@Sunkar Thank you so much for clarifying. I truly appreciate it.
New Update JShelter - JavaScript Restrictor
- Thread starter SpiderWeb
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Add-on/Extension Page
- https://jshelter.org/
Yes, it is but smaller. There is an overlap only for fingerprinting prevention.
thanksYes, it is but smaller. There is an overlap only for fingerprinting prevention.
F
ForgottenSeer 92963
Request to JShelter developers: don't add nonsense, add noise!
Technical definition of noise: irregular fluctuations that accompany a transmitted electrical signal but are not part of it and tend to obscure it.
This morning I got another email notification from Github (Better to provide real world values than random or faked values for three spoofs WebGL, Plugins and Fonys · Issue #166 · polcak/jsrestrictor) telling me again that the WebGL vendor and renderer values are correctly randomized with non-existing fake values. They don't seem to grasp that they are adding identifying nonsense in stead of obscuring noise.
Trace for instances does this (half) right by adding a list of real world GPU models to obscure WebGL vendor and renderer. To do this perfectly right the end-user has to limit this list to DirectX and WebGL versions which the end-user's own GPU model does accept (as explained in red in the picture). So when you have a Intel 620 HD Graphics model, you should limit the list to generation 9 Intel GPU's all excepting DirectX 12_1 (the 5xx and 6xx family Intel graphics GPU's).
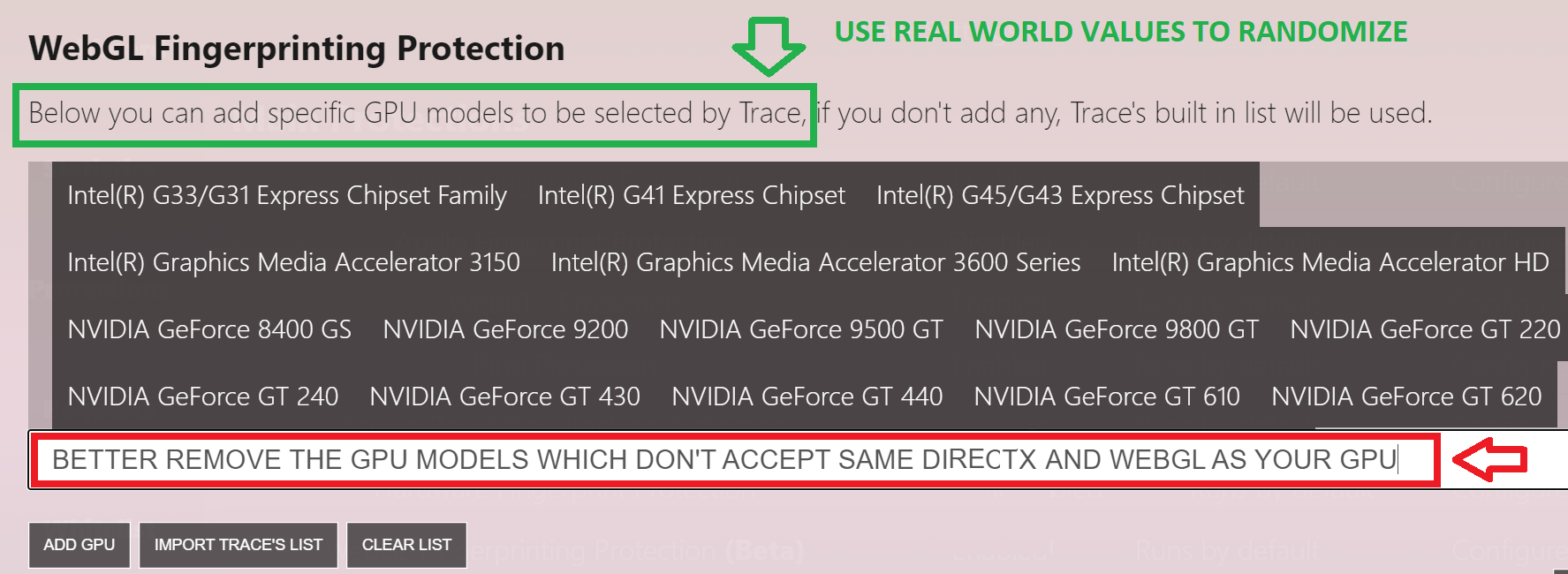
I only get responses (probably from tech people) that they are implementing what the BLOG tells them to (link). Sadly there seems to be no big-data expert and digital marketeer involved who can explain them what they are doing is putting a huge pink elephant (non-existing value) in a herd of sheep and thinking they won't stand out, so until further notice
DON'T USE THIS EXTENSION
*) This is yet another example of the much posted advice in security forums that it is better to add no fingerprinting protection than wrong obfuscation. Remember that only a limited percentage of the websites use these advanced fingerprinting techniques (5 to 10 at most is my guess) because the digital marketeers using these systems are often only trained in the top3 most prevalent tracking systems and have to proof (every two to three) years that they still know how to operate these analysis/tagging/tracking systems.
