Evjl's Rain
Level 47
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
- Apr 18, 2016
- 3,676
- 28,872
- 4,599
I performed a test between well-known DNS-es with multiple links
OpenDNS: 208.67.222.222, 208.67.220.220
Norton ConnectSafe: 199.85.126.10, 199.85.127.10
Quad9: 9.9.9.9, 149.112.112.112
SafeDNS: 195.46.39.39, 195.46.39.40
Neustar Free Recursive: 156.154.70.2, 156.154.71.2
Comodo Shield: 8.26.56.10, 8.20.247.10
Yandex: 77.88.8.88, 77.88.8.2
Adguard: 176.103.130.130, 176.103.130.131
Links: 56, may contain some dead links
10 links were collected from vxvault, malc0de, phishtank, openphish and especially 6 links from MT malware Hub. Special thanks to @Solarquest, @silversurfer and @Der.Reisende for providing the samples so I could extract some links from script files.
NOTE: 1 DNS may not be able to resolve the links while others can. Therefore, you would see 1/10, 2/9 or 3/7 in the results
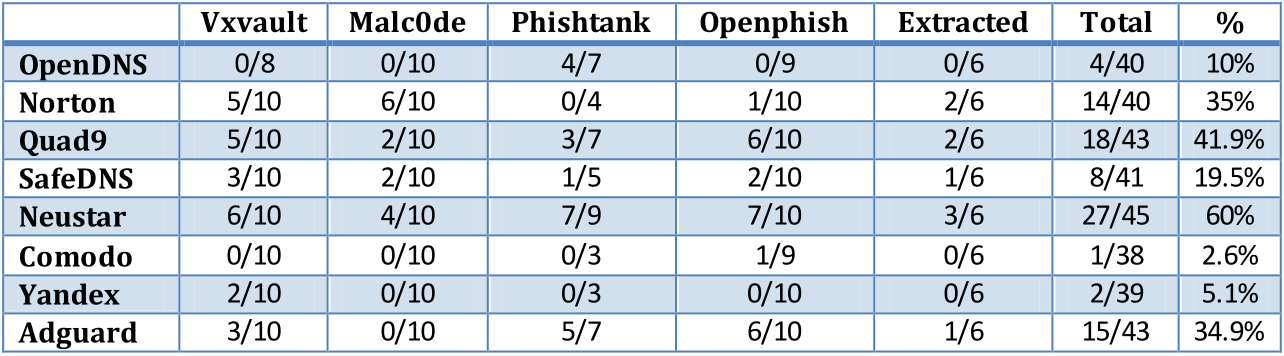
Winner: Neustar Free Recursive DNS
OpenDNS: 208.67.222.222, 208.67.220.220
Norton ConnectSafe: 199.85.126.10, 199.85.127.10
Quad9: 9.9.9.9, 149.112.112.112
SafeDNS: 195.46.39.39, 195.46.39.40
Neustar Free Recursive: 156.154.70.2, 156.154.71.2
Comodo Shield: 8.26.56.10, 8.20.247.10
Yandex: 77.88.8.88, 77.88.8.2
Adguard: 176.103.130.130, 176.103.130.131
Links: 56, may contain some dead links
10 links were collected from vxvault, malc0de, phishtank, openphish and especially 6 links from MT malware Hub. Special thanks to @Solarquest, @silversurfer and @Der.Reisende for providing the samples so I could extract some links from script files.
NOTE: 1 DNS may not be able to resolve the links while others can. Therefore, you would see 1/10, 2/9 or 3/7 in the results
Winner: Neustar Free Recursive DNS
Last edited:
