Does AppGuard (by default) protect against ink, lnk and pif vulnerabilities? I have added them to user space?
Completely securing a computer without using programs
- Thread starter TheMalwareMaster
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
5
509322
Does AppGuard (by default) protect against ink, lnk and pif vulnerabilities? I have added them to user space?
AppGuard blocks *.pif by default.
Don't add shortcut files to User Space.
Add wscript.exe and cscript.exe to the Guarded Apps list or disable them by adding to User Space (YES). cmd.exe and powershell.exe are already covered, but I recommend that you disable powershell.exe by unticking it in the Guarded Apps list and then adding it to User Space (YES).
See your PM.
Last edited by a moderator:
5
509322
Where about's is my PM?
PM = Private Messages
TheMalwareMaster
Level 21
Thread author
Verified
Honorary Member
Top Poster
Well-known
Forum Veteran
I'm back on this old post I made some time ago...
I'm quite bored of using COMODO Firewall because I want to optimize my system performance, even if COMODO doesn't use much of resources...
I'm Learning about SRP and Windows Enforcment in my VM, in order to make a security config without the need of security software
I'm quite bored of using COMODO Firewall because I want to optimize my system performance, even if COMODO doesn't use much of resources...
I'm Learning about SRP and Windows Enforcment in my VM, in order to make a security config without the need of security software
A
antreas
I will share mine, if you share yours.Is it possible?
[Batch] Windows Tweaks - Pastebin.com
I use it like that for years, no problems here. I do not even use AV on mom's computer, it was too much of a hassle. I have only recently added Windows Firewall, because since 1709, it has got too intrusive when disabled and I got tired of restarting computer every time, just to enable/disable it.Is it possible?
TheMalwareMaster
Level 21
Thread author
Verified
Honorary Member
Top Poster
Well-known
Forum Veteran
Thanks... I will save your link.... Such a lot of tweaks!!I will share mine, if you share yours.
[Batch] Windows Tweaks - Pastebin.com
I use it like that for years, no problems here. I do not even use AV on mom's computer, it was too much of a hassle. I have only recently added Windows Firewall, because since 1709, it has got too intrusive when disabled and I got tired of restarting computer every time, just to enable/disable it.
Are these all really needed? Or you think that SRP+some important ones, like: Disable execution of unsigned programs, disable CMD, disable Powershell, disable remote assistance, disable Windows script host, disable autorun, use Run by smartscreen are OK? I basically know only these by now
Not really, most are just customization. Some can be considered as security tweaks, like when Windows/software thinks, there is no internet, it does not try to connect.Are these all really needed?
I like to think, that disabling WSH and removing powershell protects PC from 99% of malware, I have not seen ransomware, which would be able to infect PC without them. Note that I say removing powershell, not disabling it. Restriction policies can be bypassed, but if PS is not there, you can not run ps scripts, no matter what.Or you think that SRP+some important ones, like: Disable execution of unsigned programs, disable CMD, disable Powershell, disable remote assistance, disable Windows script host, disable autorun, use Run by smartscreen are OK?
It is also interesting, that by blocking adult webpages, about 10-30% of malware gets blocked (malc0de links), they can not be downloaded either, unless IP is used.
