You were quicker than me to share this, @amico81Zukunft der Cybersicherheit
Today was a press conference at 11 a.m. about the new deep-ray-technology
"G DATA's security solutions are equipped with a variety of next-generation technologies. With DeepRay, 30 years of competent experience in the antivirus business are now pooling into a new technology. The self-learning system exasculates a harmful process in the first step, based on more than 150 different factors. A "Multi perceptron powered neural network ", a novel artificial intelligence, eventually conducts a risk assessment. If a critical value is reached, the process is subjected to an in-depth analysis in the second step. In the future, this technology will save valuable computer resources and prevent malicious processes from executing them."
G DATA Beta-Test 25.5.1.14
- Thread starter amico81
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I've tried G-Data twice just for fun my problem was the Firewall blocking my Marantz (others) Streamer. Despite much faffing I never got it to work consistently, I would have thought I should have succeeded as Media Player Streaming is an integral part of Windows Networking (although makes sense really  )
)
Last edited:
About the new G Data security module:
Anti-virus software with AI technology: G Data relies on DeepRay
With DeepRay, the German AV manufacturer wants to make life much harder for cyber criminals.
By Jürgen Schmidt
read aloudPrintRead comments17posts
(Image: G Data)
The defense of malicious software is a constant hare-hedgehog race. With DeepRay, G Data wants to take on the role of the hedgehog, who is always there when the bunny arrives. To do this, the virus monitor analyzes files using AI methods, which primarily aim to detect known but disguised malware.

The system is taught continuously. The recognition includes factors such as the ratio of file size to actual code.
(Image: G Data)
G Data announces this with: "artificial intelligence brings breakthrough in the fight against cybercrime" - and triggers with the key words "breakthrough", "AI" and "cybercrime" in a sentence once the laboriously trained spam detection of some real intelligence. But behind DeepRay is a very valid approach. It is based on the realization that the criminals by no means constantly rewrite their malicious software. Instead, the proven code with the core functions is only repackaged over and over again to pass it past the AV software.
AI detection with neural networks
Thus, the file examined by the AV software only contains the malicious code in encrypted form. It will be found later in decrypted form in the main memory. But the Guardian can not constantly monitor for resource reasons. The mission of DeepRay is to reliably detect the suspicious unpacking of code using methods from AI research. The central element is a continuously trained neural network. If this detection fails, an analysis of the memory, which searches there for known patterns of malicious software. If malicious code is detected, the virus monitor stops the process.
Incidentally, the virus monitor not only examines the memory of the currently suspected process, but also all the processes that it has accessed to reserve memory. Behind this is the realization that malware often injects its malicious code into other seemingly harmless processes of the system.
This protection function is to be distributed immediately as an update to G-Data customers. It will complement conventional techniques such as signatures and heuristics. Whether this will actually change the rules of the game as radically as G DATA asserts will only have to be demonstrated in tests and above all in the daily lives of users. But the concept sounds interesting.
Source: Antiviren-Software mit KI-Technik: G Data setzt auf DeepRay
Anti-virus software with AI technology: G Data relies on DeepRay
With DeepRay, the German AV manufacturer wants to make life much harder for cyber criminals.
By Jürgen Schmidt
read aloudPrintRead comments17posts

(Image: G Data)
The defense of malicious software is a constant hare-hedgehog race. With DeepRay, G Data wants to take on the role of the hedgehog, who is always there when the bunny arrives. To do this, the virus monitor analyzes files using AI methods, which primarily aim to detect known but disguised malware.

The system is taught continuously. The recognition includes factors such as the ratio of file size to actual code.
(Image: G Data)
G Data announces this with: "artificial intelligence brings breakthrough in the fight against cybercrime" - and triggers with the key words "breakthrough", "AI" and "cybercrime" in a sentence once the laboriously trained spam detection of some real intelligence. But behind DeepRay is a very valid approach. It is based on the realization that the criminals by no means constantly rewrite their malicious software. Instead, the proven code with the core functions is only repackaged over and over again to pass it past the AV software.
AI detection with neural networks
Thus, the file examined by the AV software only contains the malicious code in encrypted form. It will be found later in decrypted form in the main memory. But the Guardian can not constantly monitor for resource reasons. The mission of DeepRay is to reliably detect the suspicious unpacking of code using methods from AI research. The central element is a continuously trained neural network. If this detection fails, an analysis of the memory, which searches there for known patterns of malicious software. If malicious code is detected, the virus monitor stops the process.
Incidentally, the virus monitor not only examines the memory of the currently suspected process, but also all the processes that it has accessed to reserve memory. Behind this is the realization that malware often injects its malicious code into other seemingly harmless processes of the system.
This protection function is to be distributed immediately as an update to G-Data customers. It will complement conventional techniques such as signatures and heuristics. Whether this will actually change the rules of the game as radically as G DATA asserts will only have to be demonstrated in tests and above all in the daily lives of users. But the concept sounds interesting.
Source: Antiviren-Software mit KI-Technik: G Data setzt auf DeepRay
Last edited:
- Apr 28, 2015
- 9,398
- 1
- 84,824
- 8,389
@Faybert: it would be interesting is this info is also published in English, thanks 
E
Eddie Morra
It would be pretty good if there was an official translation for these articles on G Data in English, Italian or Russian, because reading them with Google translate can be tricky sometimes when GT ruins the sentence structure from making sense. GT does work, but it just makes things awkward when it messes up what was trying to actually be said badly.
If only I had the time to learn German... I'll add that on my to-do list. I doubt I will be able to do it within the next several years because I once took classes for 3+ years on German and forgot what "Ich" meant by the end of the day. Nice language, would be cool if I could read, write and speak in it fluently. Imagine all the more people you could then speak with... and all the information/resources out there which are strictly in German, or any other language.
It's incredible when you remember how learning one language can make the difference between communicating with MILLIONS more people around the world.
If only I had the time to learn German... I'll add that on my to-do list. I doubt I will be able to do it within the next several years because I once took classes for 3+ years on German and forgot what "Ich" meant by the end of the day. Nice language, would be cool if I could read, write and speak in it fluently. Imagine all the more people you could then speak with... and all the information/resources out there which are strictly in German, or any other language.
It's incredible when you remember how learning one language can make the difference between communicating with MILLIONS more people around the world.
Sorry, I think now it's better, @harlan4096 
[QUOTE = "Faybert, post: 777943, member: 58452"] o do this, the virus monitor acronyms files [/ QUOTE]
Deep ray constnatly monitors within the ram and after execution and traces down the culprit behaviors with/in its own updated AI model in a neural network across different trained levels before a verdict is reached.
Good work ! Eager to test
From what i understood ..Deep ray acts as a virtual platform after the malicious file is by passed by its pro active layers, since some times malicious operations hide before they begin. So making BB running entirely on memory is a waste thingAbout the new G Data security module:
Anti-virus software with AI technology: G Data relies on DeepRay
With DeepRay, the German AV manufacturer wants to make life much harder for cyber criminals.
By Jürgen Schmidt
read aloudPrintRead comments17posts

(Image: G Data)
The defense of malicious software is a constant hare-hedgehog race. With DeepRay, G Data wants to take on the role of the hedgehog, who is always there when the bunny arrives. To do this, the virus monitor analyzes files using AI methods, which primarily aim to detect known but disguised malware.
The system is taught continuously. The recognition includes factors such as the ratio of file size to actual code.
(Image: G Data)
G Data announces this with: "artificial intelligence brings breakthrough in the fight against cybercrime" - and triggers with the key words "breakthrough", "AI" and "cybercrime" in a sentence once the laboriously trained spam detection of some real intelligence. But behind DeepRay is a very valid approach. It is based on the realization that the criminals by no means constantly rewrite their malicious software. Instead, the proven code with the core functions is only repackaged over and over again to pass it past the AV software.
AI detection with neural networks
Thus, the file examined by the AV software only contains the malicious code in encrypted form. It will be found later in decrypted form in the main memory. But the Guardian can not constantly monitor for resource reasons. The mission of DeepRay is to reliably detect the suspicious unpacking of code using methods from AI research. The central element is a continuously trained neural network. If this detection fails, an analysis of the memory, which searches there for known patterns of malicious software. If malicious code is detected, the virus monitor stops the process.
Incidentally, the virus monitor not only examines the memory of the currently suspected process, but also all the processes that it has accessed to reserve memory. Behind this is the realization that malware often injects its malicious code into other seemingly harmless processes of the system.
This protection function is to be distributed immediately as an update to G-Data customers. It will complement conventional techniques such as signatures and heuristics. Whether this will actually change the rules of the game as radically as G DATA asserts will only have to be demonstrated in tests and above all in the daily lives of users. But the concept sounds interesting.
Source: Antiviren-Software mit KI-Technik: G Data setzt auf DeepRay
Deep ray constnatly monitors within the ram and after execution and traces down the culprit behaviors with/in its own updated AI model in a neural network across different trained levels before a verdict is reached.
Good work ! Eager to test
E
Eddie Morra
Based on that article, here's a TLDR of what is being said in a simpler form.From what i understood ..Deep ray acts as a virtual platform after the malicious file is by passed by its pro active layers, since some times malicious operations hide before they begin. So making BB running entirely on memory is a waste thing
Deep ray constnatly monitors within the ram and after execution and traces down the culprit behaviors with/in its own updated AI model in a neural network across different trained levels before a verdict is reached.
Good work ! Eager to test
1. DeepRay is relying on Ai/ML models (e.g. neural network).
2. DeepRay is being used by G Data to identify unpacking operations through memory scanning.
3. DeepRay monitors a few things (dynamically) to identify potentially malicious operations which would have normally evaded detection if memory scanning was relied on alone, such as code injection into other processes -> memory scanning on the injected code to determine if any of their generic signatures can find a match.
For the most part, it appears to be a mechanism to aid in malware detection through better identification of unpacking techniques which allows them to use their generic signatures to a fuller potential, with a hint of some dynamic interception to enhance it more.
Please do not quote me on this though, because G Data aren't straight-up cutting to the chase with these announcements/descriptions and neither are these blog posts, and... what I am reading might not even be a correct English translation.
But the thing i'm confused here this is the first time G data directly made the module in its Beta version without any beta tests / announcements..i did try to make it to work but may be i'm not successful.Based on that article, here's a TLDR of what is being said in a simpler form.
1. DeepRay is relying on Ai/ML models (e.g. neural network).
2. DeepRay is being used by G Data to identify unpacking operations through memory scanning.
3. DeepRay monitors a few things (dynamically) to identify potentially malicious operations which would have normally evaded detection if memory scanning was relied on alone, such as code injection into other processes -> memory scanning on the injected code to determine if any of their generic signatures can find a match.
For the most part, it appears to be a mechanism to aid in malware detection through better identification of unpacking techniques which allows them to use their generic signatures to a fuller potential, with a hint of some dynamic interception to enhance it more.
Please do not quote me on this though, because G Data aren't straight-up cutting to the chase with these announcements/descriptions and neither are these blog posts, and... what I am reading might not even be a correct English translation.
Yes what u said is correct..it seems to help in other modules along side its own work. But still confused about its way of mechanism
Testing is the own way to get a bit clarity. thanks for your detail.
What a pity not to see the new beta version with deepray in our malwarehub :emoji_disappointed:
What a pity not to see the new beta version with deepray in our malwarehub :emoji_disappointed:
That would be TERRIFIC!!!
Any takers???
Thank you for sharing with us all, @Faybert. The 25.5.1.21 version has already gone out to the general public?
I will continue my tests..but as far I studiedThat would be TERRIFIC!!!
Any takers???
Deep Ray is too deep seated ...so requires a lot of patience and time.Remember if a module doesn't work in our tests..doesn't mean it is obsolete..in one day or next it will come out..
I will share the video if and if I see Deep Ray in action.
Even me too eager#
Giving the Anti-Virus a spin, I've had no problems - Does the install size of the program have to be so large, hundreds of meg more than ESET for example? Tried the Internet Security & the firewall is most annoying, despite faffing for an hour it was still blocking streaming, going to get support on about this as I really like G Data.
5
509322
Tried the Internet Security & the firewall is most annoying, despite faffing for an hour it was still blocking streaming, going to get support on about this as I really like G Data.
Good luck with the firewall. It has been reported to G DATA many times.
Dual engine weight , Bit defender signatures(Heavy) + Engine B's, Rest of the other modules, Deep Ray (Recently added).Giving the Anti-Virus a spin, I've had no problems - Does the install size of the program have to be so large, hundreds of meg more than ESET for example? Tried the Internet Security & the firewall is most annoying, despite faffing for an hour it was still blocking streaming, going to get support on about this as I really like G Data.
just tried it out 25.5.1.14 is lighter and faster.
Absolutely. MUCH lighter and faster!
No problems here. Installed right over 25.0.****
DeepRay now officially unveiled by G Data:
DeepRay messes up cybercriminals
With machine learning against malware: G DATA has introduced its latest next-generation technology. DeepRay can effectively detect obfuscation of malware samples, protecting customers in real time from new threats.
 G DATA introduces DeepRay.
G DATA introduces DeepRay.
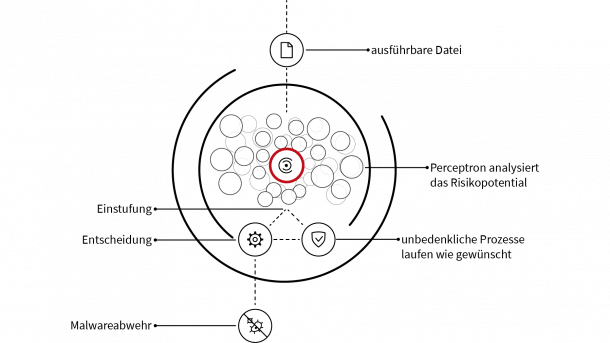
G DATA is tackling the growing threat posed by cybercrime with a complete new development. Instead of catching malware with classic signatures, the German IT security manufacturer relies on a self-developed machine learning solution to quickly identify, identify and block rapidly changing malware in a timely, effective and resource-efficient manner. The DeepRay technologyclassifies the possible damage files using artificial intelligence on the basis of several hundred factors and calculates a risk value for each individual executable file.
DeepRay has become necessary because the cybercrime scene has developed massively over the past few years: malicious software has become a service good. Criminals can buy specialized malicious software packages on relevant underground platforms and then distribute them. They need far less specialized knowledge than before. As a result, more and more criminals are taking advantage of these offerings, spreading more and more malware online. In addition, the malware itself is also technologically superior. Sophisticated camouflage mechanisms make detection by antivirus software difficult. Classic algorithms for finding such malware are thus severely limited in their effectiveness.
New iteration of Next-Gen technologies
The DeepRay technology complements the already extensive portfolio of next-generation technologies in the G DATA securitysolutions . The Exploit Protection can already prevent the exploitation of security vulnerabilities in the operating system and software, the G DATA BankGuard protects users in online banking. A complete overview of all Next-Gen components can be found in this blog post.
"With DeepRay, we're changing the rules of the game and taking their economic footing for cybercriminals. Thanks to this new technology we are behind the camouflage of the malicious software and can effectively fend off fast-paced malware campaigns. Thus, we significantly improve the protection for our customers, "explains Andreas Lüning, founder and CEO of G DATA Software AG.
DeepRay is based on the more than 30 years of experience that G DATA has in the antivirus business . The expertise in analyzing and classifying malware flows directly into the training of new machine learning components. G DATA uses neural networks with multiple perceptrons to quickly and efficiently classify executables.
All in all, around 20 differently-trained machine-learning models are doing their job in the G DATA security solution in order to ensure optimal detection of defective files using DeepRay. Executable files of various kinds (portable executables such as .exe / MSIL / .Net or VB6) are analyzed based on static indicators predefined by our analysts. The training set includes more than 150 such indicators, including the ratio of file size to executable code, the version of the compiler used, or the number of imported system functions.
20 machine-learning models in the service of customers
Using various training sets, the models analyze the processes and determine a risk value. If the file is considered potentially defective by one of the models, the machine learning technology will initiate a deeper analysis of the file. This analysis takes place in the memory of the customer. As a result, malware can not behave differently in an analytics environment to escape detection. The DeepRay technology therefore makes it possible to detect even previously unknown malware based on specific memory characteristics.
Nor does it use cybercriminals to obfuscate their malicious code with the help of certain packers or other concealment techniques. First of all, even the use of certain packers in combination with other features can reveal an executable file as malicious. And second, the code runs at least in the main memory of the computer in plain text and can be analyzed.
However, as new malware families or new threats emerge, another learning process remains essential. For this DeepRay uses adaptive learning. The knowledge gained from the technology will be much more stable and long-term usable than single signatures or heuristic detection methods.
The advantage of the technology is obvious: it not only detects malware samples previously considered by analysts to be harmful, but also previously unknown programs. In addition, it is no longer necessary to write a separate signature for each individual recognition. With a growing data set and a long-term learning process, DeepRay's insights can effectively protect users from malware in the long run.
Source: DeepRay versaut Cyberkriminellen das Geschäft | G DATA Blog
DeepRay messes up cybercriminals
With machine learning against malware: G DATA has introduced its latest next-generation technology. DeepRay can effectively detect obfuscation of malware samples, protecting customers in real time from new threats.

G DATA is tackling the growing threat posed by cybercrime with a complete new development. Instead of catching malware with classic signatures, the German IT security manufacturer relies on a self-developed machine learning solution to quickly identify, identify and block rapidly changing malware in a timely, effective and resource-efficient manner. The DeepRay technologyclassifies the possible damage files using artificial intelligence on the basis of several hundred factors and calculates a risk value for each individual executable file.
DeepRay has become necessary because the cybercrime scene has developed massively over the past few years: malicious software has become a service good. Criminals can buy specialized malicious software packages on relevant underground platforms and then distribute them. They need far less specialized knowledge than before. As a result, more and more criminals are taking advantage of these offerings, spreading more and more malware online. In addition, the malware itself is also technologically superior. Sophisticated camouflage mechanisms make detection by antivirus software difficult. Classic algorithms for finding such malware are thus severely limited in their effectiveness.
New iteration of Next-Gen technologies
The DeepRay technology complements the already extensive portfolio of next-generation technologies in the G DATA securitysolutions . The Exploit Protection can already prevent the exploitation of security vulnerabilities in the operating system and software, the G DATA BankGuard protects users in online banking. A complete overview of all Next-Gen components can be found in this blog post.
"With DeepRay, we're changing the rules of the game and taking their economic footing for cybercriminals. Thanks to this new technology we are behind the camouflage of the malicious software and can effectively fend off fast-paced malware campaigns. Thus, we significantly improve the protection for our customers, "explains Andreas Lüning, founder and CEO of G DATA Software AG.
DeepRay is based on the more than 30 years of experience that G DATA has in the antivirus business . The expertise in analyzing and classifying malware flows directly into the training of new machine learning components. G DATA uses neural networks with multiple perceptrons to quickly and efficiently classify executables.
All in all, around 20 differently-trained machine-learning models are doing their job in the G DATA security solution in order to ensure optimal detection of defective files using DeepRay. Executable files of various kinds (portable executables such as .exe / MSIL / .Net or VB6) are analyzed based on static indicators predefined by our analysts. The training set includes more than 150 such indicators, including the ratio of file size to executable code, the version of the compiler used, or the number of imported system functions.
20 machine-learning models in the service of customers
Using various training sets, the models analyze the processes and determine a risk value. If the file is considered potentially defective by one of the models, the machine learning technology will initiate a deeper analysis of the file. This analysis takes place in the memory of the customer. As a result, malware can not behave differently in an analytics environment to escape detection. The DeepRay technology therefore makes it possible to detect even previously unknown malware based on specific memory characteristics.
Nor does it use cybercriminals to obfuscate their malicious code with the help of certain packers or other concealment techniques. First of all, even the use of certain packers in combination with other features can reveal an executable file as malicious. And second, the code runs at least in the main memory of the computer in plain text and can be analyzed.
However, as new malware families or new threats emerge, another learning process remains essential. For this DeepRay uses adaptive learning. The knowledge gained from the technology will be much more stable and long-term usable than single signatures or heuristic detection methods.
The advantage of the technology is obvious: it not only detects malware samples previously considered by analysts to be harmful, but also previously unknown programs. In addition, it is no longer necessary to write a separate signature for each individual recognition. With a growing data set and a long-term learning process, DeepRay's insights can effectively protect users from malware in the long run.
Source: DeepRay versaut Cyberkriminellen das Geschäft | G DATA Blog
Last edited:
Nice job G-data, just need to remove "KingOfBug" EngineDeepRay now officially unveiled by G Data:
DeepRay messes up cybercriminals
With machine learning against malware: G DATA has introduced its latest next-generation technology. DeepRay can effectively detect obfuscation of malware samples, protecting customers in real time from new threats.
G DATA introduces DeepRay.
G DATA is tackling the growing threat posed by cybercrime with a complete new development. Instead of catching malware with classic signatures, the German IT security manufacturer relies on a self-developed machine learning solution to quickly identify, identify and block rapidly changing malware in a timely, effective and resource-efficient manner. The DeepRay technologyclassifies the possible damage files using artificial intelligence on the basis of several hundred factors and calculates a risk value for each individual executable file.
DeepRay has become necessary because the cybercrime scene has developed massively over the past few years: malicious software has become a service good. Criminals can buy specialized malicious software packages on relevant underground platforms and then distribute them. They need far less specialized knowledge than before. As a result, more and more criminals are taking advantage of these offerings, spreading more and more malware online. In addition, the malware itself is also technologically superior. Sophisticated camouflage mechanisms make detection by antivirus software difficult. Classic algorithms for finding such malware are thus severely limited in their effectiveness.
New iteration of Next-Gen technologies
The DeepRay technology complements the already extensive portfolio of next-generation technologies in the G DATA securitysolutions . The Exploit Protection can already prevent the exploitation of security vulnerabilities in the operating system and software, the G DATA BankGuard protects users in online banking. A complete overview of all Next-Gen components can be found in this blog post.
"With DeepRay, we're changing the rules of the game and taking their economic footing for cybercriminals. Thanks to this new technology we are behind the camouflage of the malicious software and can effectively fend off fast-paced malware campaigns. Thus, we significantly improve the protection for our customers, "explains Andreas Lüning, founder and CEO of G DATA Software AG.
DeepRay is based on the more than 30 years of experience that G DATA has in the antivirus business . The expertise in analyzing and classifying malware flows directly into the training of new machine learning components. G DATA uses neural networks with multiple perceptrons to quickly and efficiently classify executables.
All in all, around 20 differently-trained machine-learning models are doing their job in the G DATA security solution in order to ensure optimal detection of defective files using DeepRay. Executable files of various kinds (portable executables such as .exe / MSIL / .Net or VB6) are analyzed based on static indicators predefined by our analysts. The training set includes more than 150 such indicators, including the ratio of file size to executable code, the version of the compiler used, or the number of imported system functions.
20 machine-learning models in the service of customers
Using various training sets, the models analyze the processes and determine a risk value. If the file is considered potentially defective by one of the models, the machine learning technology will initiate a deeper analysis of the file. This analysis takes place in the memory of the customer. As a result, malware can not behave differently in an analytics environment to escape detection. The DeepRay technology therefore makes it possible to detect even previously unknown malware based on specific memory characteristics.
Nor does it use cybercriminals to obfuscate their malicious code with the help of certain packers or other concealment techniques. First of all, even the use of certain packers in combination with other features can reveal an executable file as malicious. And second, the code runs at least in the main memory of the computer in plain text and can be analyzed.
However, as new malware families or new threats emerge, another learning process remains essential. For this DeepRay uses adaptive learning. The knowledge gained from the technology will be much more stable and long-term usable than single signatures or heuristic detection methods.
The advantage of the technology is obvious: it not only detects malware samples previously considered by analysts to be harmful, but also previously unknown programs. In addition, it is no longer necessary to write a separate signature for each individual recognition. With a growing data set and a long-term learning process, DeepRay's insights can effectively protect users from malware in the long run.
Source: DeepRay versaut Cyberkriminellen das Geschäft | G DATA Blog
I agree, they should follow the F-Secure example .Nice job G-data, just need to remove "KingOfBug" Engine
You may also like...
-
On Sale! G DATA Total Security 2026, 3 Dev, 1 Yr, 19,90 €
- Started by Brownie2019
- Replies: 0
-
G DATA Internet Security 2025 -Multi Device-, 3 Dev, 1 yr, 14,90 €
- Started by Brownie2019
- Replies: 10
-
Serious Discussion Data Collection Core Principles (Security Software)
- Started by Trident
- Replies: 7
-
AV-Comparatives Data transmission in consumer security products
- Started by Gandalf_The_Grey
- Replies: 13
-
AVLab.pl Threat landscape and the results of protection based on telemetry data of malware in the wild (March 2023)
- Started by Adrian Ścibor
- Replies: 13