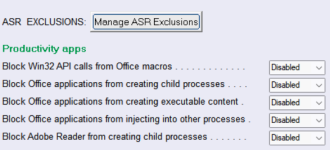
When using Outlook and accessing my calendar Outlook gets unresponsive when fetching the weather forecast for my location with ConfigureDefender on High.
What (ASR rule?) could be causing this?
It's not happening with ConfigureDefender at Default.
Any events in the ConfigureDefender Log?