Attachments
Last edited:
TheMalwareMaster
Level 21
Thread author
Verified
Honorary Member
Top Poster
Well-known
Forum Veteran
Interesting... How can these be bypassed? Taking a look at @Andy Ful Hard configurator,this "block sponsors" should be able to prevent restriction policies bypassNote that I say removing powershell, not disabling it. Restriction policies can be bypassed
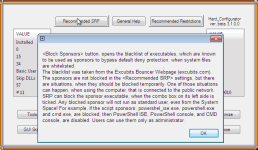
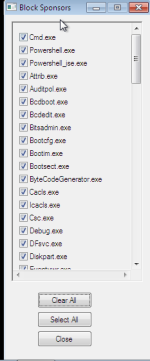
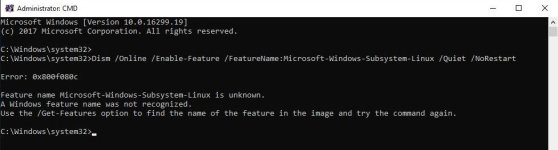
That is nice. I am not an expert like Andy and others, I am just trying to cover the basics as I understand them. I would say, whatever works you, but restrictions can be bypassed, so could be restrictions of the restrictions, once altered by malware. There is never enough restrictions in place. I prefer to go all the way using unconventional methods, which are not known to malware coders, like disabling bash malware simply by preventing it from being enabled using DISM. If you look at how malware works (like the scary SeTcbPrivilege), it checks for restrictions, etc and once it elevates to system rights, it will change settings to whatever it wants to.Interesting... How can these be bypassed? Taking a look at @Andy Ful Hard configurator,this "block sponsors" should be able to prevent restriction policies bypass
15 Ways to Bypass the PowerShell Execution Policy
Attachments
Last edited:
TheMalwareMaster
Level 21
Thread author
Verified
Honorary Member
Top Poster
Well-known
Forum Veteran
Interesting... I looked at your config and that's what I would like to use... Except I want to add also SRP..That is nice. I am not an expert like Andy and others, I am just trying to cover the basics as I understand them. I would say, whatever works you, but restrictions can be bypassed, so could be restrictions of the restrictions, once altered by malware. There is never enough restrictions in place. I prefer to go all the way using unconventional methods, which are not known to malware coders, like disabling bash malware simply by preventing it from being enabled using DISM. If you look at how malware works (like the scary SeTcbPrivilege), it checks for restrictions, etc and once it elevates to system rights, it will change settings to whatever it wants to.
15 Ways to Bypass the PowerShell Execution Policy
RISKY - TairikuOkami's Crippled Windows
What are these? mshta.exe/msra.exe/psexec.exe/bash.exe/nc.exe/nc64.exe/netsh.exe?
OK, with this kind of setup one can safely disable Windows Defender. But what about Windows Firewall? I think one should keep it eneabled to prevent Attacks from the internal network.
Now, let's focus on an other case. Signed malware. Really rare, but can happen (see CCleaner case). If an admin runs CCleaner, this config will be bypassed.
I knew forcepoint (the guys protecting avast servers, I think), were able to intercept the backdoor with their firewall. Also Cisco anti-exploit software was able to intercept it... Do you know any Windows Firewall tweak/other software that can protect from this kind of supply-chain signed malware attack?
Those are commonly used by malware, I add them on the go, just for the reference, I use disallow policy, which is not very effective, since it works only for the current user, I am thinking about SRP as well.What are these? mshta.exe/msra.exe/psexec.exe/bash.exe/nc.exe/nc64.exe/netsh.exe?
msra.exe - used by remote assistance
mshta.exe - used by scripting malware
bash.exe - linux subsystem malware, AVs are unable to stop it
netsh.exe - can be used for various network commands, like add/change windows firewall rules
psexec.exe/nc.exe/nc64.exe - not present by default, but hackers usually do not bother renaming them
nc.exe | ThreatExpert statistics
Beware of the Bashware: A New Method for Any Malware to Bypass Security Solutions - Check Point Research
Because of, or I might say, thanks to insufficient IP4 adresses, virtually everyone is behind a router, which blocks inbound requests and unsolicited traffic (which helps to avoid a higher CPU/network usage). But even without a router and if you do not use a firewall, all ports are blocked, that is the same like stealthed, in both cases, all inbound requests are dropped. A computer can be exploited only when you have a process running, which keeps the port open. Usually the attacker scans the computer and if he finds an open port, he tries to exploit, otherwise there is not much he can do.OK, with this kind of setup one can safely disable Windows Defender. But what about Windows Firewall? I think one should keep it eneabled to prevent Attacks from the internal network.
CCleaner sure made a mess of things. If you have a trusted software, you allow it, otherwise it would not be able to run/work properly. The basic rule is obviously do not allow more than needs to be, like no outbound, unless needed. "Luckily", CCleaner was already infected with malware, so they did not use too sophisticated technics for it, I believe a firewall was able to simply block its outbound requests, but if someone used its remote functionality or auto-updating, that would not help them, unless they would setup an allowed IP range, if you are using a firewall, you should take advantage of it, like setup IPs for DNS, etc.Now, let's focus on an other case. Signed malware. Really rare, but can happen (see CCleaner case). If an admin runs CCleaner, this config will be bypassed.
