- Dec 27, 2016
- 1,480
Call it "Essential Security against Evolving Threats", "Nemocnica na Okraji Disku" or just "ESET", a theophoric name derived from an Egyptian goddess. ESET Nod has been a favorite of many users worldwide since 1992.
A month back, I gave ESET a revisit after a long time. And it has been my Kaspersky alternative for a while now.
Before we plunge into the the review, let's talk about the multi-layered ESET Technology for a bit. Shall we?
The awfully amazing (+)

ESET through the eyes of a user -->
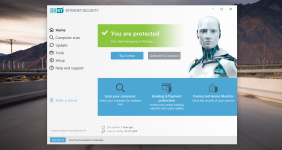
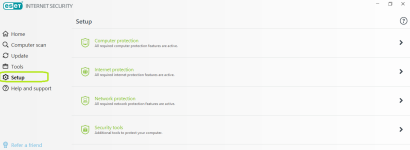
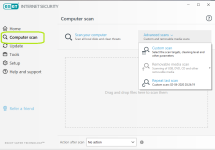
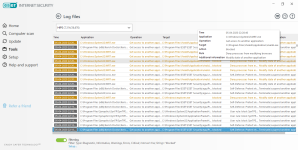
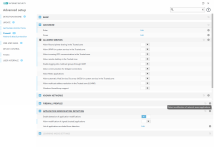
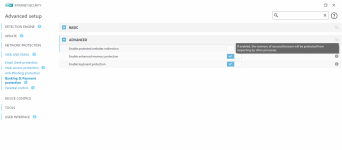
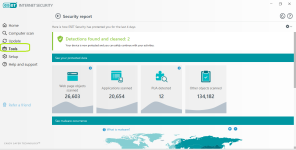
Overview
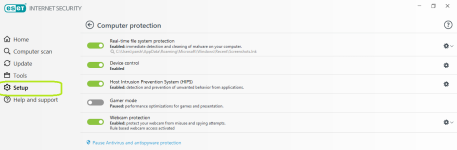
Computer protection
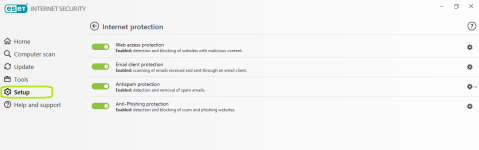
Internet protection
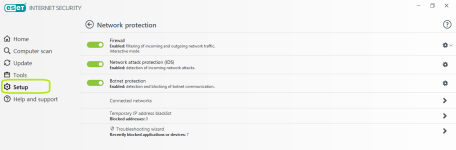
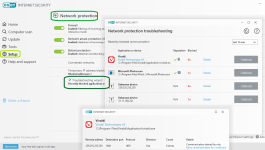
Network protection
Privacy protection
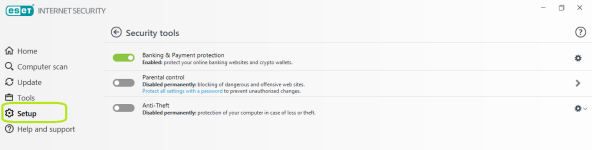
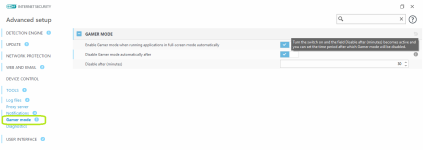
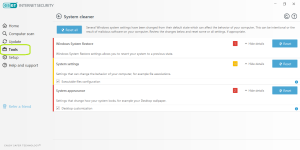
Security tools
Uhm ...,
A month back, I gave ESET a revisit after a long time. And it has been my Kaspersky alternative for a while now.
It's a self-taught warrior. Mind you, a very intelligent one. However, it might need an additional push from the master (experienced user) to unleash the beast on the battlefield!
Generalized as below
Generalized as below
| novice / users wanting automated simplicity | novice with ^ learning appetite / advanced users wanting control | |
| Experience | 9.5/10 | 9/10 |
| Security fulfillment | 9.5/10 | 9.5/10 |
| Security protection | 8.5/10 | 9/10 |
| Security tools | 9/10 | 9.5/10 |
Amazing facts? Nah. But a good read about some technical jargons and wizardry.
What are some benefits of ESET's core technology?
ESET had been using interpreted assembly code that would execute on emulated resources like the CPU.