Technical definition of noise: irregular fluctuations that accompany a transmitted electrical signal but are not part of it and tend to obscure it.
This morning I got another email notification from Github (Better to provide real world values than random or faked values for three spoofs WebGL, Plugins and Fonys · Issue #166 · polcak/jsrestrictor) telling me again that the WebGL vendor and renderer values are correctly randomized with non-existing fake values. They don't seem to grasp that they are adding identifying nonsense in stead of obscuring noise.
Trace for instances does this (half) right by adding a list of real world GPU models to obscure WebGL vendor and renderer. To do this perfectly right the end-user has to limit this list to DirectX and WebGL versions which the end-user's own GPU model does accept (as explained in red in the picture). So when you have a Intel 620 HD Graphics model, you should limit the list to generation 9 Intel GPU's all excepting DirectX 12_1 (the 5xx and 6xx family Intel graphics GPU's).
I only get responses (probably from tech people) that they are implementing what the BLOG tells them to (link). Sadly there seems to be no big-data expert and digital marketeer involved who can explain them what they are doing is putting a huge pink elephant (non-existing value) in a herd of sheep and thinking they won't stand out, so until further notice
DON'T USE THIS EXTENSION
*) This is yet another example of the much posted advice in security forums that it is better to add no fingerprinting protection than wrong obfuscation. Remember that only a limited percentage of the websites use these advanced fingerprinting techniques (5 to 10 at most is my guess) because the digital marketeers using these systems are often only trained in the top3 most prevalent tracking systems and have to proof (every two to three) years that they still know how to operate these analysis/tagging/tracking systems.
Last edited by a moderator:
Request to JShelter developers: don't add nonsense, add noise!
Technical definition of noise: irregular fluctuations that accompany a transmitted electrical signal but are not part of it and tend to obscure it.
This morning I got another email notification from Github (Better to provide real world values than random or faked values for three spoofs WebGL, Plugins and Fonys · Issue #166 · polcak/jsrestrictor) telling me again that the WebGL vendor and renderer values are correctly randomized with non-existing fake values. They don't seem to grasp that they are adding identifying nonsense in stead of obscuring noise.
Trace for instances does this (half) right by adding a list of real world GPU models to obscure WebGL vendor and renderer. To do this perfectly right the end-user has to limit this list to DirectX and WebGL versions which the end-user's own GPU model does accept (as explained in red in the picture). So when you have a Intel 620 HD Graphics model, you should limit the list to generation 9 Intel GPU's all excepting DirectX 12_1 (the 5xx and 6xx family Intel graphics GPU's).
View attachment 263644
I only get responses (probably from tech people) that they are implementing what the BLOG tells them to (link). Sadly there seems to be no big-data expert and digital marketeer involved who can explain them what they are doing is putting a huge pink elephant (non-existing value) in a herd of sheep and thinking they won't stand out, so until further notice
DON'T USE THIS EXTENSION
*) This is yet another example of the much posted advice in security forums that it is better to add no fingerprinting protection than wrong obfuscation. Remember that only a limited percentage of the websites use these advanced fingerprinting techniques (5 to 10 at most is my guess) because the digital marketeers using these systems are often only trained in the top3 most prevalent tracking systems and have to proof (every two to three) years that they still know how to operate these analysis/tagging/tracking systems.
Discussion on WebGL, Plugins, Fonts, Timestamps, Geolocation and other wrappers · Issue #166 · polcak/jsrestrictor
When using JShelter on max The unmased vendor and renderer return random (invalid) values [see link at MT: https://malwaretips.com/attachments/1642245908077-png.263592/ Plugin has option to provide...
F
ForgottenSeer 92963
F
ForgottenSeer 92963
Last edited by a moderator:
Trace has this setting disabled by default. It is, however, available to be enabled in the free version.To do this perfectly right the end-user has to limit this list to DirectX and WebGL versions which the end-user's own GPU model does accept (as explained in red in the picture).
I wonder if there are other settings besides this one that will obscure the gpu more completely. I've done browser fingerprinting tests in the past and my hardware (cpu and gpu) were always correctly identified. Think if I have some time, I'll enable the spoofer also and see how it does--the thing is, it's not perfect so I don't have this active at the moment.
One browser test I've used--most know this one already. Should I delete the Microsoft Visual Redistributable C++ libraries (2015, 2017, 2019)?

F
ForgottenSeer 92963
@plat1098
You exactly pin pointed the weak spot. The browser reveals same or similar data through different means: (browser) Agent, Navigator (data), (which standards the browser) Accepts, API's
That is why the idea of Google is really elegant. In stead of blocking and blurring data, a website has some "user data" budget to provide a seamless user experience. When ithe website is over asking data (more than necessary) the browser will block access to these different data sources. Some browsers (Firefox, Brave and Safari) have put time and money in limiting user data access or separating data. So they are trying to change the standards to what they already have developed (or adopt it a little so they still have an advantage over other browsers).
To be honest, I am not using an anti-fingerprinting or blurring solution, because I yet have to find a good functioning extension or the solution chargex to much for what my privacy is worth (e.g. browser bubble) or is a to heavy hit on my internet speed (Tor browser plus VPN)
You exactly pin pointed the weak spot. The browser reveals same or similar data through different means: (browser) Agent, Navigator (data), (which standards the browser) Accepts, API's
That is why the idea of Google is really elegant. In stead of blocking and blurring data, a website has some "user data" budget to provide a seamless user experience. When ithe website is over asking data (more than necessary) the browser will block access to these different data sources. Some browsers (Firefox, Brave and Safari) have put time and money in limiting user data access or separating data. So they are trying to change the standards to what they already have developed (or adopt it a little so they still have an advantage over other browsers).
To be honest, I am not using an anti-fingerprinting or blurring solution, because I yet have to find a good functioning extension or the solution chargex to much for what my privacy is worth (e.g. browser bubble) or is a to heavy hit on my internet speed (Tor browser plus VPN)
Last edited by a moderator:
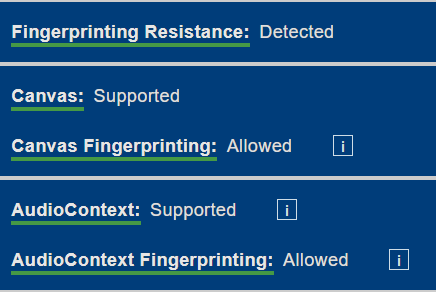
Audio + Canvas protection:
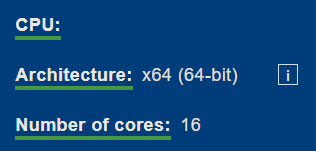
CPU detection:
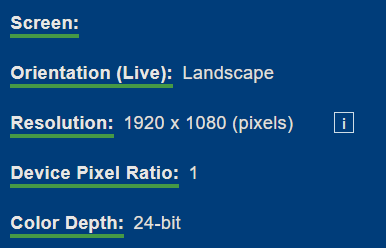
Resolution detection:
Battery detection:
Accounts detection:
CPU detection:
Resolution detection:
Battery detection:
Accounts detection:
Audio + Canvas protection:
CPU detection:
Resolution detection:
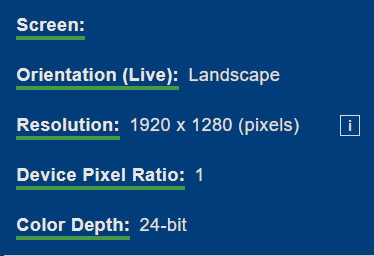
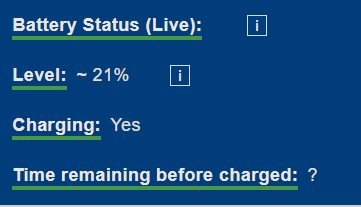
Battery detection: (Quite useless as the battery API isn't used anymore by Firefox at least)
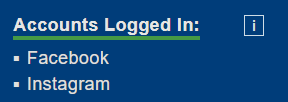
Accounts detection: (Don't know why but with Trace enabled it shows me 2 logged in accounts)
CPU detection:
Resolution detection:
Battery detection: (Quite useless as the battery API isn't used anymore by Firefox at least)
Accounts detection: (Don't know why but with Trace enabled it shows me 2 logged in accounts)
Website: Device Info - Web browser security, privacy, and troubleshooting tool.
I tested on browserleaks.org and it is giving me all of my true user agent data and a unique fingerprint lol. It doesn't seem to do anything on my end.
I have to correct myself (it's not about consistency):It won't simply hide or change your userAgent because it may introduce inconsistency of the fingerprint and make it more unique.
"User agent wasn't modified because it can cause compatibility issues as we support multiple browsers. We will continue to watch changes in the user agent and may implement some defence in future, although it looks like a better solution is on the way."
