Right and once trained adequately you get very few pop-ups except when you install or run something new. I used the prior stable for some time and had very few pop-ups. That is what it is supposed to do.
EXE Radar Pro v4 (Beta)
- Thread starter NoVirusThanks
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Avast and EXE Rader Pro v4(beta1) is gel together.No problem so far.
Hi All,
Can anyone please let me know how I change this to a wildcard
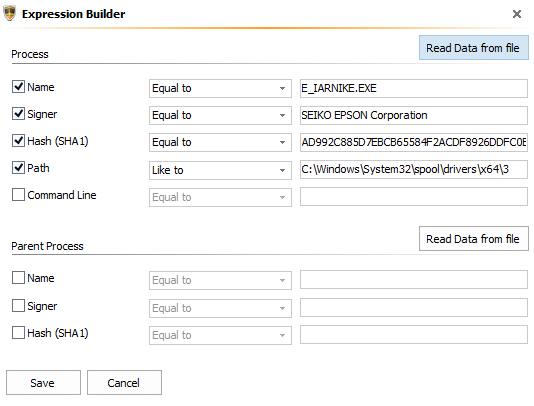
Thanks
Andy
Can anyone please let me know how I change this to a wildcard
Thanks
Andy
Can anyone please let me know how I change this to a wildcard
Do you want any .exe program say in program files area to be able to access the driver file? I think you would need to add a wildcard for the parent, such as Path->C:\Program Files\* (Don't see the path option on the menu however). Then maybe you would need to add one for C:\Windows\*. I am guessing this is so your printer will initialize when used with various programs. Looks like you could allow anything signed by adding a * to the Parent i.e.->Parent->Signer->*. Just guessing...
Yes,Do you want any .exe program say in program files area to be able to access the driver file? I think you would need to add a wildcard for the parent, such as Path->C:\Program Files\* (Don't see the path option on the menu however). Then maybe you would need to add one for C:\Windows\*. I am guessing this is so your printer will initialize when used with various programs. Looks like you could allow anything signed by adding a * to the Parent i.e.->Parent->Signer->*. Just guessing...
As long as it doesn't comprise security - what would I need to do then ?
I have the default set of vulnerable processes imported which includes deny to icacls.exe in System 32 and SysWOW64. I have tried to whitelist the following two processes hoping that these are specific and would be allowed and that the two "general" vulnerable process would continue to function for anything non-specifically whitelisted.
Is this right
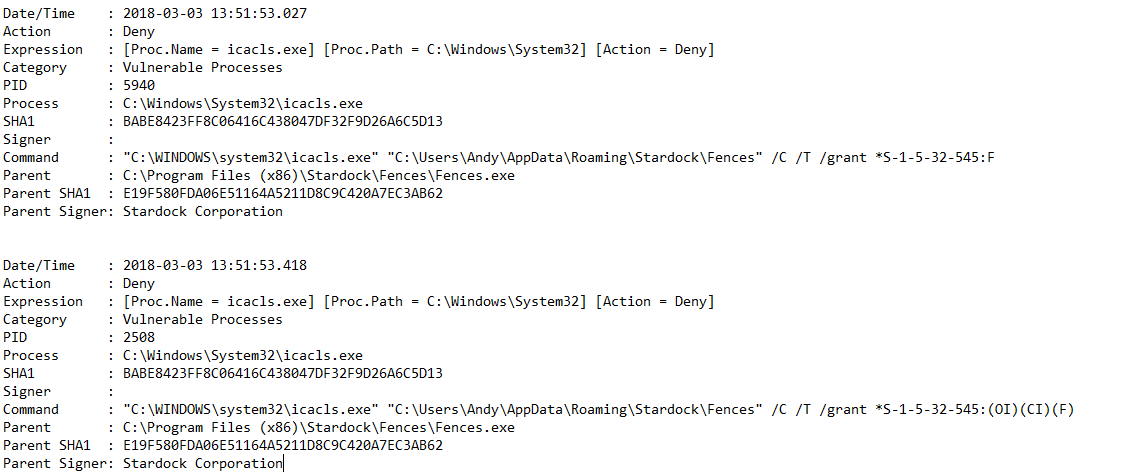
Is this right
Yes,
As long as it doesn't comprise security - what would I need to do then ?
Did you try the "Signer" = "*" rule? Looks to me like the best option for you might be to lobby NVT for the addition of a "Path" entry on the rule creation dialog. Maybe I am just not seeing it there. That would be best for security, so that .tmps or other strange places wouldn't have access to the folder. I hate to sacrifice even the least amount of security too, so I know where you are coming from with this concern. BTW, if you go with "Signer", I don't know how Windows apps would react. I think some of them are unsigned by design (?). However, if that's not a problem, the choice would mean that only signed applications could access the driver, which would be a start. Don't know, however, how ERP 4.0 would react to just a single * wildcard character for a rule choice in the "Signer" rule entry box.