To further improve the performance, sandboxing now uses "binary translation" together with "interpreted emulation" that can be done on the real CPU.
What exactly is DNA Detection in ESET?
DNA detection carry genes - complex definitions of malicious behavior and malware characteristics, extracted by performing deep analysis of code. This arguably carries more valuable data compared to IOCs some next-gen solutions boast of using. You could call it advanced heuristics.
The scanning engine also extracts many discriminator genes used for anomaly detection - anything which does not look legitimate is potentially malicious.
Thus, DNA can detect known & unknown malware families that contain characteristics matching these "extracted" genes.
New malicious genes/patterns are also extracted using cloud ML analysis, and are matched with a whitelist to not generate FPs.
DNA detection can use ML models both online and offline.
So is DNA Detection "the" dynamic protection?
There are primarily 2 types of "code analysis" - static and dynamic.
Static analysis mainly uses traditional hashes and pattern matching without execution.
Dynamic analysis uses an in-product sandbox/emulator to emulate files or parts of them. Emulator unpacks files and monitors behavior (compares with DNA genes) using DNA detections. Thus, polymorphic and obfuscated malware can be analysed by DNA detection.
Nowadays, static analysis is used in combination with dynamic analysis. The idea is to emulate the execution of an application in a secure virtual environment before it actually runs on the machine.
Does that mean DNA is different than the Deep Behavioral Inspection?
According to ESET, yes. Their Behavioral Inspection is said to be an extension of HIPS that monitors the behavior of running programs and alerts of any suspicious "activity".
Recently added, the DBI includes new detection heuristics and enables deep user-mode monitoring of unknown, suspicious processes. This is done via hooks created within unknown, potentially harmful processes and monitoring of their activity and requests to the OS. If malicious behavior is detected, DBI mitigates the activity and informs the user. If the process is suspicious, but does not show clear signs of malice, HIPS can also use the data gathered by DBI to run further analysis via its other modules.
We've read about the memory scanners in such AVs. That's some more cream?
Highly obfuscated and encrypted malware may be difficult to detect through even emulators or sandboxing, or they may not exhibit malicious behavior due to their preventive - timing and technical sophistication. Advanced Memory Scanning monitors in-memory app behavior using DNA analysis. It works in conjunction with the Exploit Blocker. AMS thus detects malicious code as it unveils its true colors (only) in memory.
So the exploit protection ...?
The scanning engine covers exploits in malformed document files, Network Attack Protection in FW targets the communication level, and finally the Exploit Blocker blocks the exploitation process itself.
Heard it got HIPS?
HIPS is a detection technology specifically created to monitor and scan behavioral events from running processes, files and registry keys, looking for suspicious activity. Self-defense mechanism uses pre-defined rules to analyse and stop potentially malicious activities.
The members include
Ransomware are greeted with ...?
A Ransomware Shield behavior monitor that works in conjunction with Cloud Malware Protection System, Network Attack Protection and DNA Detections.
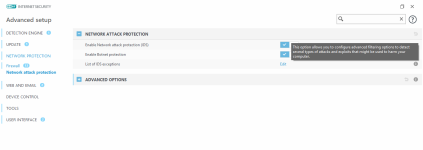
Can we expect Network Protection from these suites, over standalone alternatives or their AV versions?
Industry standard signatures like Snort or Bro allow detection of many attacks, but ESET Network Detections are specifically designed to target network vulnerabilities, exploit kits, and communication by advanced malware in particular, including encrypted communication sometimes. Firewall integration with the AV also helps detect the bandit process.
And the Cloud thing?
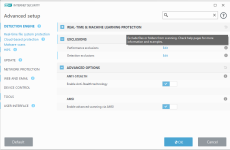
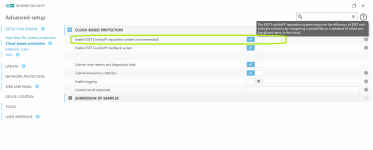
The LiveGrid Reputation System uses behavior gene hashing instead of traditional data hashing to detect new malware. It contains info about analysed files, their origins, similarities, certificates, URLs and IPs.
ESET Cloud based on LiveGrid, takes suspicious/unknown samples --> subjects them to auto-sandboxing (physical & virtual) and behavioral analysis in cloud --> automated detection (~ 20mins). These automated detections are usable via LiveGrid w/o needing to wait for the next detection engine update.
