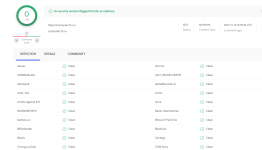
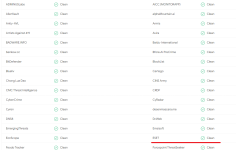
A year has passed since I installed Eset Internet Security. I have not used this product before, but now I already have a certain idea about it. A fairly easy product for system resources compared to the antiviruses that I used before (I had Avast for 6 years, then free Kaspersky for a year, then paid for another year, and again free for half a year). A couple of times Eset blocked my access to sites (he defined one site as malicious, the other site as containing PUPs). In fact, the "dangerous" site does not contain any dangerous things  I calmly entered it from other PCs and read articles there (this is a site on computer security, programs, settings, in general about computers and the Internet). But the site is included in the internal blacklist of Eset and Eset is not allowed there in any way, even if it is included in the exceptions
I calmly entered it from other PCs and read articles there (this is a site on computer security, programs, settings, in general about computers and the Internet). But the site is included in the internal blacklist of Eset and Eset is not allowed there in any way, even if it is included in the exceptions  Perhaps this is all that Eset web protection has remembered for a year
Perhaps this is all that Eset web protection has remembered for a year 
The antivirus did not deliver any global problems in a year of use.
It is definitely disappointing that some of the stagnation in development that other users have noted is disappointing. So, for example, the LiveGuard function was introduced only in the premium version, and the new version of Internet Security was left without new functions at all. The developers are clearly trolling users when the award received from AV-Comparatives in 2020 is indicated as a new function for the antivirus Internet Security.
It is also disappointing that the "Network Inspector" is designated as a "new" function for Internet Security version 15, while this very name "Network Inspector" has already appeared in version 14, and has already performed the same functions. Although, the official forum has already written the position of the developers that they think that users almost never look at the interface. It turns out that you can write that a new function was introduced, although in fact it has been around for a long time
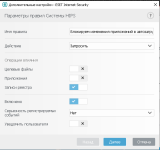
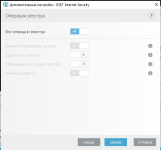
Once again, there is nothing to say about HIPS. Everything has already been said on the official forum, here on the forum, and more than once.
I would like to wish the antivirus real development (and not only "cosmetic" changes), and the developers - to listen to the opinions of users.
The antivirus did not deliver any global problems in a year of use.
It is definitely disappointing that some of the stagnation in development that other users have noted is disappointing. So, for example, the LiveGuard function was introduced only in the premium version, and the new version of Internet Security was left without new functions at all. The developers are clearly trolling users when the award received from AV-Comparatives in 2020 is indicated as a new function for the antivirus Internet Security.
It is also disappointing that the "Network Inspector" is designated as a "new" function for Internet Security version 15, while this very name "Network Inspector" has already appeared in version 14, and has already performed the same functions. Although, the official forum has already written the position of the developers that they think that users almost never look at the interface. It turns out that you can write that a new function was introduced, although in fact it has been around for a long time
Once again, there is nothing to say about HIPS. Everything has already been said on the official forum, here on the forum, and more than once.
I would like to wish the antivirus real development (and not only "cosmetic" changes), and the developers - to listen to the opinions of users.