It's a good thing we have Hard_Configurator, to take care of all this stuff for us.You are pretty much safe, because you know how to set SRP properly. Most SRP users, are hardly as safe as they think. They do not recognize the shortcut, macros, and scriptlet vulnerabilities, which can easily bypass the standard SRP configuration. They do not know how many Windows folders have writable & executable permissions and allow dropping executables to whitelisted folders without UAC prompt.
Advice Request Does oneself really need an Antivirus?
- Thread starter LDogg
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
Hard_Configurator makes the proper SRP configuration much easier, but still in most cases, it is the task to do for advanced users.
5
509322
since vista i don't use an antivirus, no realtime protection only srp. and adguard. so far so good
It is best practice to use an antivirus alongside SRP and ad blocker. Not using an antivirus should be reserved for a low resource, decrepit system that is basically a real pain to use if an antivirus is running. I have yet to find a system that I cannot run an antivirus on... even a 10 year old Toshiba with a low-end Pentium chip and only 3 GB RAM. Instead of packing that system with a bunch of programs, I carefully choose what to install on it to accommodate the security soft resource overhead. It's the smart way to do things.
5
509322
If you want an honest opinion, is extremely easy to exploit Linux compared to Windows, Windows has lots of holes patched and systems (with more every year) in place that make it a chore.
Linux users truly believe they're more secure, when they're not, people are just not interested in attacking them.
Speaking outside of exploits, you don't need to spend much time on Linux to find an annoying bug..
Windows is more secure only to the extent that discovering, reporting and patching vulnerabilities and other weaknesses is ongoing. However, the rate of doing so is not fast enough. It will never be fast enough. It probably can never be substantially faster than it is today.. There are a ton of undiscovered and upatched vulnerabilities and weaknesses in Windows and the programs that run on it. And malc0ders are developing new and innovative ways to compromise Windows systems. So Microsoft and everybody else always remain behind the 8 Ball.
It is not economically rewarding to target and attack Linux. That is why malc0ders do not target the OS.
Malware and making money from it is a numbers game. The more systems you attack with widely-used, popular software\OS, the more financially rewarding that it is. Since Windows is the most prevalently used OS world-wide, and users run the most exploited programs on it along with generally poor or non-existent security practices, the malc0ders target Windows.
Windows, and programs that run on Windows, are a treasure trove of undiscovered and unpatched vulnerabilities and weaknesses.
Last edited by a moderator:
Hi...here are my observations after making some short test connected to level protection of SS and "default deny/allow" feature...each one made with enabled "Auto-block suspicious behaviour" option and empty list of rules (in "Aplication Execution Control" also)Yes, I found it (Ask User), but this is only for Certified applications, and the user will be alerted only for the suspicious applications (not for all applications). This feature is not for blocking the malware, but rather for avoiding blocking the legal applications.
.
Anyway, I found one useful feature related to folders:
"Exclude existing files and any future files in this folder - This option will exclude all currently existing files in the folder as well as all future files. It is less safe than first option; however, it might be useful for users who often modify files."
.
The above can be used for whitelisting/blacklisting folders.
There is an option 'Make it denied", that will apply all SpyShelter rules to this folder (I think). This would work as default-deny for suspicious applications. Yet, if the malware can behave like the legal software, then SpyShelter HIPS (deny template) can be bypassed, so this kind of security is only close to default-deny. The alerts can be suppressed by ticking the option 'Auto-block suspicious behaviour'.
One should test such setup to know how strong it can be.
.
Edit.
I think that the same thing can be done with Sandboxie (paid), by sandboxing disks or folders in a highly restricted sandbox.
- "Ask user" level - with no rules nothing can be launched...you can't run any process including system/MS processes e.g. Control Panel and you can't even switch-off the system (of course you can power-off phisical machine), every rule added to the list is "block". In this context I don't think that "Certified applications" can play some role...for me they are useless in such settings.
- "Auto allow - high..." - known apps can be launched but SS automaticaly creates "block" rules for some specific (suspicious for SS) actions/behaviours...here trusted signers can play the role by allowing to run apps and acting only "non-critical" actions
- "Auto allow - medium..." similar to mentioned abowe but most of actions are automaticaly allowed without adding to the list of rules...I noticed only blocked (and added to the list) actions that are "very critical" for system like #26,48,50
- Allow Microsoft" - I didn't noticed blocked actions of diferent apps/processes but only automaticaly allowed and added to the list...maybe such processes don't present suspicious behaviour?
