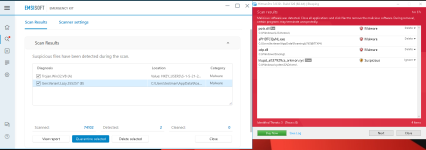
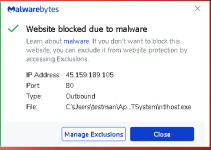
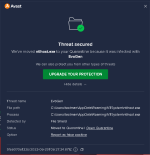
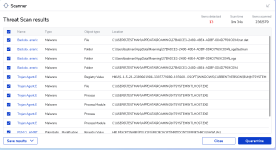
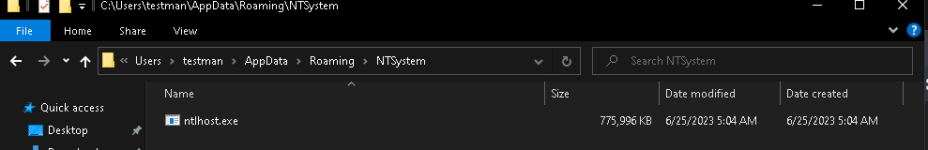
Majority of the content inside is just filler to increase the size and do it in a way that won’t raise suspicion by static abalysis, which suggests that AVs like Norton, Defender or Kaspersky were the target for evasion. The Cursed.exe is the actual stealer, which is configured with a very high refresh rate (amateur attacker maybe) and has very high CPU usage.Majority of the content inside is just filler to increase the size and do it in a way that won’t raise suspicion by static abalysis, which suggests that AVs like Norton, Defender or Kaspersky were the target for evasion. The Cursed.exe is the actual stealer, which is configured with a very high refresh rate (amateur attacker maybe) and has very high CPU usage.
@piquiteco BD uses cloud and everyone else does as well. There is nobody not using it.