Typically, an attack will operate either through a payload running on the disk, in which case sandbox has you covered, or through a command line interpreter such as powershell, in which case embedded code detection is there to protect you.If an attack use exploit to inject shellcode to an already running process and does not write any payload to files or start any new processes.
Like UIWIX, all code are running in memory.
In this circumstance, can auto-sanbox protect system?
App Review Comodo Firewall 10 Setup
- Thread starter cruelsister
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It is advised to take all reviews with a grain of salt. In extreme cases some reviews use dramatization for entertainment purposes.
But few malwares like UIWIX ransomware neither drop payload into disk nor start any interpreter/process, they just utilize SMB exploit(MS17-010) and inject shellcode into a running system process like LMS.exe and execute.Typically, an attack will operate either through a payload running on the disk, in which case sandbox has you covered, or through a command line interpreter such as powershell, in which case embedded code detection is there to protect you.
I wonder that if we only use auto-sandbox, can auto-sandbox protect system in this circumstance.
The SMB exploit is how the malware spreads laterally in a network, once it has infected one of the computers on the network. It is not the method for infecting the computer.But few malwares like UIWIX ransomware neither drop payload into disk nor start any interpreter/process, they just utilize SMB exploit(MS17-010) and inject shellcode into a running system process like LMS.exe and execute.
I wonder that if we only use auto-sandbox, can auto-sandbox protect system in this circumstance.
Uiwix Ransomware Using EternalBlue SMB Exploit To Infect VictimsThe SMB exploit is how the malware spreads laterally in a network, once it has infected one of the computers on the network. It is not the method for infecting the computer.
Uiwix Ransomware Using EternalBlue SMB Exploit To Infect Victims
Beaumont also reported that when a victim becomes infected with the ransomware, it will not be written to disk. Instead this ransomware will run directly from memory and begin infecting the computer. This makes it difficult for most security programs to properly detect that this program is running and thus prevent it from encrypting a victim's data.
After WannaCry, UIWIX Ransomware and Monero-Mining Malware Follow Suit
After WannaCry, UIWIX Ransomware and Monero-Mining Malware Follow Suit - TrendLabs Security Intelligence Blog
So how is UIWIX different? It appears to be fileless: UIWIX is executed in memory after exploiting EternalBlue. Fileless infections don’t entail writing actual files/components to the computer’s disks, which greatly reduces its footprint and in turn makes detection trickier.
UIWIX Ransomware appears to be fileless and doesnot start any new interpreter/process.
UIWIX sample, dump directly from memory
Antivirus scan for 146581f0b3fbe00026ee3ebe68797b0e57f39d1d8aecc99fdc3290e9cfadc4fc at 2017-05-22 09:19:32 UTC - VirusTotal
Last edited:
Using outbound firewall like, CFW/Zone etc and block. Or disable/remove smb1 , 2 , 3... your PC...
Well, the "worm" behavior, which utilizes the SMB exploit, describes how the malware spreads through the network.Uiwix Ransomware Using EternalBlue SMB Exploit To Infect Victims
Uiwix Ransomware Using EternalBlue SMB Exploit To Infect Victims
After WannaCry, UIWIX Ransomware and Monero-Mining Malware Follow Suit
After WannaCry, UIWIX Ransomware and Monero-Mining Malware Follow Suit - TrendLabs Security Intelligence Blog
UIWIX Ransomware appears to be fileless and doesnot start any new interpreter/process.
UIWIX sample, dump directly from memory
Antivirus scan for 146581f0b3fbe00026ee3ebe68797b0e57f39d1d8aecc99fdc3290e9cfadc4fc at 2017-05-22 09:19:32 UTC - VirusTotal
And yes, there is "fileless" behavior, as described in the above-mentioned articles, but this is only after the initial infection.
I still maintain that the initial infection is file-based, and would be blocked by Comodo autosandbox or any other decent default/deny mechanism.