Did you try to block the %UserProfile% via "Exclude existing files and any future files in this folder" and 'Make it denied"? I think that after blocking it, the user could exclude some programs by applying the concrete settings per program. It would be interesting to know if 'Make it denied' is more restrictive than 'Auto allow - high ...' or 'Allow Microsoft'.Hi...here are my observations after making some short test connected to level protection of SS and "default deny/allow" feature...each one made with enabled "Auto-block suspicious behaviour" option and empty list of rules (in "Aplication Execution Control" also)
- "Ask user" level - with no rules nothing can be launched...you can't run any process including system/MS processes e.g. Control Panel and you can't even switch-off the system (of course you can power-off phisical machine), every rule added to the list is "block". In this context I don't think that "Certified applications" can play some role...for me they are useless in such settings.
- "Auto allow - high..." - known apps can be launched but SS automaticaly creates "block" rules for some specific (suspicious for SS) actions/behaviours...here trusted signers can play the role by allowing to run apps and acting only "non-critical" actions
- "Auto allow - medium..." similar to mentioned abowe but most of actions are automaticaly allowed without adding to the list of rules...I noticed only blocked (and added to the list) actions that are "very critical" for system like #26,48,50
- Allow Microsoft" - I didn't noticed blocked actions of diferent apps/processes but only automaticaly allowed and added to the list...maybe such processes don't present suspicious behaviour?
Last edited:
@Andy Ful
I've never tested feature to block whole excluded folder with its content because such option is designed to exclude - in manual they say "meaning, that you don't want to block" - so actualy means to set folder free from protection. I'm using instead it option to restrict folder that one can find and add to the list in "Restricted apps" tab...by this way I have added folder for downloaded content and additionaly that one in which I have more than two thousend installators (it's my archive) of not only security apps and its versions. Of course we can't forget add for restricted folder important option to write and save inside - "folders with write access" tab.
But back to your question - I've checked what will happened when we make denied user folder/folders...because of my Vista I've used to make deny whole folder "C:\Users\my_name\"...and actualy nothing interresting have happened with usual (installed) apps - it looks that they still work properly. Some interresting things I found when tried to install new app using .exe installator - in my case it was NVT OSArmor - insttalation process was broken with special system alert...see screenshot
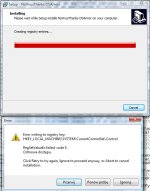
Some actions was blocked also when I've tried to run zipped portable apps image browser CPix...but app would launch and open window. I've tested also UNetbootin that is single .exe file - it was executed from the same folder as mentioned above and nothing have been blocked - it worked as usual.
So...It's still "mistery" for me what is the rule/base of SS that allow specific app (its actions) or block another ones. It looks that thing which pass thru temp user folders sometine is just blocked and sometime only some actions off app are blocked. I attached some lines from log file of SS to show such issue
"2018-05-29 18:33:51,2192,C:\Moje programy\FreeCommander\FreeCommander.exe,53,Allowed ;Execution of an application ("C:\testy\unetbootin-windows-661.exe" )
2018-05-29 18:34:01,2192,C:\Moje programy\FreeCommander\FreeCommander.exe,53,Allowed ;Execution of an application ("C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe" )
2018-05-29 18:34:01,4060,C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe,50,Blocked ;Accessing the network via DNS Resolver service
2018-05-29 18:34:01,4060,C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe,48,Blocked ;Outgoing network access
2018-05-29 18:34:15,4060,C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe,26,Blocked ;Modifying protected registry key (HKLM\SOFTWARE\Classes\CPix.bmpfile\shell\open\command,)
2018-05-29 18:35:42,2000,C:\Windows\System32\taskeng.exe,53,Allowed ;Execution of an application (C:\Windows\system32\wermgr.exe -queuereporting)
2018-05-29 18:36:02,2192,C:\Moje programy\FreeCommander\FreeCommander.exe,53,Allowed ;Execution of an application ("C:\testy\osarmor_setup_1.4_test67.exe" )
2018-05-29 18:36:02,2964,C:\testy\osarmor_setup_1.4_test67.exe,53,Allowed ;Execution of an application ("C:\Users\xxx\AppData\Local\Temp\is-1CBGV.tmp\osarmor_setup_1.4_test67.tmp" /SL5="$220426,8243353,57856,C:\testy\osarmor_setup_1.4_test67.exe" )
2018-05-29 18:36:09,2448,C:\Users\xxx\AppData\Local\Temp\is-1CBGV.tmp\osarmor_setup_1.4_test67.tmp,26,Blocked ;Modifying protected registry key (HKLM\SYSTEM\ControlSet001\Control,ServicesPipeTimeout)"
I've never tested feature to block whole excluded folder with its content because such option is designed to exclude - in manual they say "meaning, that you don't want to block" - so actualy means to set folder free from protection. I'm using instead it option to restrict folder that one can find and add to the list in "Restricted apps" tab...by this way I have added folder for downloaded content and additionaly that one in which I have more than two thousend installators (it's my archive) of not only security apps and its versions. Of course we can't forget add for restricted folder important option to write and save inside - "folders with write access" tab.
