of the process.
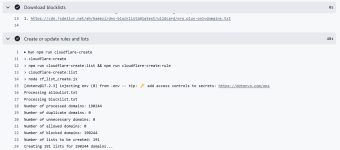
Cloudflare email, API token with Zero Trust read and edit permissions, and account ID.

 github.com
github.com
I believe you kept the defaults when creating locations. You can disable IPv4 and IPv6 if you plan to use DoH and DoT. Cloudflare evaluates policies from top to bottom; it applies the first policy a query matches, and evaluation stops.
I suggest using the mrrfv repo; its guide is simple and quicker than using AIs. You can experiment once you get the overall feel of the process.
Cloudflare email, API token with Zero Trust read and edit permissions, and account ID.
cloudflare-gateway-pihole-scripts/extended_guide.md at main · mrrfv/cloudflare-gateway-pihole-scripts
Use Cloudflare Gateway DNS/VPN to block ads, malware and tracking domains - free alternative to NextDNS, Pi-hole and AdGuard - mrrfv/cloudflare-gateway-pihole-scripts
Running in GitHub Actions
These scripts can be run using GitHub Actions so your filters will be automatically updated and pushed to Cloudflare Gateway. This is useful if you are using a frequently updated blocklist.
Please note that:
- GitHub Actions wasn't intended to be used for this purpose, therefore the local options are recommended.
- the GitHub Action downloads the recommended blocklists and whitelist by default. You can change this behavior by setting Actions variables.
- Create a new empty, private repository. Forking or public repositories are discouraged, but supported - although the script never leaks your API keys and GitHub Actions secrets are automatically redacted from the logs, it's better to be safe than sorry. There is no need to use the "Sync fork" button if you're doing that! The GitHub Action downloads the latest code regardless of what's in your forked repository.
- Create the following GitHub Actions secrets in your repository settings:
- CLOUDFLARE_API_TOKEN: Your Cloudflare API Token with Zero Trust read and edit permissions
- CLOUDFLARE_ACCOUNT_ID: Your Cloudflare account ID
- CLOUDFLARE_LIST_ITEM_LIMIT: The maximum number of blocked domains allowed for your Cloudflare Zero Trust plan. Default to 300,000. Optional if you are using the free plan.
- PING_URL: /Optional/ The HTTP(S) URL to ping (using curl) after the GitHub Action has successfully updated your filters. Useful for monitoring.
- DISCORD_WEBHOOK_URL: /Optional/ The Discord (or similar) webhook URL to send notifications to. Good for monitoring as well.
- Create the following GitHub Actions variables in your repository settings if you desire:
- ALLOWLIST_URLS: Uses your own allowlists. One URL per line. Recommended allowlists will be used if this variable is not provided.
- BLOCKLIST_URLS: Uses your own blocklists. One URL per line. Recommended blocklists will be used if this variable is not provided.
- BLOCK_PAGE_ENABLED: Enable showing block page if host is blocked.
- Create a new file in the repository named .github/workflows/main.yml with the contents of auto_update_github_action.yml found in this repository. The default settings will update your filters every week at 3 AM UTC. You can change this by editing the schedule property.
- Enable GitHub Actions in your repository settings.