What about that fancy ML stuff?
ESET has been using ML since before 2000. The newly integrated Augur uses neural networks and 6 classification algorithms.
Classification is done using attributes extracted during execution according to static/dynamic code analysis, changes to OS, network communication patterns, similarity to other malware, DNA features, structural information and anomaly detection. However, every such automation comes with a hoard of drawbacks due to factors like lack of human input, diverse/imbalanced class of data fed into the system, snowballing... Here, detection engineers play a small role in balancing.
Let's end with an amazing fact?
ESET Botnet protection detects malicious communications (sure it does, so what?)
While their Online Tracker system extracts samples or malicious dumps from endpoints, contextually explores and tries to identify their C&C server keys, initiates fake connections to them and uses the new leads to protect all ESET customers worldwide.
What are some benefits of ESET's core technology?
ESET had been using interpreted assembly code that would execute on emulated resources like the CPU.
To further improve the performance, sandboxing now uses "binary translation" together with "interpreted emulation" that can be done on the real CPU.
What exactly is DNA Detection in ESET?
DNA detection carry genes - complex definitions of malicious behavior and malware characteristics, extracted by performing deep analysis of code. This arguably carries more valuable data compared to IOCs some next-gen solutions boast of using. You could call it advanced heuristics.
The scanning engine also extracts many discriminator genes used for anomaly detection - anything which does not look legitimate is potentially malicious.
Thus, DNA can detect known & unknown malware families that contain characteristics matching these "extracted" genes.
New malicious genes/patterns are also extracted using cloud ML analysis, and are matched with a whitelist to not generate FPs.
DNA detection can use ML models both online and offline.
So is DNA Detection "the" dynamic protection?
There are primarily 2 types of "code analysis" - static and dynamic.
Static analysis mainly uses traditional hashes and pattern matching without execution.
Dynamic analysis uses an in-product sandbox/emulator to emulate files or parts of them. Emulator unpacks files and monitors behavior (compares with DNA genes) using DNA detections. Thus, polymorphic and obfuscated malware can be analysed by DNA detection.
Nowadays, static analysis is used in combination with dynamic analysis. The idea is to emulate the execution of an application in a secure virtual environment before it actually runs on the machine.
Does that mean DNA is different than the Deep Behavioral Inspection?
According to ESET, yes. Their Behavioral Inspection is said to be an extension of HIPS that monitors the behavior of running programs and alerts of any suspicious "activity".
Recently added, the DBI includes new detection heuristics and enables deep user-mode monitoring of unknown, suspicious processes. This is done via hooks created within unknown, potentially harmful processes and monitoring of their activity and requests to the OS. If malicious behavior is detected, DBI mitigates the activity and informs the user. If the process is suspicious, but does not show clear signs of malice, HIPS can also use the data gathered by DBI to run further analysis via its other modules.
We've read about the memory scanners in such AVs. That's some more cream?
Highly obfuscated and encrypted malware may be difficult to detect through even emulators or sandboxing, or they may not exhibit malicious behavior due to their preventive - timing and technical sophistication. Advanced Memory Scanning monitors in-memory app behavior using DNA analysis. It works in conjunction with the Exploit Blocker. AMS thus detects malicious code as it unveils its true colors (only) in memory.
So the exploit protection ...?
The scanning engine covers exploits in malformed document files, Network Attack Protection in FW targets the communication level, and finally the Exploit Blocker blocks the exploitation process itself.
Heard it got HIPS?
HIPS is a detection technology specifically created to monitor and scan behavioral events from running processes, files and registry keys, looking for suspicious activity. Self-defense mechanism uses pre-defined rules to analyse and stop potentially malicious activities.
The members include
- Advanced Memory Scanner (AMS)
- Exploit Blocker (EB)
- Ransomware Shield (RS)
- Deep Behavioral Inspection (DBI)
Ransomware are greeted with ...?
A Ransomware Shield behavior monitor that works in conjunction with Cloud Malware Protection System, Network Attack Protection and DNA Detections.
Can we expect Network Protection from these suites, over standalone alternatives or their AV versions?
Industry standard signatures like Snort or Bro allow detection of many attacks, but ESET Network Detections are specifically designed to target network vulnerabilities, exploit kits, and communication by advanced malware in particular, including encrypted communication sometimes. Firewall integration with the AV also helps detect the bandit process.
And the Cloud thing?
The LiveGrid Reputation System uses behavior gene hashing instead of traditional data hashing to detect new malware. It contains info about analysed files, their origins, similarities, certificates, URLs and IPs.
ESET Cloud based on LiveGrid, takes suspicious/unknown samples --> subjects them to auto-sandboxing (physical & virtual) and behavioral analysis in cloud --> automated detection (~ 20mins). These automated detections are usable via LiveGrid w/o needing to wait for the next detection engine update.
What about that fancy ML stuff?
ESET has been using ML since before 2000. The newly integrated Augur uses neural networks and 6 classification algorithms.
Classification is done using attributes extracted during execution according to static/dynamic code analysis, changes to OS, network communication patterns, similarity to other malware, DNA features, structural information and anomaly detection. However, every such automation comes with a hoard of drawbacks due to factors like lack of human input, diverse/imbalanced class of data fed into the system, snowballing... Here, detection engineers play a small role in balancing.
Let's end with an amazing fact?
ESET Botnet protection detects malicious communications (sure it does, so what?)
While their Online Tracker system extracts samples or malicious dumps from endpoints, contextually explores and tries to identify their C&C server keys, initiates fake connections to them and uses the new leads to protect all ESET customers worldwide.
Modules -->
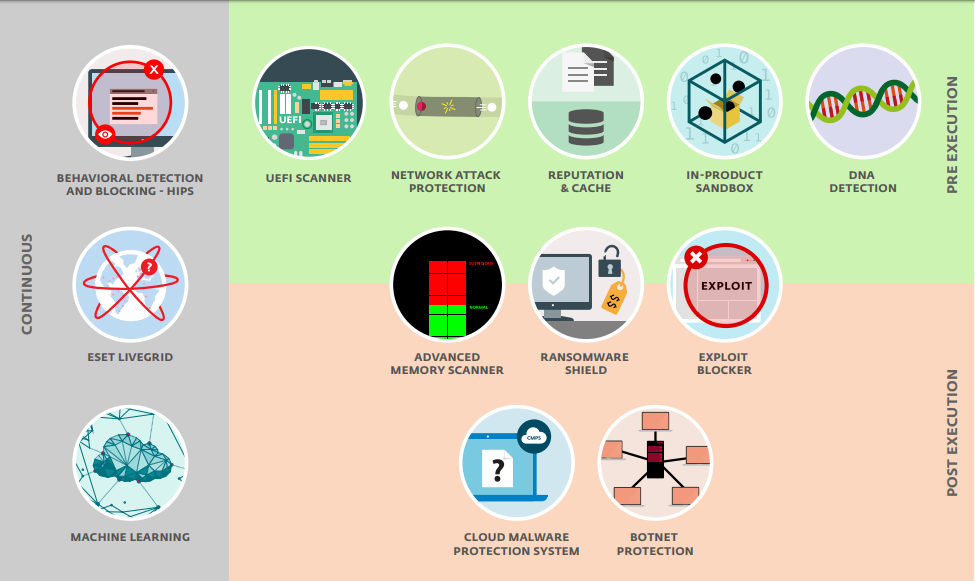
Behavioral detection -->
(1)
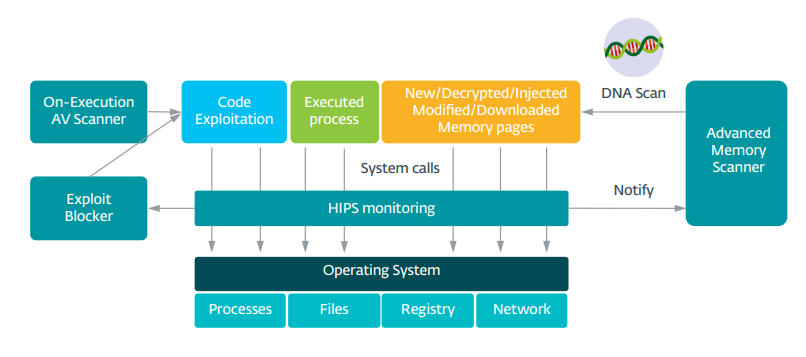
(2)
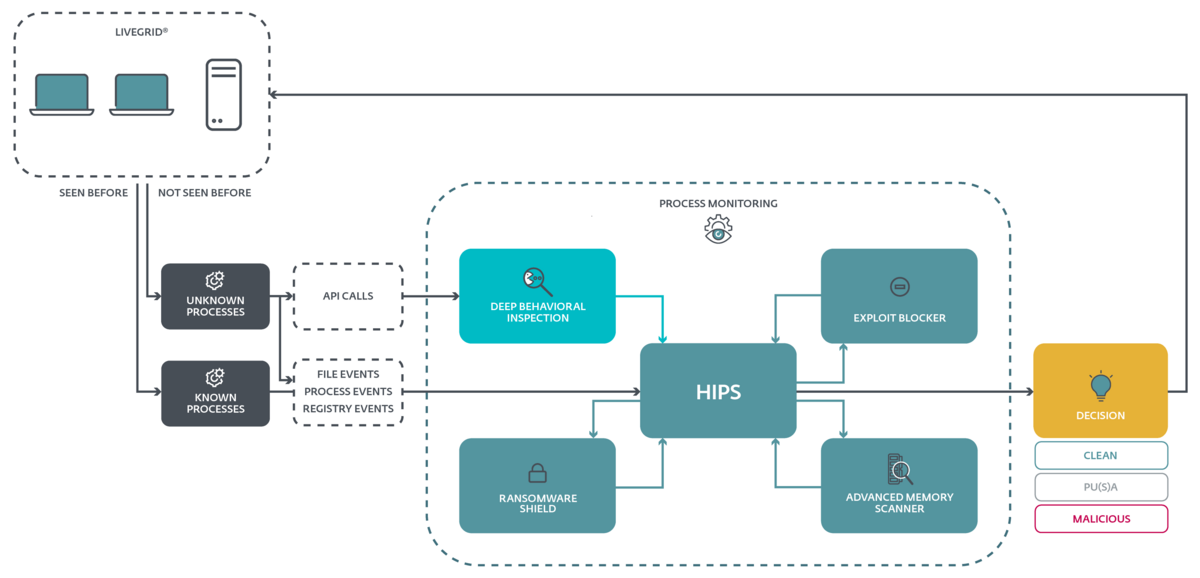
In-product sandbox principle -->
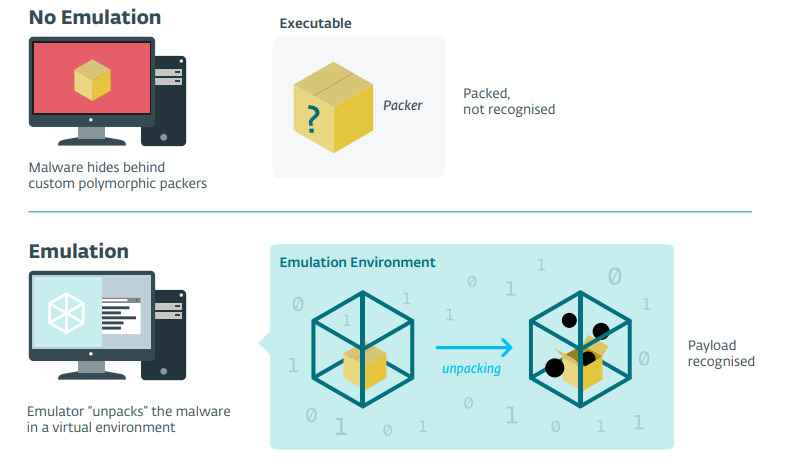
Augur ML scheme -->
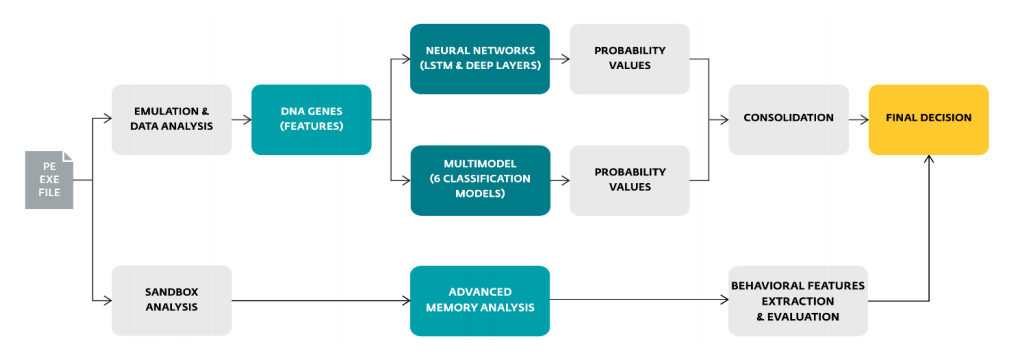
PS: Did you know that viewing diagrams of a product of interest (like this or that) subconsciously draws you towards its features and finally to the product?