But back to your question - I've checked what will happened when we make denied user folder/folders...because of my Vista I've used to make deny whole folder "C:\Users\my_name\"...and actualy nothing interresting have happened with usual (installed) apps - it looks that they still work properly. Some interresting things I found when tried to install new app using .exe installator - in my case it was NVT OSArmor - insttalation process was broken with special system alert...see screenshot

Some actions was blocked also when I've tried to run zipped portable apps image browser CPix...but app would launch and open window. I've tested also UNetbootin that is single .exe file - it was executed from the same folder as mentioned above and nothing have been blocked - it worked as usual.
So...It's still "mistery" for me what is the rule/base of SS that allow specific app (its actions) or block another ones. It looks that thing which pass thru temp user folders sometine is just blocked and sometime only some actions off app are blocked. I attached some lines from log file of SS to show such issue
"2018-05-29 18:33:51,2192,C:\Moje programy\FreeCommander\FreeCommander.exe,53,Allowed ;Execution of an application ("C:\testy\unetbootin-windows-661.exe" )
2018-05-29 18:34:01,2192,C:\Moje programy\FreeCommander\FreeCommander.exe,53,Allowed ;Execution of an application ("C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe" )
2018-05-29 18:34:01,4060,C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe,50,Blocked ;Accessing the network via DNS Resolver service
2018-05-29 18:34:01,4060,C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe,48,Blocked ;Outgoing network access
2018-05-29 18:34:15,4060,C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe,26,Blocked ;Modifying protected registry key (HKLM\SOFTWARE\Classes\CPix.bmpfile\shell\open\command,)
2018-05-29 18:35:42,2000,C:\Windows\System32\taskeng.exe,53,Allowed ;Execution of an application (C:\Windows\system32\wermgr.exe -queuereporting)
2018-05-29 18:36:02,2192,C:\Moje programy\FreeCommander\FreeCommander.exe,53,Allowed ;Execution of an application ("C:\testy\osarmor_setup_1.4_test67.exe" )
2018-05-29 18:36:02,2964,C:\testy\osarmor_setup_1.4_test67.exe,53,Allowed ;Execution of an application ("C:\Users\xxx\AppData\Local\Temp\is-1CBGV.tmp\osarmor_setup_1.4_test67.tmp" /SL5="$220426,8243353,57856,C:\testy\osarmor_setup_1.4_test67.exe" )
2018-05-29 18:36:09,2448,C:\Users\xxx\AppData\Local\Temp\is-1CBGV.tmp\osarmor_setup_1.4_test67.tmp,26,Blocked ;Modifying protected registry key (HKLM\SYSTEM\ControlSet001\Control,ServicesPipeTimeout)"
...
But back to your question - I've checked what will happened when we make denied user folder/folders...because of my Vista I've used to make deny whole folder "C:\Users\my_name\"...and actualy nothing interresting have happened with usual (installed) apps - it looks that they still work properly. Some interresting things I found when tried to install new app using .exe installator - in my case it was NVT OSArmor - insttalation process was broken with special system alert...see screenshot
...