Does "Read Data from file" give you any options or is that just a header for the group of options?
I have the default set of vulnerable processes imported which includes deny to icacls.exe in System 32 and SysWOW64. I have tried to whitelist the following two processes hoping that these are specific and would be allowed and that the two "general" vulnerable process would continue to function for anything non-specifically whitelisted.
Is this right
I have tried this kind of rule in 3.1 without much success with whitelisting. However, the power of whitelisting may have been extended in 4.0. Those rules look to me like they should do the job if the "*" will be recognized in that place in the string. Have you had a chance to test to see? If the rules work, you should get no alert from NVT over one of the icacls.exe processes being accessed by the StarDock program.
For the moment is have disabled the two vulnerable processes which have icacls.exe in them and all OK but not sure this should be the right way. I thought that if you added/whitelisted a vulnerable process with certain limitations like path/parent process that this would whitelist that particular process but the general vulnerable process would still be implemented elsewhere.
The main page even has three fields that have not been put into any language yet, as far as I can tell. I see that it says lorem ipsem, which is a latin text used as filler, until the real text is put in.yes, it is a beta so the main page will surely be translated later, it is not an urgent thing.
It is in settings: allow all microsoft signed, allow all signed, allow program files. You will have less prompts.Instead of alert mode what othe mode will give less prompts yet be safe?
But there will still be prompts from the VPL, especially from rundll32, because the dev did not yet write the list of command lines that Windows needs by default. ERP 3 had it, but as far as I can see, ERP 4 does not have it yet.
For the moment is have disabled the two vulnerable processes which have icacls.exe in them and all OK but not sure this should be the right way. I thought that if you added/whitelisted a vulnerable process with certain limitations like path/parent process that this would whitelist that particular process but the general vulnerable process would still be implemented elsewhere.
Yes, I should think so. This is exactly how it works in ERP 3.1. For example, if cmd.exe is used to run a command and I whitelist just the command, I will still get a prompt every time cmd.exe is referenced to be used...by any executable, even allowed ones. That's how it works with vulnerables. You get the chance to see the command line associated and blacklist it or whitelist it, etc.
Looks like with v4.0 you are just getting more options for whitelisting and then extended capablities for blacklisting also. I can see how it would be much more powerful for rule creation, although I guess it will be a bear to learn. Probably a challenge to make it understandable for NVT too I guess...
In ERP 3 there was command line whitelisting that only took a quick click or two. We need to get that back. We also need to get back the ability to whitelist command lines by learning mode.
In ERP 3 there was command line whitelisting that only took a quick click or two. We need to get that back. We also need to get back the ability to whitelist command lines by learning mode.
Sounds nice to me. Waiting to see where you guys go with the app, since I couldn't get it to fire on anything. Only had the vulnerable rules I think...
You are not the only one. @Peter2150 reported on the other forum that he did a test with a ransomware exe, and ERP 4 did not block it.Sounds nice to me. Waiting to see where you guys go with the app, since I couldn't get it to fire on anything. Only had the vulnerable rules I think...
ERP 4 is still in the early stages.
Here is a new v4.0 (pre-release) test2:
http://downloads.novirusthanks.org/files/exe_radar_pro_4_setup_test2.exe
*** Please do not share the download link, we will delete it when we'll release the official v4 ***
So far this is what's new compared to the previous pre-release:
+ Fixed writing of rules (matching of fields)
+ Fixed matching of wildcard characters (Like to) on rules
+ Fixed matching of parent process on rules
+ Fixed showing of main window on multi-monitors
+ Fixed showing of "Hide Main Window" on Tray Icon
+ Added option "Do not auto-close notification dialog" (when a process is blocked)
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
There were some issues on rules, please retry with this new build (should work fine now).
To use wildcards (? and * characters) just select "Like to" instead of "Equal to".
Wildcard works on all process fields (name, path, signer, etc).
I'll start creating a pre-built-whitelist of safe commands related to Vulnerable Processes asap.
http://downloads.novirusthanks.org/files/exe_radar_pro_4_setup_test2.exe
*** Please do not share the download link, we will delete it when we'll release the official v4 ***
So far this is what's new compared to the previous pre-release:
+ Fixed writing of rules (matching of fields)
+ Fixed matching of wildcard characters (Like to) on rules
+ Fixed matching of parent process on rules
+ Fixed showing of main window on multi-monitors
+ Fixed showing of "Hide Main Window" on Tray Icon
+ Added option "Do not auto-close notification dialog" (when a process is blocked)
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
There were some issues on rules, please retry with this new build (should work fine now).
