Fake AVG virus
- Thread starter donnamv
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hi and welcome to MalwareTips! 
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
<hr>
Open OTL. Under custom scan/fixes, copy and paste the following:
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Download TDSSkiller from here
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Open OTL. Under custom scan/fixes, copy and paste the following:
:OTL
O4 - HKCU..\Run: [DN_PA_VGT] C:\Program Files\Adware Pro\Adware_Pro.exe File not found
O4 - HKCU..\Run: [SearchProtect] C:\Documents and Settings\pvidulic\Application Data\SearchProtect\bin\cltmng.exe (Conduit)
@Alternate Data Stream - 146 bytes -> C:\Documents and Settings\All Users\Application Data\TEMP346F792
:Files
C:\Program Files\Adware Pro
C:\Documents and Settings\pvidulic\Application Data\SearchProtect
ipconfig /flushdns /c
:Commands
[EMPTYTEMP]
[RESETHOSTS]
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.
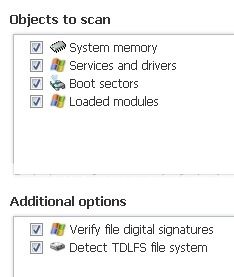
- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
I have attached the fix log OTL created.
Fiery said:Hi and welcome to MalwareTips!
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Open OTL. Under custom scan/fixes, copy and paste the following:
:OTL
O4 - HKCU..\Run: [DN_PA_VGT] C:\Program Files\Adware Pro\Adware_Pro.exe File not found
O4 - HKCU..\Run: [SearchProtect] C:\Documents and Settings\pvidulic\Application Data\SearchProtect\bin\cltmng.exe (Conduit)
@Alternate Data Stream - 146 bytes -> C:\Documents and Settings\All Users\Application Data\TEMP346F792
:Files
C:\Program Files\Adware Pro
C:\Documents and Settings\pvidulic\Application Data\SearchProtect
ipconfig /flushdns /c
:Commands
[EMPTYTEMP]
[RESETHOSTS]
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.

- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
Attachments
Did the TDSSkiller , ran the scan, it rebooted and now the screen say Running startup scripts for the last half hour!
Fiery said:Hi and welcome to MalwareTips!
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Open OTL. Under custom scan/fixes, copy and paste the following:
:OTL
O4 - HKCU..\Run: [DN_PA_VGT] C:\Program Files\Adware Pro\Adware_Pro.exe File not found
O4 - HKCU..\Run: [SearchProtect] C:\Documents and Settings\pvidulic\Application Data\SearchProtect\bin\cltmng.exe (Conduit)
@Alternate Data Stream - 146 bytes -> C:\Documents and Settings\All Users\Application Data\TEMP346F792
:Files
C:\Program Files\Adware Pro
C:\Documents and Settings\pvidulic\Application Data\SearchProtect
ipconfig /flushdns /c
:Commands
[EMPTYTEMP]
[RESETHOSTS]
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.

- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
I am technically challenged. What do you mean normal mode? The laptop restarted and it still says Running startup scripts. There is no TDSSKiller message.....
Fiery said:Are you able to access normal mode? can you do anything while that TDSSKiller message is up?
The laptop does not fully startup. It's still on the Running startup scripts screen. I can see the desktop...that TSSKiller did something to it.
Fiery said:Can you navigate to C:\ folder and see if there is a TDSSKiller log?
Also, give Malwarebytes a run
Try starting your PC in safemode
Start your computer in Safe Mode with Networking.
<br>
<img title="Safe Mode with Networking screen" src="http://malwaretips.com/images/removalguide/safemode.jpg" alt="[Image: Safemode.jpg]" width="539" height="292" border="0" /></li>
</ol>
Start your computer in Safe Mode with Networking.
- Remove all floppy disks, CDs, and DVDs from your computer, and then <>restart your computer</>.</li>
[*]<>Tap the "F8 key" continuously</> until you get the Advanced Boot Options screen.</li>
[*]On the Advanced Boot Options screen, use the arrow keys to <>highlight Safe Mode with Networking</> , and then <>press ENTER</>.