I attached some lines from log file of SS to show such issue
"2018-05-29 18:33:51,2192,C:\Moje programy\FreeCommander\FreeCommander.exe,53,Allowed ;Execution of an application ("C:\testy\unetbootin-windows-661.exe" )
2018-05-29 18:34:01,2192,C:\Moje programy\FreeCommander\FreeCommander.exe,53,Allowed ;Execution of an application ("C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe" )
2018-05-29 18:34:01,4060,C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe,50,Blocked ;Accessing the network via DNS Resolver service
2018-05-29 18:34:01,4060,C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe,48,Blocked ;Outgoing network access
2018-05-29 18:34:15,4060,C:\Users\xxx\AppData\Local\Temp\FreeCommander2192\2\CPix.exe,26,Blocked ;Modifying protected registry key (HKLM\SOFTWARE\Classes\CPix.bmpfile\shell\open\command,)
2018-05-29 18:35:42,2000,C:\Windows\System32\taskeng.exe,53,Allowed ;Execution of an application (C:\Windows\system32\wermgr.exe -queuereporting)
2018-05-29 18:36:02,2192,C:\Moje programy\FreeCommander\FreeCommander.exe,53,Allowed ;Execution of an application ("C:\testy\osarmor_setup_1.4_test67.exe" )
2018-05-29 18:36:02,2964,C:\testy\osarmor_setup_1.4_test67.exe,53,Allowed ;Execution of an application ("C:\Users\xxx\AppData\Local\Temp\is-1CBGV.tmp\osarmor_setup_1.4_test67.tmp" /SL5="$220426,8243353,57856,C:\testy\osarmor_setup_1.4_test67.exe" )
2018-05-29 18:36:09,2448,C:\Users\xxx\AppData\Local\Temp\is-1CBGV.tmp\osarmor_setup_1.4_test67.tmp,26,Blocked ;Modifying protected registry key (HKLM\SYSTEM\ControlSet001\Control,ServicesPipeTimeout)"
SS allows execution but applies the restrictions to executed programs from denied folders.
The question is if it applies all possible restrictions (I suspect so). From your log it follows, that the below actions were blocked:
Accessing the network via DNS Resolver service
Outgoing network access
Modifying protected registry key
I suspect that executing some other applications, you would also see other actions blocked (there are many left). Another question is if it possible to exclude some blocked actions for the concrete program, for example allowing to modify protected registry keys by OSArmor.
If so, then SS could be really used to protect all UserProfile and other user folders/partitions/disks by adopting a light sandbox for any program trying to execute from those locations.
Last edited:
I made a quick SpyShelter test. There are two different ways of applying SS restrictions to folders/subfolders:
.
Sadly for the point 1 solution, I could not change restrictions of the concrete program located in such folders or exclude subfolders. So this solution has limited usability as default-deny protection for the UserProfile.
.
Exclusions are possible for the point 2 solution via the options 'Exclude file' or 'Exclude folder'.
So, this could be used to apply a kind of smart-default-deny security based on restrictions in the light sandbox. It shows 'All general actions' set to Deny for the program located in a denied location, but anyway allows Hard disk access. So, only some restrictions are applied, and the user cannot choose Custom option to activate all possible restrictions.
- Restricted apps list -> choose folder
- Rules -> Exclude folder -> choose folder to exclude -> Make it denied
.
Sadly for the point 1 solution, I could not change restrictions of the concrete program located in such folders or exclude subfolders. So this solution has limited usability as default-deny protection for the UserProfile.
.
Exclusions are possible for the point 2 solution via the options 'Exclude file' or 'Exclude folder'.
So, this could be used to apply a kind of smart-default-deny security based on restrictions in the light sandbox. It shows 'All general actions' set to Deny for the program located in a denied location, but anyway allows Hard disk access. So, only some restrictions are applied, and the user cannot choose Custom option to activate all possible restrictions.
Last edited:
Yes...you are right that some other actions can be blocked autmaticaly but perhaps it needs time, patience and diferent apps to see something moreSS allows execution but applies the restrictions to executed programs from denied folders.
The question is if it applies all possible restrictions (I suspect so). From your log it follows, that the below actions were blocked:
Accessing the network via DNS Resolver service
Outgoing network access
Modifying protected registry key
I suspect that executing some other applications, you would also see other actions blocked (there are many left). Another question is if it possible to exclude some blocked actions for the concrete program, for example allowing to modify protected registry keys by OSArmor.
If so, then SS could be really used to protect all UserProfile and other user folders/partitions/disks by adopting a light sandbox for any program trying to execute from those locations.