However, I am not a malware analyst or anything even vaguely close to it. I am sure that @Lockdown or @Winter Soldier or another one of the technically knowledgeable members of this forum can clear things up for us.
There is probably already a video about Comodo and UIWIX, I am just too lazy to search for it...
I just saw this interesting post by @Andy Ful, which touches on the subject. If I understood it right, typical home user situations are not vulnerable to the worm, because the worm first has to get onto the local network.Well, the "worm" behavior, which utilizes the SMB exploit, describes how the malware spreads through the network.
And yes, there is "fileless" behavior, as described in the above-mentioned articles, but this is only after the initial infection.
I still maintain that the initial infection is file-based, and would be blocked by Comodo autosandbox or any other decent default/deny mechanism.
However, I am not a malware analyst or anything even vaguely close to it. I am sure that @Lockdown or @Winter Soldier or another one of the technically knowledgeable members of this forum can clear things up for us.
There is probably already a video about Comodo and UIWIX, I am just too lazy to search for it...
Is that true, that default deny security solutions can stop the EternalBlue & DoublePulsar attacks?
And here's an interesting point: uiwix is VM-sensitive, meaning that it checks for the presence of sandboxes, including Comodo sandbox. If it detects a sandbox, it is inert, in order to avoid detection:
UIWIX – Evasive Ransomware Exploiting ETERNALBLUE
Later moving to detect different sandbox solutions, UIWIX checks the loaded modules against a black list a list of DLLs (see full list below):

Figure 4: UIWIX tests if a DLL related to COMODO's sandbox is loaded
UIWIX – Evasive Ransomware Exploiting ETERNALBLUE
Later moving to detect different sandbox solutions, UIWIX checks the loaded modules against a black list a list of DLLs (see full list below):

Figure 4: UIWIX tests if a DLL related to COMODO's sandbox is loaded
Yes, out of the use of the same exploit as the initial infection vector, UIWIX presents significant differences compared to WannaCry. First of all, this malware has the ability to spread automatically in the network from an infected machine. UIWIX uses EternalBlue to inject the malware directly into the victim computer by doing the scans of his network, starting from the server under criminal's control. Also, apparently this malware does not store any files on the machine but is directly executed in the memory as a fileless and it seems to be sandbox aware.Well, the "worm" behavior, which utilizes the SMB exploit, describes how the malware spreads through the network.
And yes, there is "fileless" behavior, as described in the above-mentioned articles, but this is only after the initial infection.
I still maintain that the initial infection is file-based, and would be blocked by Comodo autosandbox or any other decent default/deny mechanism.
However, I am not a malware analyst or anything even vaguely close to it. I am sure that @Lockdown or @Winter Soldier or another one of the technically knowledgeable members of this forum can clear things up for us.
There is probably already a video about Comodo and UIWIX, I am just too lazy to search for it...
It seems there are not enough info about fileless behavior of this ransomware, but I think it is memory resident, at least in a certain phase, by using the memory space of legitimate Windows files, it loads its code into memory until when this file is processed. Even if the execution runs within memory space of the legitimate file, it still exists a dormant physical file that starts the execution.
Accordingly, this type of malware is not to be considered completely fileless, according to me.
How does the ball get rolling in the first place?Yes, out of the use of the same exploit as the initial infection vector, UIWIX presents significant differences compared to WannaCry. First of all, this malware has the ability to spread automatically in the network from an infected machine. UIWIX uses EternalBlue to inject the malware directly into the victim computer by doing the scans of his network, starting from the server under criminal's control. Also, apparently this malware does not store any files on the machine but is directly executed in the memory as a fileless and it seems to be sandbox aware.
It seems there are not enough info about fileless behavior of this ransomware, but I think it is memory resident, at least in a certain phase, by using the memory space of legitimate Windows files, it loads its code into memory until when this file is processed. Even if the execution runs within memory space of the legitimate file, it still exists a dormant physical file that starts the execution.
