@Umbra- I just would like to pinpoint just a few things now,as i said i dont have much time
available now
I said :
I hear a lot of advice these days about the need of 'upgrading' to Windows10 as a measure of
security, but i think all this fanfare is -perhaps- greatly exaggerated.
Did i say 'untrue' or 'false'? No.
But you vented your fury immediately stating
you are maybe the first one that contradict himself in the same post
.
Great : i was the FIRST!!!
First in all history of the forum or of all time?
In both instances i think there were many more before me.
But I have to invite both readers and moderators to read my post carefully and find a hint
of contradiction in what i wrote in this first sentence.
Either something really bad happened to you in the ten minutes prior to your post, or you
have something personal?
You never had any issues with Windows10? Good for you,but there's a million people who
had.especially in the first year,a lot of problems.
This may have nothing to do with security,but it was annoying. Now this has improved for
Windows10pro to the point you can defer updates for a while,a fact which i mentioned as
improved,regarding the OS.
Then you launch yourself into 'imaging' what i would do or think with my installed software
which is a really remarkable feat.
You go as far as stating that i run NVTExe,because 'i dont trust' Kaspersky...:
if it were so i wouldnt spend money every year on 'untrusted' software....
with Windows 10 i have a secure OS out-of-the-Box
in my post it is
VERY CLEAR i consider Windows7 safe
WITH a bunch of security
software which i mention, so i think you are trying to overturn the cards here as my post
was
NOT a comparison
btw OUT OF THE BOX oss, which is obviously in favour of W10.
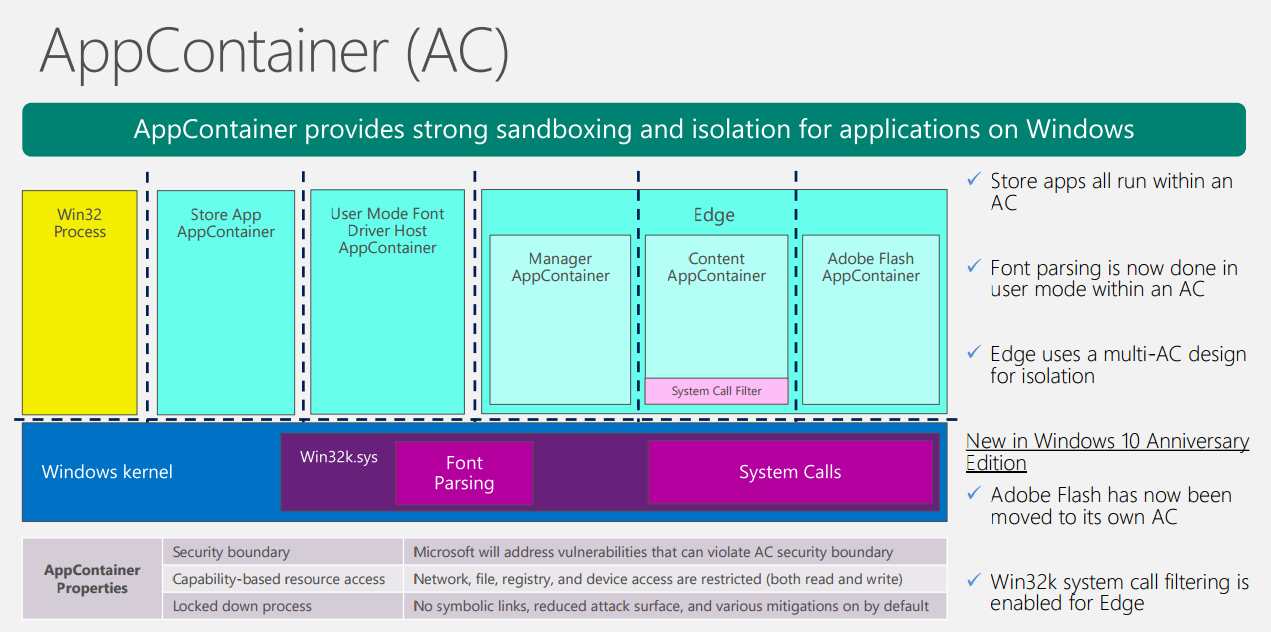
because you seems to ignore what are kernel exploits delivered via fileless malware.
This point needs further study on my part,i dont have time now,but i'll search and come back
in a couple of days time perhaps. It seems to me what you say is irrilevant-regarding the
type of OS- but depending on other factors which can be adressed by security programs.
try again without any 3rd party securty tools, will you do? i dont think so.
When you compare stuff, you compare them at the same level, both out-of-the-box or both with additional tools;
Definetely! But i was not endorsing the use of Windows7 as it came out in 2009....
this was only in your imagination.
I bet you will never run Windows 7 without any security tools
NAP: you can bet your house on it.
But ,again,
I NEVER STATED that.
Rather comical.
The whole "fanfare" as you claimed
You're hit,it seems,by the word 'fanfare' about upgrading to W10,which may i remind you means
1: a short and lively sounding of trumpets
2: a showy outward display
3: a lot of talk or activity showing that people are excited about something
the arrival of a warning from MS in all windows7 computers of the planet i guess justifies the definition.
I observed many security-oriented people, bashing Windows 10 because "i can make Windows 7 very safe", sure, but does 99% of the users worldwide can do the same? not at all.
Am i writing my post for the 99% or for myself?
From now on anyone posting here has to speak for those who know nothing and dont use any
security software?
So yes , i'm hypercritic to those who mislead users stating upgrading to Windows 10 is not necessary, while they safely relax behind their security knowledge/tools and let Average Joe struggle and be victims of keyloggers and ransomware
ahahah!!! so
you are heavily contradicting yourself here,as you imply that i,for one,can
SAFELY RELAX with Windows7 provided i run suitable softwares....
I also didnt know that everytime i express an opinion i have to speak to 'average joe'.
This stance would reduce to rubble 50-60% of the forum.
That was true during WinXP/7 era, but you didn't have much ransomware or credential stealers like now.
Bloody hell!! I did not know MS had devised a total protection against ransomware in windows10!!!
I will immediately remove Comodo protections in my notebook running W10,must be redundant
and useless and i wouldnt like MS gets offended by it.
you dismissed upgrading Windows 10 as security measure, while you keep Windows 7 boosted
with 5 security apps.
Exactly.As the intent of my post was establishing that Windows7 could be used safely
even without updates
for a COUPLE OF YEARS more....no more than that....but you
misrepresented my entire post.
Furthermore you immediately used a quasi-offensive tone without any reason,so when i have time i will reply to you about some tek things you mentioned.