Exclusion of some action in case "excluded folder" aren't possible for both decision (allow-block)...you can't open advanced rules editor. But I think...it's only speculation...that you can add OSArmor to trusted signers list and by this way use another feature which you can find on the list of monitored actions (Settings/List of monitored...). There you can see empty box called "Auto-allow action for a component signed by a trusted signer"...if you tick it "on" you automaticaly allow all monitored action to be allowed and now you should manualy edit each one and make it "yes" or "no". I think priority of that settings is higher than rules made automaticaly while using app and detecting new actions that should be blocked.
Your way #2 is for me a bit "tricky" and actualy not well checked and documented...so it's rather "proof of concept" that needs to be deeper researched. That's why I'm sticking rather to #1 which is for me used for some time.
BTW...thansk for such interresting and explorative discuss
The way #2 is probably weaker than #1, so it is better to stick with #1.Yes...you are right that some other actions can be blocked autmaticaly but perhaps it needs time, patience and diferent apps to see something more
Exclusion of some action in case "excluded folder" aren't possible for both decision (allow-block)...you can't open advanced rules editor. But I think...it's only speculation...that you can add OSArmor to trusted signers list and by this way use another feature which you can find on the list of monitored actions (Settings/List of monitored...). There you can see empty box called "Auto-allow action for a component signed by a trusted signer"...if you tick it "on" you automaticaly allow all monitored action to be allowed and now you should manualy edit each one and make it "yes" or "no". I think priority of that settings is higher than rules made automaticaly while using app and detecting new actions that should be blocked.
Your way #2 is for me a bit "tricky" and actualy not well checked and documented...so it's rather "proof of concept" that needs to be deeper researched. That's why I'm sticking rather to #1 which is for me used for some time.
BTW...thansk for such interresting and explorative discuss
Surprised I hadn't replied yet, but the answer is.... Yes.
Keep in mind Windows is not the only operating system, there is Linux, macOS, Android and iOS - the main ones.
You don't need latest and best $100 "Security Suites", but something to aid your existing security and knowledge is sufficient.
Additional security measures and safeguards may be required for business devices and networks.
I'll await someone to moan about the Average Joe not knowing the difference between Recovery and Backup.
Keep in mind Windows is not the only operating system, there is Linux, macOS, Android and iOS - the main ones.
You don't need latest and best $100 "Security Suites", but something to aid your existing security and knowledge is sufficient.
- Router + Hardware Firewall + Secure Wireless network
- Latest OS + Security Updates
- Modern Browser + Content Blocker
- Real-time Security
- Encryption + Backup
- Emergency Recovery
Additional security measures and safeguards may be required for business devices and networks.
I'll await someone to moan about the Average Joe not knowing the difference between Recovery and Backup.
So, What do you think about this combo?
HMPA + H_C with srp on + SysHardener (or OSArmor)
Virustotal app to check files if needed.
Optional: Firewall with strict default deny rules.
I feel antivirus is just useless with good habits and legal software and gives false sense of security
HMPA + H_C with srp on + SysHardener (or OSArmor)
Virustotal app to check files if needed.
Optional: Firewall with strict default deny rules.
I feel antivirus is just useless with good habits and legal software and gives false sense of security
F
ForgottenSeer 823865
good enough, almost my old combo (but with AppGuard instead of H_C) when i was using HMPA.HMPA + H_C with srp on + SysHardener (or OSArmor)
Virustotal app to check files if needed.
Too complex and asking to break Windows Updates.So, What do you think about this combo?
HMPA + H_C with srp on + SysHardener (or OSArmor)
Virustotal app to check files if needed.
Optional: Firewall with strict default deny rules.
I feel antivirus is just useless with good habits and legal software and gives false sense of security
They are important because many users can't tell whether or not a particular file should be run, malware is sometimes hidden in ads or parts of web pages in legit websites, etc.
You may also like...
-
Serious Discussion Antivirus vs. Common Sense — What Really Keeps You Safe in 2025?
- Started by Bot
- Replies: 105
-
Advice Request Best Antivirus for my Family
- Started by KnownStormChaser
- Replies: 172
-
App Review PCMatic Antivirus Home 2026
- Started by Shadowra
- Replies: 12
-
Poll Paid vs Free Antivirus in 2026: What are you using, and is it worth paying for?
- Started by Bot
- Replies: 96