Behavioral detection -->
(1)
(2)
In-product sandbox principle -->
Augur ML scheme -->
PS: Did you know that viewing diagrams of a product of interest (like this or that) subconsciously draws you towards its features and finally to the product?
The awfully amazing (+)
- Usability
- Automated
- Lightest AV perhaps
- HIPS and FW alerts - detailed and flexible
- Customizable notifications
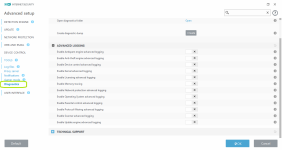
- Advanced logging
- HIPS & FW at learning mode - useful to auto-create safe rules (not for continuous use)
- HIPS & FW at policy mode - block all non-configured actions (for designated environments)
- Security
- Highly multi-layered protection with tight coupling
- Signatures among the best + Augur ML engine
- 3rd largest market share of 12.4% - hence expected to have a huge data intelligence
- Overall very good real-time protection (independent tests)
- Pioneer to provide UEFI boot scan
- Memory scanning & fileless malware protection is noteworthy (some independent tests)
- Highly customizable levels of real-time file-system protection
- PUP/PUA detection among the best
- Perhaps the highest configurable FW in a consumer AV
- FW at automatic mode is decent
- FW at interactive mode can be very useful (for advanced users)
- FW alerts offer reverse DNS (displays the domain name associated with the IP) (Kaspersky offers experimental domain based rules) *
- Detects app modification and alerts to re-configure FW rules
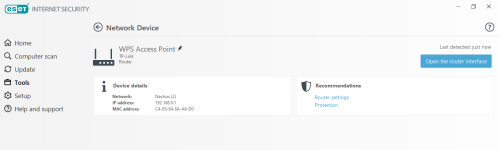
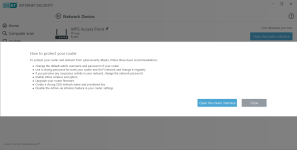
- Router vulnerability scanner
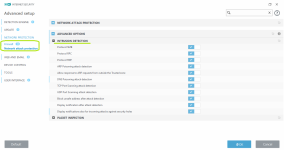
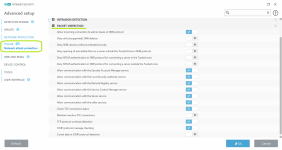
- Highly configurable IDS
- Highly configurable web (especially HTTPS) protection
- SysInspector to compare system snapshots
- Device control + basic tools for system and network monitoring
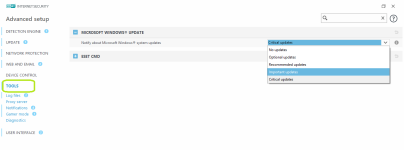
- Alerts for Windows updates
- Privacy
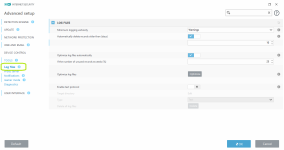
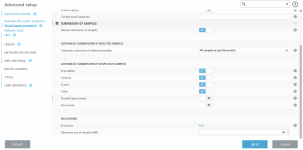
- Can customize the type + size of files uploaded for analysis, can set exceptions
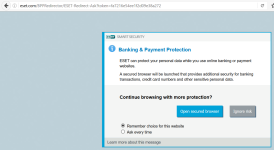
- Safe browser for Banking & Payment Protection
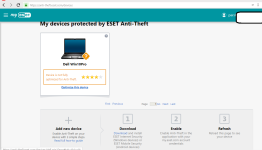
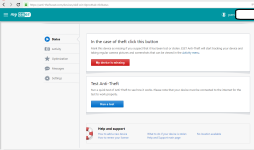
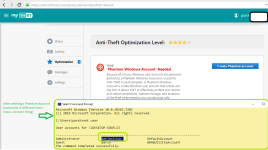
- Anti Theft via portal (uses a phantom account)
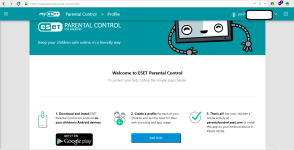
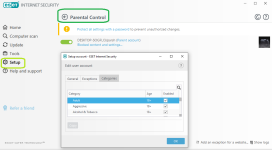
- Parental Control via portal and suite settings
- Social Media Scanner via portal
- Usability
- Settings can be overwhelming for an average user
- Sometimes the "notify" feature on blocked actions (by HIPS) does not work, you would have to refer to logs when doubtful
- No wildcard support in HIPS rules (for advanced users)