<br>
<img title="Safe Mode with Networking screen" src="http://malwaretips.com/images/removalguide/safemode.jpg" alt="[Image: Safemode.jpg]" width="539" height="292" border="0" /></li>
</ol>
Last edited by a moderator:
Click Yes.
Then try to find the TDSSKiller log in the C:\ folder and attach it here. While in safe mode, do another OTL scan after using adwCleaner and RogueKiller.
Please download AdwCleaner by Xplode onto your desktop.
Download & SAVE to your Desktop RogueKiller or from here
Then try to find the TDSSKiller log in the C:\ folder and attach it here. While in safe mode, do another OTL scan after using adwCleaner and RogueKiller.
Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
- Please post the content of that logfile with your next reply.
- You can find the logfile at C:\AdwCleaner[S1].txt
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Fiery said:Click Yes.
Then try to find the TDSSKiller log in the C:\ folder and attach it here. While in safe mode, do another OTL scan after using adwCleaner and RogueKiller.
Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
- Please post the content of that logfile with your next reply.
- You can find the logfile at C:\AdwCleaner[S1].txt
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Attachments
donnamv said:Fiery said:Click Yes.
Then try to find the TDSSKiller log in the C:\ folder and attach it here. While in safe mode, do another OTL scan after using adwCleaner and RogueKiller.
Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
- Please post the content of that logfile with your next reply.
- You can find the logfile at C:\AdwCleaner[S1].txt
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Attachments
RogueKiller V8.5.4 [Mar 18 2013] by Tigzy
mail : tigzyRK<at>gmail<dot>com
Feedback : http://www.geekstogo.com/forum/files/file/413-roguekiller/
Website : http://tigzy.geekstogo.com/roguekiller.php
Blog : http://tigzyrk.blogspot.com/
Operating System : Windows XP (5.1.2600 Service Pack 3) 32 bits version
Started in : Safe mode with network support
User : pvidulic [Admin rights]
Mode : Remove -- Date : 05/27/2013 11:12:19
| ARK || FAK || MBR |
¤¤¤ Bad processes : 0 ¤¤¤
¤¤¤ Registry Entries : 8 ¤¤¤
[RUN][SUSP PATH] HKUS\.DEFAULT[...]\Run : SearchProtect (C:\WINDOWS\system32\config\systemprofile\Application Data\SearchProtect\bin\cltmng.exe) -> DELETED
[STARTUP][SUSP PATH] HP SimpleSave Monitor.lnk @pvidulic : C:\Documents and Settings\pvidulic\Application Data\HP SimpleSave Application\StartHelper.exe [7] -> DELETED
[PROXY IE] HKCU\[...]\Internet Settings : ProxyServer (10.7.192.2:8080) -> NOT REMOVED, USE PROXYFIX
[HJ] HKLM\[...]\System : consentpromptbehavioradmin (0) -> REPLACED (2)
[HJ] HKLM\[...]\SystemRestore : DisableSR (1) -> REPLACED (0)
[HJ] HKLM\[...]\System : enablelua (0) -> REPLACED (1)
[HJ] HKLM\[...]\Security Center : FirewallDisableNotify (1) -> REPLACED (0)
[HJ DESK] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver : [NOT LOADED] ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
--> C:\WINDOWS\system32\drivers\etc\hosts
ÿþ1
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: HTS541080G9SA00 +++++
--- User ---
[MBR] e3f83c72ff09a4512f8c37e620825edf
[BSP] f4f37b2ef736532be808bea337d4827d : MBR Code unknown
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 63 | Size: 76316 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[2]_D_05272013_02d1112.txt >>
RKreport[1]_S_05272013_02d1111.txt ; RKreport[2]_D_05272013_02d1112.txt
mail : tigzyRK<at>gmail<dot>com
Feedback : http://www.geekstogo.com/forum/files/file/413-roguekiller/
Website : http://tigzy.geekstogo.com/roguekiller.php
Blog : http://tigzyrk.blogspot.com/
Operating System : Windows XP (5.1.2600 Service Pack 3) 32 bits version
Started in : Safe mode with network support
User : pvidulic [Admin rights]
Mode : Remove -- Date : 05/27/2013 11:12:19
| ARK || FAK || MBR |
¤¤¤ Bad processes : 0 ¤¤¤
¤¤¤ Registry Entries : 8 ¤¤¤
[RUN][SUSP PATH] HKUS\.DEFAULT[...]\Run : SearchProtect (C:\WINDOWS\system32\config\systemprofile\Application Data\SearchProtect\bin\cltmng.exe) -> DELETED
[STARTUP][SUSP PATH] HP SimpleSave Monitor.lnk @pvidulic : C:\Documents and Settings\pvidulic\Application Data\HP SimpleSave Application\StartHelper.exe [7] -> DELETED
[PROXY IE] HKCU\[...]\Internet Settings : ProxyServer (10.7.192.2:8080) -> NOT REMOVED, USE PROXYFIX
[HJ] HKLM\[...]\System : consentpromptbehavioradmin (0) -> REPLACED (2)
[HJ] HKLM\[...]\SystemRestore : DisableSR (1) -> REPLACED (0)
[HJ] HKLM\[...]\System : enablelua (0) -> REPLACED (1)
[HJ] HKLM\[...]\Security Center : FirewallDisableNotify (1) -> REPLACED (0)
[HJ DESK] HKLM\[...]\NewStartPanel : {20D04FE0-3AEA-1069-A2D8-08002B30309D} (1) -> REPLACED (0)
¤¤¤ Particular Files / Folders: ¤¤¤
¤¤¤ Driver : [NOT LOADED] ¤¤¤
¤¤¤ HOSTS File: ¤¤¤
--> C:\WINDOWS\system32\drivers\etc\hosts
ÿþ1
¤¤¤ MBR Check: ¤¤¤
+++++ PhysicalDrive0: HTS541080G9SA00 +++++
--- User ---
[MBR] e3f83c72ff09a4512f8c37e620825edf
[BSP] f4f37b2ef736532be808bea337d4827d : MBR Code unknown
Partition table:
0 - [ACTIVE] NTFS (0x07) [VISIBLE] Offset (sectors): 63 | Size: 76316 Mo
User = LL1 ... OK!
User = LL2 ... OK!
Finished : << RKreport[2]_D_05272013_02d1112.txt >>
RKreport[1]_S_05272013_02d1111.txt ; RKreport[2]_D_05272013_02d1112.txt
Fiery said:Is there another TDSSKiller log? There should be 2.
And let me know the results of the OTL scan afterwards.
Attachments
donnamv said:Fiery said:Is there another TDSSKiller log? There should be 2.
And let me know the results of the OTL scan afterwards.
Attachments
Yes it booted normally this time. Thanks.
Fiery said:Can you boot your PC normally now? Or does it still say "running TDSSKiller script"?
Good! We are almost done. How is your PC? Any other issues?
Run Eset NOD32 Online AntiVirus here
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
Run Eset NOD32 Online AntiVirus here
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
- Tick the box next to YES, I accept the Terms of Use.
- Click Start
- When asked, allow the activex control to install
- Disable your current antivirus software. You can usually do this with its Notfication Tray icon near the clock.
- Make sure that the option "Remove found threats" is Un-checked, and the following Advance Settings are Checked
- Scan unwanted applications
- Scan for potentially unsafe applications
- Enable Anti-Stealth Technology
- Click Scan
- Wait for the scan to finish
- When the scan is done, if it shows a screen that says "Threats found!", then click "List of found threats", and then click "Export to text file..."
- Save that text file on your desktop. Copy and paste the contents of that log in your next reply to this topic.
- The log can also be found in logfile located at C:\Program Files\ESET\Eset Online Scanner\log.txt
You may also like...
-
-
Security News New Fake CAPTCHA Scam Abuses Microsoft Tools to Install Amatera Stealer
- Started by Brownie2019
- Replies: 24
-
App Review AVG vs Symantec Antivirus: This One Cleaned Better
- Started by Khushal
- Replies: 57
-
Malware News Fake Leonardo DiCaprio Movie Torrent Drops Agent Tesla Through Layered PowerShell Chain
- Started by Khushal
- Replies: 2
-
New Tech Support Scam Uses Microsoft Logo to Fake Browser Lock, Steal Data
- Started by Brownie2019
- Replies: 1