- Apr 6, 2016
- 440
Worm viruses are malicious programs that can replicate themselves but cannot infect executable files. Doctor Web specialists have examined one such Trojan that infects RAR archives and uses the VNC remote access system to spread itself.
The worm, named BackDoor.Ragebot.45, receives instructions via the IRC (Internet Relay Chat) protocol by connecting to the corresponding chat channel.
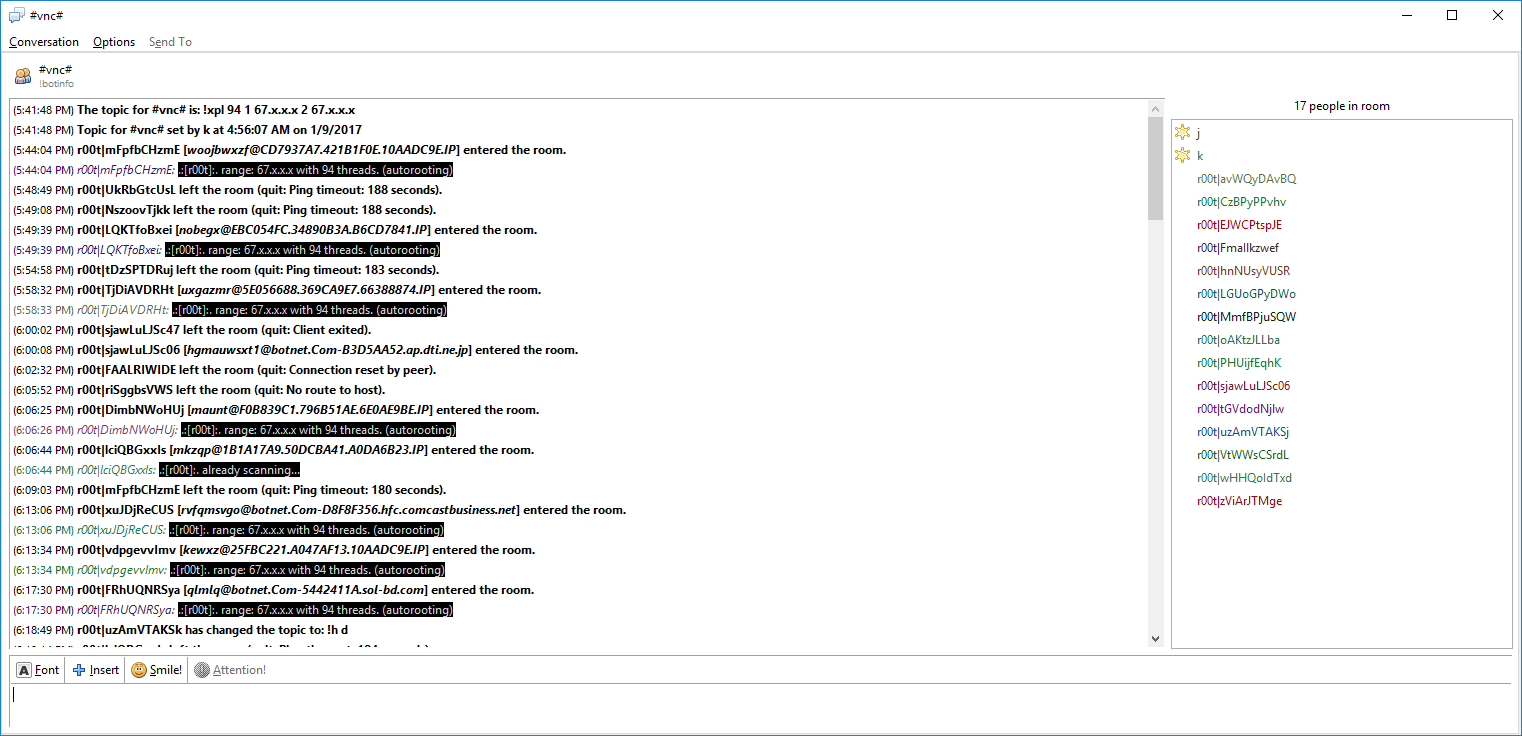
After infecting a computer running Windows, BackDoor.Ragebot.45 launches the FTP server and uses it to download its copy on the computer. It then scans accessible subnetworks, searching for nodes with the open port 5900 to establish a connection to the Virtual Network Computing (VNC) desktop. Once the machine is detected, BackDoor.Ragebot.45 tries to obtain access to it via a brute-force attack.
If access is obtained, the worm establishes the VNC connection and sends keystroke signals, using them to run the CMD command interpreter and execute the code for launching its copy over the FTP protocol. This is how the worm replicates itself.
One more function of BackDoor.Ragebot.45 is to search and infect RAR archives on removable media. When detecting an archive, the Trojan saves a copy (named setup.exe, installer.exe, self-installer.exe, or self-extractor.exe) to it. For the infection to be successful, the user must run an executable file that has been extracted from the archive.
In addition, the Trojan copies itself to the ICQ client folder together with folders of programs designed to establish P2P connections. Once BackDoor.Ragebot.45 receives the corresponding command, it searches for other Trojans in the system and, if it finds any, deletes their executable files. The Trojan has special white lists containing file names (mainly belonging to Windows system files) that it ignores, allowing them to operate on the infected machine.
The existence of samples of a previous version of BackDoor.Ragebot.45 became public some time ago. Perhaps, this will cause the worm to actively spread itself in the future. Dr.Web successfully detects and removes BackDoor.Ragebot.45, and, therefore, this malicious program poses no threat to our users.
More about this Trojan
The worm, named BackDoor.Ragebot.45, receives instructions via the IRC (Internet Relay Chat) protocol by connecting to the corresponding chat channel.

After infecting a computer running Windows, BackDoor.Ragebot.45 launches the FTP server and uses it to download its copy on the computer. It then scans accessible subnetworks, searching for nodes with the open port 5900 to establish a connection to the Virtual Network Computing (VNC) desktop. Once the machine is detected, BackDoor.Ragebot.45 tries to obtain access to it via a brute-force attack.
If access is obtained, the worm establishes the VNC connection and sends keystroke signals, using them to run the CMD command interpreter and execute the code for launching its copy over the FTP protocol. This is how the worm replicates itself.
One more function of BackDoor.Ragebot.45 is to search and infect RAR archives on removable media. When detecting an archive, the Trojan saves a copy (named setup.exe, installer.exe, self-installer.exe, or self-extractor.exe) to it. For the infection to be successful, the user must run an executable file that has been extracted from the archive.
In addition, the Trojan copies itself to the ICQ client folder together with folders of programs designed to establish P2P connections. Once BackDoor.Ragebot.45 receives the corresponding command, it searches for other Trojans in the system and, if it finds any, deletes their executable files. The Trojan has special white lists containing file names (mainly belonging to Windows system files) that it ignores, allowing them to operate on the infected machine.
The existence of samples of a previous version of BackDoor.Ragebot.45 became public some time ago. Perhaps, this will cause the worm to actively spread itself in the future. Dr.Web successfully detects and removes BackDoor.Ragebot.45, and, therefore, this malicious program poses no threat to our users.
More about this Trojan