- Need to answer additional UAC prompt while saving FW rules via an alert
- HIPS in interactive mode (advanced users) --> might be difficult to handle
- FW in interactive mode (advanced users) --> if you rely on IPs for allowing, alerts can be overwhelming. Would be less practical/safe to find/set a range of IP's (unless surely known) to the allowed rules for an app
- HIPS does not indicate the wrong input when alerting of incorrectly set rules
- Anti-theft's phantom account name on Windows does not match the user-assigned name via portal
- Security
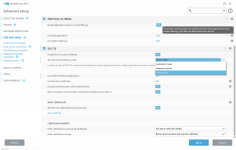
- "Ask alert" of HIPS auto-allows action if user does not respond within 1min
- HIPS modes (without user-defined rules) -->
- Default mode of HIPS auto-allows most actions
- Smart mode is less vocal about suspicious activities
- No App Control based on reputation, cannot be used as default-deny (for advanced users)
- Known to be weaker against unknown malware (not detected by signatures/DNA) at default settings
- Ransomware protection slightly on weaker side thanks to the above point (HIPS rules can be set to protect important data)
- Known to reduce reporting of suspicious detection to user - to highly reduce FP's
- Privacy
- Banking Protection supports only IE, Chrome and Firefox. Chromium browsers not supported
- No VPN option (really nothing much)
- Your novice friends
- Users tired of advanced witchcraft configs
- Gaming PC companion
- People usually on the move with their machines
- For your spouse or kids
- For your (grand) parents living miles away
- People using anti-exes / SRP, and alongside need a chilled out AV
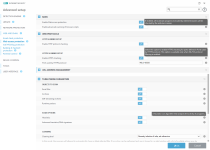
ESET through the eyes of a user -->
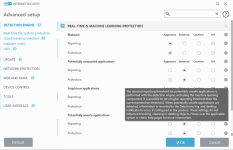
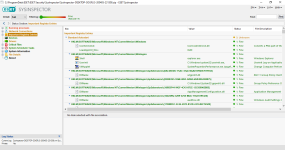
Overview
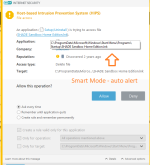
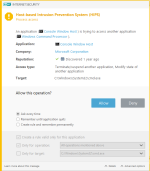
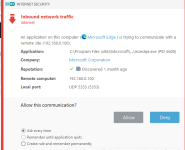
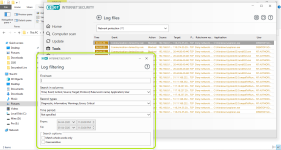
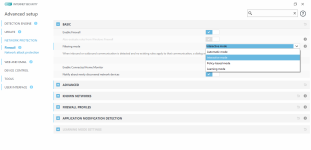
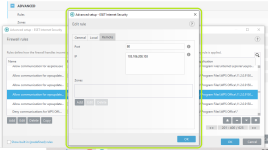
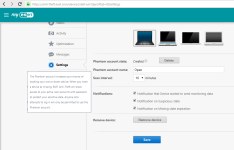
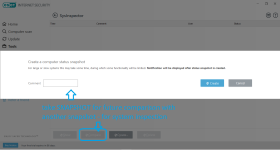
HIPS modes
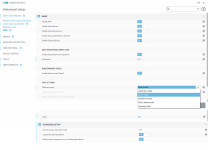
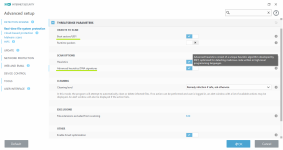
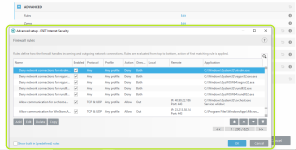
HIPS Rules screen
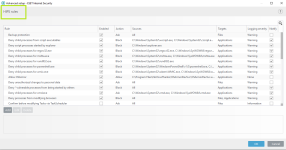
Setting rules
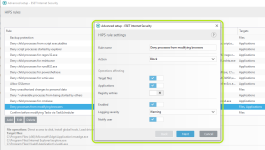
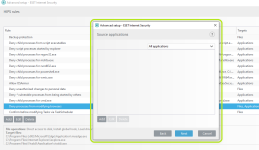
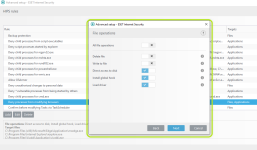
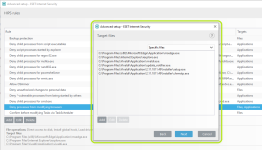
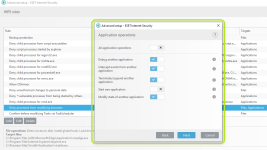
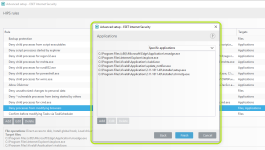
*Please note that when creating a (generalized) rule for blocking some activity, make sure to create another (special) rule, to specifically allow good exceptions.