To use wildcards (? and * characters) just select "Like to" instead of "Equal to".
Wildcard works on all process fields (name, path, signer, etc).
I'll start creating a pre-built-whitelist of safe commands related to Vulnerable Processes asap.
@NoVirusThanks
would be very nice if you add a password protection... there are cases when people have access to my computer or i could configure and install this on other pc's in lockdown mode and all of this would be pointless without password protection
would be very nice if you add a password protection... there are cases when people have access to my computer or i could configure and install this on other pc's in lockdown mode and all of this would be pointless without password protection
@Itachi Sempai
Yes it is on the todo list.
We'll also add "User must be in Administrators Group to edit things" (i.e to change protection mode or to open the GUI).
At the moment we're working on:
- Possibility to create a new rule or edit an existing rule via Events (right-click popup menu on an event)
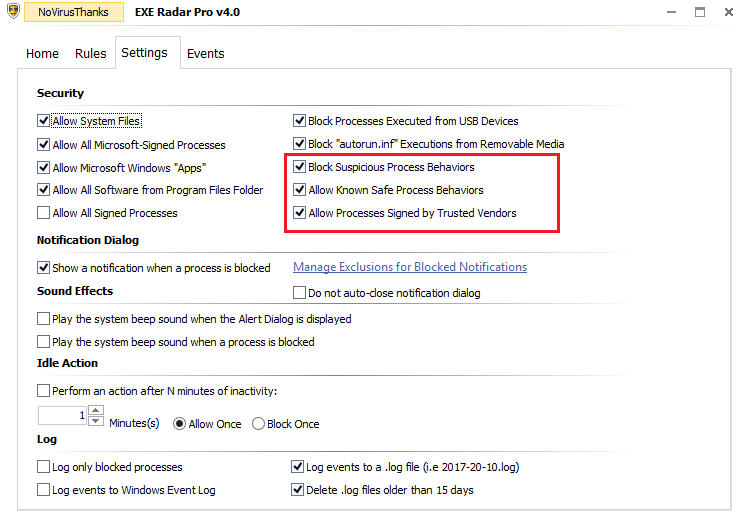
- New option "Alllow processes signed by Trusted Vendors" (internal list of Trusted Vendors)
- New option "Allow known safe processes behaviors" (some code taken from OSArmor internal whitelist + smart rules for safe command-lines)
- New option "Block suspicious processes behaviors" (some code taken from OSArmor) *To Discuss*
* With these last 3 "New option ..." the user should receive much less alerts *
- Option 1) discussed on #16 *Done*
- Option 2) discussed on #16
- Merging of Rule Editor with Expression Builder as discussed on #16
- Fix importing of rules that have command-line strings with double quotes
- Double-check creation of rules and matching of processes fields
- Bring the application to front when the GUI is shown via tray icon -> Show Main Window
- Increase rules pagination to 50 rules per page
Yes it is on the todo list.
We'll also add "User must be in Administrators Group to edit things" (i.e to change protection mode or to open the GUI).
At the moment we're working on:
- Possibility to create a new rule or edit an existing rule via Events (right-click popup menu on an event)
- New option "Alllow processes signed by Trusted Vendors" (internal list of Trusted Vendors)
- New option "Allow known safe processes behaviors" (some code taken from OSArmor internal whitelist + smart rules for safe command-lines)
- New option "Block suspicious processes behaviors" (some code taken from OSArmor) *To Discuss*
* With these last 3 "New option ..." the user should receive much less alerts *
- Option 1) discussed on #16 *Done*
- Option 2) discussed on #16
- Merging of Rule Editor with Expression Builder as discussed on #16
- Fix importing of rules that have command-line strings with double quotes
- Double-check creation of rules and matching of processes fields
- Bring the application to front when the GUI is shown via tray icon -> Show Main Window
- Increase rules pagination to 50 rules per page
Here is a new v4.0 (pre-release) test3:
http://downloads.novirusthanks.org/files/exe_radar_pro_4_setup_test3.exe
*** Please do not share the download link, we will delete it when we'll release the official v4 ***
So far this is what's new compared to the previous pre-release:
+ In Expression Builder "Read Data from File" on Parent doesn't parse the full file path
+ There are two undeletable categories named Learning Mode and Vulnerable Processes
+ When on Learning Mode, all automatically added rules should be added on rule category "Learning Mode"
+ Possibility to create\edit a rule from Events
+ Added button "Custom Rule" on Alert Dialog to easily create a custom rule
+ Stats are now live on the Main tabsheet (running time, # analyzed, # blocked, # allowed etc.)
+ Event log file is now created with file extension ".date.log"
+ Settings category fields are now bolded (security, notification dialog, sound effects etc.)
+ Any allowed event is now green in the Events tab
+ "View Logs" now opens the logs folder instead of selecting it only from the "EXE Radar Pro" parent folder
+ Uncluttered Settings checkbox controls so they're aligned better in the UI and uniform
+ Exclude Process dialog now has the "Delete" button disabled when an excluded process is NOT selected
+ Added 3 new checkboxes to Settings: Allow Known Safe Process Behaviors, Allow Trusted Vendors, Block Suspicious Process Behaviors
+ The option "Allow Known Safe Process Behaviors" incorporates the safe command-line strings in a safer way compared to ERPv3
+ Fixed file permission issue on .db and .log files
+ When adding a rule that is already present, close the Rule Editor window when Save button is clicked
+ On Settings tab renamed the "Manage Excluded Processes" to "Manage Exclusions for Blocked Notifications"
+ Deleting a rule understands the DELETE key and editing a rule understand the ENTER/RETURN key
+ When you double-click an event on Events tab it shows the event details
+ Added popup menu on Rules listview to edit\delete selected rule(s)
+ Added popup menu on Events listview to show process properties, open containing folder, lookup SHA1 on VirusTotal, etc
+ Show in the Events listview also integrity level, username/domain and system file (true\false)
+ Fixed vertical scrollbar from not working on events
+ Fixed exporting and importing of rules
+ Minor fixes and optimizations
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
Some screenshots:
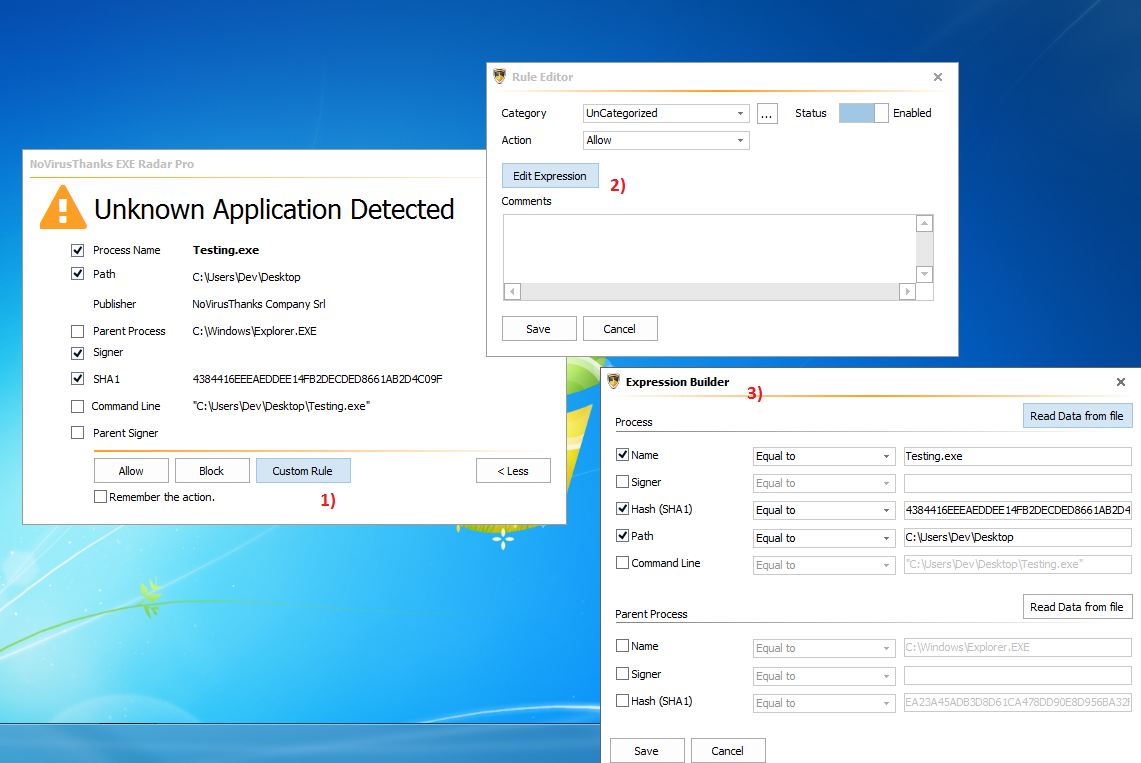
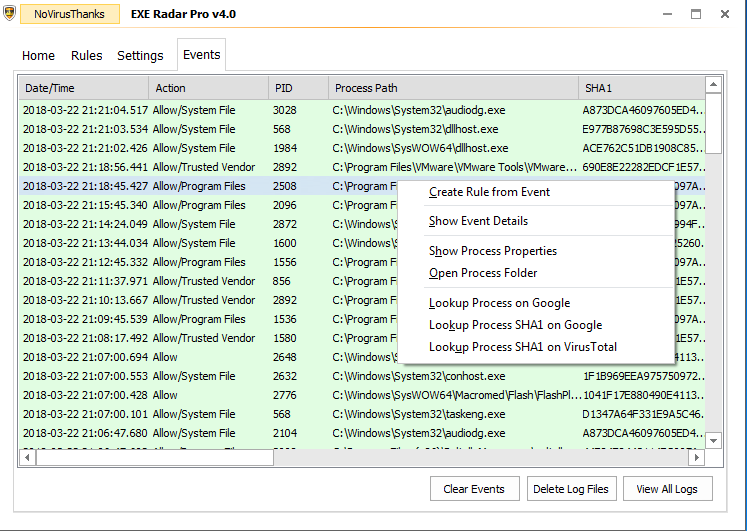
Let me know what you think about the changes.
The option "Block Suspicious Process Behaviors" includes some OSA rules.
Now we'll think about a better order for checking deny\allow\ask rules and about making a new tab dedicated to vulnerable processes maybe.
Personally I would also remove the Less\More button on Alert dialog and show directly all process details.
http://downloads.novirusthanks.org/files/exe_radar_pro_4_setup_test3.exe
*** Please do not share the download link, we will delete it when we'll release the official v4 ***
So far this is what's new compared to the previous pre-release:
+ In Expression Builder "Read Data from File" on Parent doesn't parse the full file path
+ There are two undeletable categories named Learning Mode and Vulnerable Processes
+ When on Learning Mode, all automatically added rules should be added on rule category "Learning Mode"
