I heard ESET uses Microsoft's Azure AI servers for EDTD, not their own.
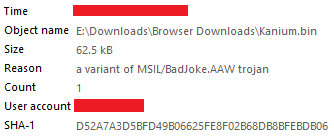
The earlier sample also wasn't detected by Microsoft Defender. The initial cloud scan found some malicious behavior in it, but it wasn't the final determination. Then I uploaded that to Microsoft and a few hours later Microsoft started detecting via cloud and my submission showed the Final determination status as malicious.
The malware that you shared here now is also not detected by Microsoft Defender at the moment and I think as a result also not by ESET Dynamic Threat Defense.
There was another fairly new sample that was tested by someone that wasn't detected by any of the popular AVs on Virustotal except Microsoft Defender. That sample was then detected by ESET's LiveGuard on ESET Smart Security.
So now everything points to what I heard. This ESET Dynamic Threat Defense aka LiveGuard is not ESET's own technology.
It's Microsoft's Azure AI sandbox, or whatever that is called. If Microsoft's cloud don't detect something, then ESET's EDTD/LiveGuard won't.
(Correct me if I'm wrong).
Edit: Microsoft won't do any more analysis of it. They did it before and confirms that this is not malicious
 View attachment 262440
View attachment 262440