I knew forcepoint (the guys protecting avast servers, I think), were able to intercept the backdoor with their firewall. Also Cisco anti-exploit software was able to intercept it... Do you know any Windows Firewall tweak/other software that can protect from this kind of supply-chain signed malware attack?
TheMalwareMaster
Level 21
Thread author
Verified
Honorary Member
Top Poster
Well-known
Forum Veteran
Thanks a lot! How one can be able to confgure a firewall before, in order to prevent these kind of intrusions? Like, nobody knew CCleaner was infected, so how can one protect against supply-chain Attacks?CCleaner sure made a mess of things. If you have a trusted software, you allow it, otherwise it would not be able to run/work properly. The basic rule is obviously do not allow more than needs to be, like no outbound, unless needed. "Luckily", CCleaner was already infected with malware, so they did not use too sophisticated technics for it, I believe a firewall was able to simply block its outbound requests, but if someone used its remote functionality or auto-updating, that would not help them, unless they would setup an allowed IP range.
If it is a simple malware like in CCleaner's case, settings up an allowed IP range should help. Lets say, that you use it just auto-updating, you would allow only TCP Out to piriform.com via port 80/443 and UDP to your DNS servers via port 53. It is pain to setup everything, but once done, it provides much safer environment. It will not protect against malware injecting to other processes or more advanced technics, but it is a start.how can one protect against supply-chain Attacks?
TheMalwareMaster
Level 21
Thread author
Verified
Honorary Member
Top Poster
Well-known
Forum Veteran
Thanks a lot for all your help!If it is a simple malware like in CCleaner's case, settings up an allowed IP range should help. Lets say, that you use it just auto-updating, you would allow only TCP Out to piriform.com via port 80/443 and UDP to your DNS servers via port 53. It is pain to setup everything, but once done, it provides much safer environment. It will not protect against malware injecting to other processes or more advanced technics, but it is a start.
iDK about Aandy tool but Rehips can block this!
from fixer:
There is a PowerShell built-in execution policy. Like, allow only scripts signed by a trusted publisher. You can think of it as of some kind of SRP (software restriction policies) extension. And it can be bypassed. That's why we don't rely on SRP and ReHIPS uses its own monitoring.
ReHIPS operates on a higher level than this built-in execution policy. So these bypasses don't affect it.
Last edited:
It seems, that "Seconfig Xp" can work on all Windows versions... or am I wrong?
Seconfig XP - freeware security configuration utility for Windows
Seconfig XP - freeware security configuration utility for Windows
- A free tool to close (not just shield) most exploited Windows security holes.
- Can close ports 135, 137-139, 445, 1025 (used by file and printer sharing, Windows domains, other Microsoft Networks access and widely exploited by worms, hackers etc.), 1900, 5000 (used by UPnP) and other...
- Can disable most dangerous Windows services.
- Can protect Windows side against most ARP spoofing/poisoning attacks.
- Can configure many other hidden security related Windows TCP/IP settings.
- Works only with registry (no files, services, drivers etc.).
- Includes three easy to use presets for average home (standalone) computers, Microsoft Networks members and standalone computers with VPN client access to Microsoft Networks.
I will share mine, if you share yours.
[Batch] Windows Tweaks - Pastebin.com
I use it like that for years, no problems here. I do not even use AV on mom's computer, it was too much of a hassle. I have only recently added Windows Firewall, because since 1709, it has got too intrusive when disabled and I got tired of restarting computer every time, just to enable/disable it.
It leaves you without Internet connection. The Start button doesn't work and I don't know how many other problems. Thank you in the same way. Best regards.
You can disable "network store service" and internet will work way more stable without "network optimizations", which cause more problems than they are worth (but this one also disables Windows Firewall). You just have to setup network settings manually. Though some services have be re-enabled for Windows Updates.It leaves you without Internet connection. The Start button doesn't work and I don't know how many other problems.
Attachments
You may also like...
-
App Review Webroot SecureAnywhere Complete 2025
- Started by Shadowra
- Replies: 16
-
App Review DrWeb Security Space BETA
- Started by Shadowra
- Replies: 11
-
App Review Bitdefender Total Security 2026
- Started by Shadowra
- Replies: 60
-
App Review Qihoo 360 Free Total Security 2025
- Started by Shadowra
- Replies: 28
-
Serious Discussion A Habit-Based Guide to Internet Security
- Started by Divergent
- Replies: 2