Accordingly, this type of malware is not to be considered completely fileless, according to me.
Doesn't the first victim on the network have to open a malicious email attachment, or something like that, and thereby execute a file?
Probably a social engineering attack, phishing mails...this is the first spread vector.How does the ball get rolling in the first place?
Doesn't the first victim on the network have to open a malicious email attachment, or something like that, and thereby execute a file?
I would like to add that even if this malware hides its presence behind the programming interface of an application, user-level or kernel-level, also in this case one file is actually present on the disk, but in stealth mode. Also in this case, it is not, therefore, completely fileless imo.
Sorry for being thick-headed, I am still trying to understand the attack vector.Probably a social engineering attack, phishing mails...this is the first spread vector.
I would like to add that even if this malware hides its presence behind the programming interface of an application, user-level or kernel-level, also in this case one file is actually present on the disk, but in stealth mode. Also in this case, it is not, therefore, completely fileless imo.
I get a socially engineered email, I stupidly click on the link, and then...
What I am trying to get at is this: I am familiar with two basic attack vectors
1 A malicious file is executed on the disk
2 A vulnerable app, such as a web browser, is exploited in order to gain access to system files
Is this a third attack vector, and if so, how does it work?
Speaking of UIWIX it seems very difficult for me to get a sample then I can just make assumptions, but there are some steps.
The first infection, as we said above is needed to launch the malicious process, and it can be done for example by opening an attachment, clicking on a link in an e-mail, opening a strange file on your computer and if you are using a remote file share.
But also the over-exploitation of EternalBlue is part of the initial diffusion vector because UIWIZ takes advantage of it to spread itself
Opening a malicious attachment, is a needed action because to enter a malicious code in a running process requires that before you carried out this action. Once the code is in memory, it can perform any action.
Probably also in this case, if the user has access to the sistem as administrator, it can be completely compromised, but if the account has limited rights, then I suppose additional steps will be needed to attack the system completely.
The first infection, as we said above is needed to launch the malicious process, and it can be done for example by opening an attachment, clicking on a link in an e-mail, opening a strange file on your computer and if you are using a remote file share.
But also the over-exploitation of EternalBlue is part of the initial diffusion vector because UIWIZ takes advantage of it to spread itself
Opening a malicious attachment, is a needed action because to enter a malicious code in a running process requires that before you carried out this action. Once the code is in memory, it can perform any action.
Probably also in this case, if the user has access to the sistem as administrator, it can be completely compromised, but if the account has limited rights, then I suppose additional steps will be needed to attack the system completely.
Thanks for explanations!Speaking of UIWIX it seems very difficult for me to get a sample then I can just make assumptions, but there are some steps.
The first infection, as we said above is needed to launch the malicious process, and it can be done for example by opening an attachment, clicking on a link in an e-mail, opening a strange file on your computer and if you are using a remote file share.
But also the over-exploitation of EternalBlue is part of the initial diffusion vector because UIWIZ takes advantage of it to spread itself
Opening a malicious attachment, is a needed action because to enter a malicious code in a running process requires that before you carried out this action. Once the code is in memory, it can perform any action.
Probably also in this case, if the user has access to the sistem as administrator, it can be completely compromised, but if the account has limited rights, then I suppose additional steps will be needed to attack the system completely.
Accordingly, a user on a home network should be protected, if all the connected PCs are running a decent default/deny solution, such as Comodo Firewall at CS settings, or VoodooShield at default settings.
Thanks for explanations!
Accordingly, a user on a home network should be protected, if all the connected PCs are running a decent default/deny solution, such as Comodo Firewall at CS settings, or VoodooShield at default settings.
One key thing about memory exploits based only on my limited understanding is that they can only exist for as long as the application they are attached to is open (without some permanent presence on the system). There could be a number of limitations on working code in the memory space of another process I suppose, but I am curious why so many malware programs contact the internet for a dropper. In the end, I think true fileless requires vulnerabilities in security software and in the application whose space is being hijacked.
