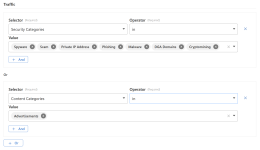
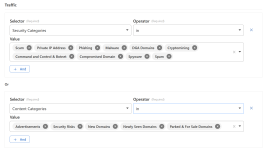
name: Delete File Lists
on:
workflow_dispatch:
inputs:
list_prefix:
description: 'Prefix of lists to delete (e.g., Adblock_)'
required: true
default: 'Adblock_'
type: string
jobs:
lists:
runs-on: ubuntu-latest
steps:
- name: Fetch and Delete Gateway Lists
run: |
PREFIX="${{ github.event.inputs.list_prefix }}"
echo "Target prefix: $PREFIX"
PAGE=1
PER_PAGE=100
while : ; do
echo "Fetching page $PAGE..."
RESPONSE_DATA=$(curl -s -X GET "
https://api.cloudflare.com/client/v4/accounts/${{ secrets.CLOUDFLARE_ACCOUNT_ID }}/gateway/lists?page=$PAGE&per_page=$PER_PAGE" \
-H "Authorization: Bearer ${{ secrets.CLOUDFLARE_API_TOKEN }}" \
-H "Content-Type: application/json")
COUNT=$(echo "$RESPONSE_DATA" | jq '.result | length')
if [ "$COUNT" -eq 0 ]; then
echo "No more lists found."
break
fi
echo "$RESPONSE_DATA" | jq -c --arg PRE "$PREFIX" '.result[] | select(.name | startswith($PRE))' | while read -r list; do
LIST_ID=$(echo "$list" | jq -r '.id')
LIST_NAME=$(echo "$list" | jq -r '.name')
echo "Attempting to delete: $LIST_NAME ($LIST_ID)"
DELETE_RES=$(curl -s -X DELETE "
https://api.cloudflare.com/client/v4/accounts/${{ secrets.CLOUDFLARE_ACCOUNT_ID }}/gateway/lists/$LIST_ID" \
-H "Authorization: Bearer ${{ secrets.CLOUDFLARE_API_TOKEN }}" \
-H "Content-Type: application/json")
if echo "$DELETE_RES" | jq -e '.success' > /dev/null; then
echo "

Successfully deleted $LIST_NAME"
else
ERR=$(echo "$DELETE_RES" | jq -r '.errors[0].message')
echo "

Failed to delete $LIST_NAME: $ERR"
fi
done
# Move to next page
PAGE=$((PAGE + 1))
done