The discussion in this thread shows that there is no agreement about the best way of spoofing fingerprint elements (and perhaps there isn't such way at all). Apart from this, I don't like spoofing because ordinary tracker blockers do a better job. Nevertheless, JavaScript Restrictor has an interesting new mechanism: FingerPrint Detector (FPD). Quote from the site JShelter::
FPD does not attempt to prevent a script from taking a fingerprint. Neither does FPD falsify a fingerprint. Instead, FPD monitors the APIs that a web page accesses and detects suspicious activities. FPD quickly reacts in case of fingerprint extraction and blocks further web page communication, including storing information.
When you choose for configuration level 0 ('Turn wrappers off'), JavaScript Restrictor will only intervene on fingerprinting sites.
The developer also states:
Finally, note that blocking tools like adblockers can significantly reduce the number of positive detections. These tools use filter lists to block tracking scripts before their execution. Using FPD with a filter-based blocking tool can significantly improve user experience and privacy.
What do you guys and girls think about it?
FPD does not attempt to prevent a script from taking a fingerprint. Neither does FPD falsify a fingerprint. Instead, FPD monitors the APIs that a web page accesses and detects suspicious activities. FPD quickly reacts in case of fingerprint extraction and blocks further web page communication, including storing information.
When you choose for configuration level 0 ('Turn wrappers off'), JavaScript Restrictor will only intervene on fingerprinting sites.
The developer also states:
Finally, note that blocking tools like adblockers can significantly reduce the number of positive detections. These tools use filter lists to block tracking scripts before their execution. Using FPD with a filter-based blocking tool can significantly improve user experience and privacy.
What do you guys and girls think about it?
Last edited:
It's a cat and mouse game. Not worth the effort or possible breakage. Built-in protection is best, at least for me.What do you guys and girls think about it?
F
ForgottenSeer 92963
@


As I have posted earlier Google has proposed a similar mechanism, where websites get some 'fingerprinting' credit and when a website exceeds its credits (meaning it gathers more profiling info than needed), the browser would block all futher fingerprinting requests.
So I like this new view on how to tackle fingerprinting for three reasons:
1. It evades the problem of balancing blurring and blocking (with many overlapping mechanism to extract data points to profile), this heuristic approach which makes it a lot simpler
2. The proposed heuristics mechanism seems related to the one proposed by Google (always reassuring when a big player and contributor to W3C standards shares your opinion)
3. Heuristics based blocking has been a proven and successful approach in the past (remember PrivacyPossum) for a privacy enhancing extension
You can argue that Google is coming with a similar solution in the future, but
a) It is Google, what level of fingerprinting does the largest advertising platform finds acceptable (similar to 'acceptable' ads, to whose standard are these acceptable)?
b) JShelter offers it now, so why wait when it is already available now
Edge's new automatic profile switching becomes real handy with this new JShelter heuristics block mode. In your (default for all websites) Strict mode profile you can install JShelter and for bookmarked websites you can switch to the more relaxed profile without JShelter. I agree with @oldschool the current implementation is a bit rough on the edges and the protection might not be worth the extra hassle. All in all it is just version 0.6 and to their credits they seem to have taken a more promising counter strategy
Thanks for the info: I stopped following the development of this extension because of the disappointing discussion I had with them. Now it seems that they agree that blurring and blocking has to be done right (or else it makes you easier to track). So they did some research and sort of changed their finger printing counter strategyThe discussion in this thread shows that there is no agreement about the best way of spoofing fingerprint elements (and perhaps there isn't such way at all). Apart from this, I don't like spoofing because ordinary tracker blockers do a better job. Nevertheless, JavaScript Restrictor has an interesting new mechanism: FingerPrint Detector (FPD).
What do you guys and girls think about it?
As I have posted earlier Google has proposed a similar mechanism, where websites get some 'fingerprinting' credit and when a website exceeds its credits (meaning it gathers more profiling info than needed), the browser would block all futher fingerprinting requests.
So I like this new view on how to tackle fingerprinting for three reasons:
1. It evades the problem of balancing blurring and blocking (with many overlapping mechanism to extract data points to profile), this heuristic approach which makes it a lot simpler
2. The proposed heuristics mechanism seems related to the one proposed by Google (always reassuring when a big player and contributor to W3C standards shares your opinion)
3. Heuristics based blocking has been a proven and successful approach in the past (remember PrivacyPossum) for a privacy enhancing extension
You can argue that Google is coming with a similar solution in the future, but
a) It is Google, what level of fingerprinting does the largest advertising platform finds acceptable (similar to 'acceptable' ads, to whose standard are these acceptable)?
b) JShelter offers it now, so why wait when it is already available now
Edge's new automatic profile switching becomes real handy with this new JShelter heuristics block mode. In your (default for all websites) