Test Link: https://brax.me/geo/
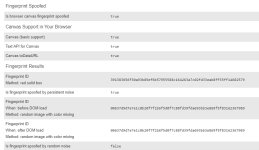
Rob Braxman Tech said:Brave Browser was revised in 2020 and received a slew of features related to better defense against browser fingerprinting. Or at least that's the claim. In this video we put this to a test, by actually attempting to fingerprint a Brave Browser session in different circumstances while we also theorize some possible ways to evade the defense.
In the end we will figure out exactly what Brave does differently from other browsers and we will see if it lives up to the hype. Is it unbeatable by a browser fingerprint tracker? Or is it flawed?
Find out the results of the actual test. We also compare it to Chrome and Firefox using default settings on those browsers.