Example if you block all processes from starting/modifying your browser, allow the browser process (and updater) to start/modify itself as a required exception.

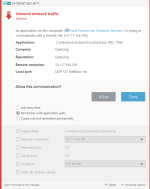
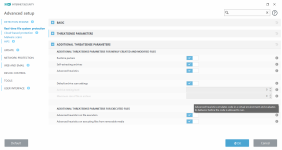
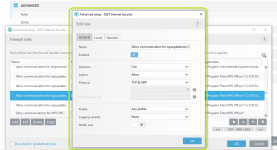
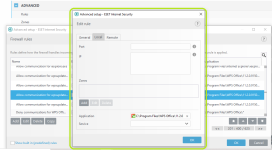
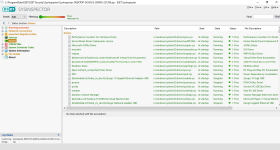
HIPS Rules screen

Setting rules






*Please note that when creating a (generalized) rule for blocking some activity, make sure to create another (special) rule, to specifically allow good exceptions.
Example if you block all processes from starting/modifying your browser, allow the browser process (and updater) to start/modify itself as a required exception.
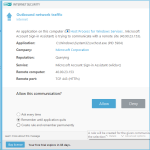
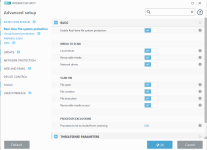
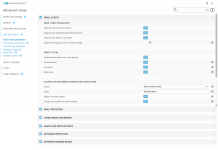
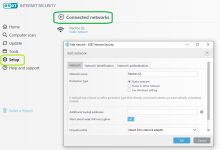
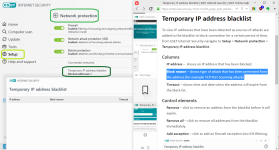
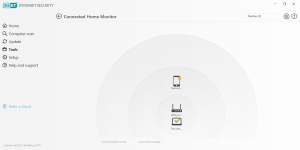
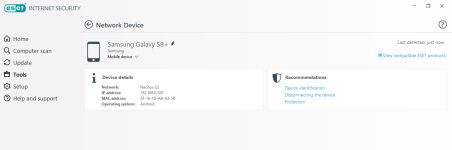
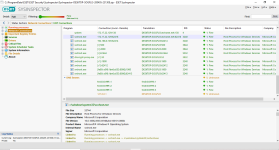
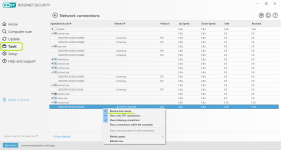
Network protection
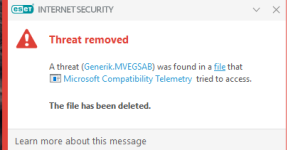
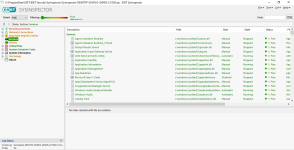
Privacy protection
It's me. Like me or not, you cannot ignore me. You are going to see my face in the forefront for many coming years - my garnered intelligence predicts!

See you around
See you around
Last edited: