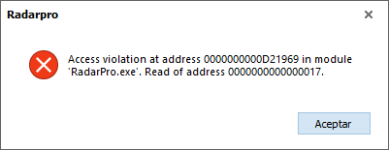
So far no issues on v4.0 (pre-release) test8. 
EXE Radar Pro v4 (Beta)
- Thread starter NoVirusThanks
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Pls, a sperate tab for trusted Trusted Digital Signatures(i can do it by myself but it's not user-friendly)
Last edited:
Let's say the Chrome.Exe want to reach the cmd(or other vulnerable processes).you can exclude the chrome.exe so the ERP will not ask you when chrome want to ##### with cmd(Erp auto allow that operation) you can exclude all commands or only a single command like ping x.x.x.x(as an example for cmd).exclude"
Let's say the Chrome.Exe want to reach the cmd(or other vulnerable processes).you can exclude the chrome.exe so the ERP will not ask you when chrome want to *** with cmd(Erp auto allow that operation) you can exclude all commands or only a single command like ping x.x.x.x(as an example for cmd).
I was attempting to create an allow rule for a cmd process launched via Chrome but i could not get it to work but have now successfully allowed it via an "exclude" rule
- thanks Sunshine-boy
You have to press the save button.
I have and i have an exclusion rule added :
Date/Time: 2018-04-14 08:57:03.275 Action: Allow/Excluded PID: 11080 Process Path: C:\Windows\System32\cmd.exe SHA1: 3585B37200EF3321262B0977401183694A3C15C6 Signer: Command Line: C:\WINDOWS\system32\cmd.exe /d /c "C:\Program Files (x86)\Siber Systems\AI RoboForm\Chrome\rf-chrome-nm-host.exe" chrome-extension://pnlccmojcmeohlpggmfnbbiapkmbliob/ --parent-window=0 < \\.\pipe\chrome.nativeMessaging.in.2da33a45ef3d0373 > \\.\pipe\chrome.nativeMessaging.out.2da33a45ef3d0373 Parent: C:\Program Files (x86)\Google\Chrome\Application\chrome.exe Parent SHA1: E5F54A2F3A004AF4C3CD24883B4F1CE38EE583D8 Parent Signer: Google Inc Expression: [Proc.Name = cmd.exe] [Proc.Path = C:\Windows\System32] [Proc.Hash LIKE 3585B37200EF3321262B0977401183694A3C15C6] [Proc.CmdLine LIKE C:\WINDOWS\system32\cmd.exe /d /c "C:\Program Files (x86)\Siber Systems\AI RoboForm\Chrome\rf-chrome-nm-host.exe" chrome-extension://pnlccmojcmeohlpggmfnbbiapkmbliob/ --parent-window=0 < \\.\pipe\chrome.nativeMessaging.in.*] [Action = Exclude] Category: Exluded(allowed) User/Domain: ANONYMOUS LOGON/NT AUTHORITY Integrity Level: Untrusted System File: True
Here is a new v4.0 (pre-release) test9:
http://downloads.novirusthanks.org/files/exe_radar_pro_4_setup_test9.exe
*** Please do not share the download link, we will delete it when we'll release the official v4 ***
So far this is what's new compared to the previous pre-release:
+ Added possibility to add/edit/delete/disable/enable Trusted Vendors List
+ Play Beep Sound (for Alert and Blocked Notify dialogs) are renamed to "Play a custom sound ..." and will play the loon WAV sound
+ Auto-check the field "Command-Line" in the Alert Dialog if category is "Vulnerable Processes"
+ If in the Alert Dialog the category is "Vulnerable Processes", when we click button "Allow" and the checkbox "Remember this action" is checked, the Action of the rule should be "Exclude" (not "Allow")
+ Save/load column size of Rules/Events listviews
+ Save/load window size of main window
+ Make the "Expression Builder" window re-sizable to enable more of the field values to be visible
+ Fixed the "Edit rule from event" feature does not appear to always work
+ Restored pagination (50 items per page)
+ Do not show "Category:" on Alert Dialog if the category is not applicable
+ Improved "Allow Known Safe Process Behaviors"
+ Minor fixes and optimizations
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
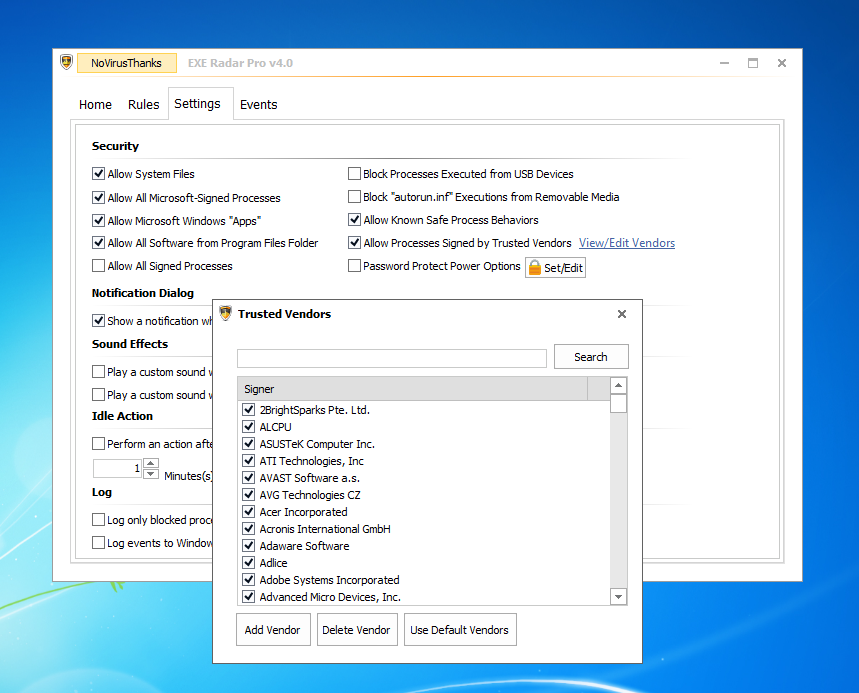
Screenshot of the View/Edit Vendors:
http://downloads.novirusthanks.org/files/exe_radar_pro_4_setup_test9.exe
*** Please do not share the download link, we will delete it when we'll release the official v4 ***
So far this is what's new compared to the previous pre-release:
+ Added possibility to add/edit/delete/disable/enable Trusted Vendors List
+ Play Beep Sound (for Alert and Blocked Notify dialogs) are renamed to "Play a custom sound ..." and will play the loon WAV sound
+ Auto-check the field "Command-Line" in the Alert Dialog if category is "Vulnerable Processes"
+ If in the Alert Dialog the category is "Vulnerable Processes", when we click button "Allow" and the checkbox "Remember this action" is checked, the Action of the rule should be "Exclude" (not "Allow")
+ Save/load column size of Rules/Events listviews
+ Save/load window size of main window
+ Make the "Expression Builder" window re-sizable to enable more of the field values to be visible
+ Fixed the "Edit rule from event" feature does not appear to always work
+ Restored pagination (50 items per page)
+ Do not show "Category:" on Alert Dialog if the category is not applicable
+ Improved "Allow Known Safe Process Behaviors"
+ Minor fixes and optimizations
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
Screenshot of the View/Edit Vendors:
Lookup on Virustotal should be done in my opinion using SHA256, as the simple SHA1 lookup not give results, resulting in this guy:

Example for Chromium:
Not sure if is in program to switch in some future builds all to SHA256, I suspect Virustotal deprecate now SHA1 in favour of SHA256.
What do you think about this @NoVirusThanks?

Example for Chromium:
Not sure if is in program to switch in some future builds all to SHA256, I suspect Virustotal deprecate now SHA1 in favour of SHA256.
What do you think about this @NoVirusThanks?
Last edited:
tried latest test build in a VM, I very much like the the way the UI and alerts work, the rule making and everything.
one small request, when something gets blocked, can we have a "Check on Virustotal" hyperlink/button on the Alert window?
since it won't show up in the overall history till the Alert window goes away, we can't check VT results before blocking or allowing it.
it would help with the decision making.
one small request, when something gets blocked, can we have a "Check on Virustotal" hyperlink/button on the Alert window?
since it won't show up in the overall history till the Alert window goes away, we can't check VT results before blocking or allowing it.
it would help with the decision making.
Last edited:
D
Deleted member 178
They are same, around 40-45mb RAM each, 0.5% CPU and I/O read & write bytes are minimal.Hi which one of these is easier on resources (ram ,cpu disk) Armor or Radar ?
Last edited by a moderator:
Does anything appear in the events tab? Is the ERPSvc service started?i have had it running a couple of hours and a few reboots later and its saying its scanned nothing! what am i doing wrong?
Nothing appears in the events tab and its running in the background.Does anything appear in the events tab? Is the ERPSvc service started?
I'll reinstall it and see if that helps.
Ok got it running by uninstalling it and reinstalling it, Now its working like a dream.
Last edited:
http://downloads.novirusthanks.org/files/VulnerableProcesses.xmlAre there any pre-configured settings in an XML file that I can use? Thank's yet again NVT great software.
covers most vulnerable processes
You may also like...
-
Expired Ashampoo Duplicate File Finder lifetime for free
- Started by Brownie2019
- Replies: 1
-
-
App Review Testing Orion Malware Cleaner Designed by Me
- Started by Trident
- Replies: 8
-
App Review DrWeb Security Space BETA
- Started by Shadowra
- Replies: 11
-
Serious Discussion Orion Malware Cleaner (OMC) - By Trident
- Started by Trident
- Replies: 23