+ Possibility to create\edit a rule from Events
+ Added button "Custom Rule" on Alert Dialog to easily create a custom rule
+ Stats are now live on the Main tabsheet (running time, # analyzed, # blocked, # allowed etc.)
+ Event log file is now created with file extension ".date.log"
+ Settings category fields are now bolded (security, notification dialog, sound effects etc.)
+ Any allowed event is now green in the Events tab
+ "View Logs" now opens the logs folder instead of selecting it only from the "EXE Radar Pro" parent folder
+ Uncluttered Settings checkbox controls so they're aligned better in the UI and uniform
+ Exclude Process dialog now has the "Delete" button disabled when an excluded process is NOT selected
+ Added 3 new checkboxes to Settings: Allow Known Safe Process Behaviors, Allow Trusted Vendors, Block Suspicious Process Behaviors
+ The option "Allow Known Safe Process Behaviors" incorporates the safe command-line strings in a safer way compared to ERPv3
+ Fixed file permission issue on .db and .log files
+ When adding a rule that is already present, close the Rule Editor window when Save button is clicked
+ On Settings tab renamed the "Manage Excluded Processes" to "Manage Exclusions for Blocked Notifications"
+ Deleting a rule understands the DELETE key and editing a rule understand the ENTER/RETURN key
+ When you double-click an event on Events tab it shows the event details
+ Added popup menu on Rules listview to edit\delete selected rule(s)
+ Added popup menu on Events listview to show process properties, open containing folder, lookup SHA1 on VirusTotal, etc
+ Show in the Events listview also integrity level, username/domain and system file (true\false)
+ Fixed vertical scrollbar from not working on events
+ Fixed exporting and importing of rules
+ Minor fixes and optimizations
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
Some screenshots:
Let me know what you think about the changes.
The option "Block Suspicious Process Behaviors" includes some OSA rules.
Now we'll think about a better order for checking deny\allow\ask rules and about making a new tab dedicated to vulnerable processes maybe.
Personally I would also remove the Less\More button on Alert dialog and show directly all process details.
You may also like...
-
Expired Ashampoo Duplicate File Finder lifetime for free
- Started by Brownie2019
- Replies: 1
-
-
App Review Testing Orion Malware Cleaner Designed by Me
- Started by Trident
- Replies: 8
-
App Review DrWeb Security Space BETA
- Started by Shadowra
- Replies: 11
-
Serious Discussion Orion Malware Cleaner (OMC) - By Trident
- Started by Trident
- Replies: 23