On this topic, I have a rant. All of this brings into perspective how little we are getting about the actual code behind malware from official sources (so we can know what we need from security) such as online computer news sources and so on. Most of the advice that is presented is useless and amounts to "patch and pray". Thanks to @DardiM and the others on the malware analysis end of things at MTs and all they are doing to expose malicious coding practices to the outside world. I hope someone can find a way to link the results of work such as theirs to us out here is the outside world in a way that helps us make good decisions and that reaches mainstream news sources with a higher competency for instructing computer users.
A little bit on how little we get from news and expert sources. For example, information on adylkuzz was so sketchy and the same is true with information on wannacry:
Security Alert - Adylkuzz, the new virus that follows in WannaCry’s footsteps
and the Pandasecurity.com link, which basically brags for the hackers was almost identical to everything else on the net about both these malware attacks:
Adylkuzz, the new virus that follows in WannaCry's footsteps - Panda Security
To fight this malware, more or less I feel like the experts are saying, "check to see if your processor is a little bit sluggish and if so you could be pwned and basically nothing stops it but you better patch up." And the advice is to patch and make sure you have security programs. Srsly? We all know that what security is out there isn't configured to stop the worst threats, and much of it can't stop the worst ones at its best settings. Besides, governments have watchdogs to guarantee that officials are held accountable for their actions. So who holds Microsoft accountable for its actions and can guarantee that M$ patches are adequate? I hate that we have to trust M$'s patches to fix problems which appear to me to be so deeply rooted in an inadequate overall design strategy from the company in the first place. In my opinion and in the every sense, trusting a company that makes invisible products is a BAD idea. We need a link into the internals of MS Windows so that the program can be properly reviewed (and the decisions and responses of Microsoft) and analytically criticized. I think almost everyone agrees that there are chronically poor policy choices from M$ in Windows 10 and back all the way to Win 95.
Back to CFW and security, if your security program doesn't crash and isn't bypassed, maybe you are protected. This is true of CFW and other Comodo stuff in a fairly serious way. The simplicity of cruelsister's settings are the biggest strength of them I guess I would say and address this problem mostly. Comodo has fewer opportunities to crash, since it's not being expected to remember anything.
Last edited:
Another malware got trough CF @cruelsister settings.
Virustotal results: Antivirus scan for dcd0e73b264427269c262d6dc070570ce76c56faaf5ccfcebc0ae79b4e32130d at 2017-05-23 14:16:21 UTC - VirusTotal
My test - Click
Here are some pictures of test (if you can't see Malware Hub):
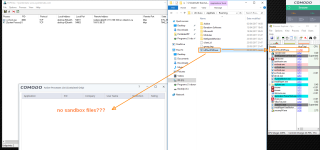
Virustotal results: Antivirus scan for dcd0e73b264427269c262d6dc070570ce76c56faaf5ccfcebc0ae79b4e32130d at 2017-05-23 14:16:21 UTC - VirusTotal
My test - Click
Here are some pictures of test (if you can't see Malware Hub):






That's why I don't get rid of the HIPSAnother malware got trough CF @cruelsister settings.
Virustotal results: Antivirus scan for dcd0e73b264427269c262d6dc070570ce76c56faaf5ccfcebc0ae79b4e32130d at 2017-05-23 14:16:21 UTC - VirusTotal
My test - Click
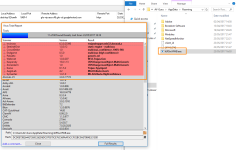
Here are some pictures of test (if you can't see Malware Hub):
View attachment 151897 View attachment 151898 View attachment 151899 View attachment 151900 View attachment 151901 View attachment 151902
Good day you can try setting me by setting up the CF settings file. Can you try this confige just for interest? Zaloha CF setings.cfgxAnother malware got trough CF @cruelsister settings.
