- Feb 25, 2017
- 2,654
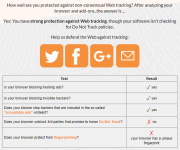
Hey guys, since some time I'm looking for ways to make my Browser fingerprint less unique as a testsite always tells me that it's still unique after all, no matter what I've tried so far. Do you have any tips? I'd also appreciate to see your testresults.
Website: Panopticlick
My current extensions are: Adguard, Privacy Badger, SmartHTTPS, Decentraleyes and Canvas Blocker. (Google Chrome)
looking forward to your recommendations
Website: Panopticlick
My current extensions are: Adguard, Privacy Badger, SmartHTTPS, Decentraleyes and Canvas Blocker. (Google Chrome)
looking forward to your recommendations