Virustotal results: Antivirus scan for dcd0e73b264427269c262d6dc070570ce76c56faaf5ccfcebc0ae79b4e32130d at 2017-05-23 14:16:21 UTC - VirusTotal
My test - Click
Here are some pictures of test (if you can't see Malware Hub):
View attachment 151897 View attachment 151898 View attachment 151899 View attachment 151900 View attachment 151901 View attachment 151902
I guess no way to know if this is a CloudLookup fail at this point?
To fight this malware, more or less I feel like the experts are saying, "check to see if your processor is a little bit sluggish and if so you could be pwned and basically nothing stops it but you better patch up." And the advice is to patch and make sure you have security programs. Srsly? We all know that what security is out there isn't configured to stop the worst threats, and much of it can't stop the worst ones at its best settings. Besides, governments have watchdogs to guarantee that officials are held accountable for their actions. So who holds Microsoft accountable for its actions and can guarantee that M$ patches are adequate? I hate that we have to trust M$'s patches to fix problems which appear to me to be so deeply rooted in an inadequate overall design strategy from the company in the first place. In my opinion and in the every sense, trusting a company that makes invisible products is a BAD idea. We need a link into the internals of MS Windows so that the program can be properly reviewed (and the decisions and responses of Microsoft) and analytically criticized. I think almost everyone agrees that there are chronically poor policy choices from M$ in Windows 10 and back all the way to Win 95.
Back to CFW and security, if your security program doesn't crash and isn't bypassed, maybe you are protected. This is true of CFW and other Comodo stuff in a fairly serious way. The simplicity of cruelsister's settings are the biggest strength of them I guess I would say and address this problem mostly. Comodo has fewer opportunities to crash, since it's not being expected to remember anything.
As to M$ policy choices, and going back to at least Windows 98SE for me where my personal interest in PC Security first started, even back then I resigned myself to the fact that each and every release of their respective O/S's were for the most part always an experimental platform.
That is it was left up to the more technically advanced institutions and many other start up industry to fashion their own respective security programs to market to consumers around the existing M$ framework if you will. I actually see no difference even with the introduction of Windows 10 today.
Whether by design or not it is what it is and has become which would be OK if not for the fact that these same platforms are long since so widely distributed that they also are depended on to reliably and safely run a heck of a lot of business and industrial industry too. Or at the very least a part of some of the machinery which they depend on to make things tick for them.
For the occasional freelancers they also served as a basis for drawing up what turned out for many of them to be some pretty crafty customizations intended to dress up the looks from it's basic Grey etc. as well as, and more importantly, automate a whole host of routines for convenience and better management of things and in essence, at least as I see it, that was the underlying policy crafted in order to encourage new business? etc.
If enough companies and consumers flocked to this (experimental? Framework) with plenty of enough access to useful programs designed for their various needs and/or expectations and they actually improved things, then M$ had established for themselves a permanent high ground in this particular field.
Just my opinion and not to be accepted as anything else, but............
In reply to the 2nd underline, I 100% agree that if nothing else, courtesy that ever so generous good soul who actually took some time and effort to share very useful rules applied to CFW 10 and point out those "strengths" by testing it, given today's far more harsh web landscape, a user can rest a bit more comfortable in the fact that there are such programs around like this that have greatly improved your chances to stay safe.
I hope some of this made a little sense. I try.
You may also like...
-
App Review Microsoft Defender Antivirus feat AI Defender
- Started by Shadowra
- Replies: 13
-
App Review DrWeb Security Space BETA
- Started by Shadowra
- Replies: 11
-
App Review Kaspersky Premium vs McAfee Advanced
- Started by Shadowra
- Replies: 87
-
Advice Request Help: Comodo 2025 - cmdguard.sys - boot fail with newer Nvidia drivers
- Started by Something-x2
- Replies: 33
-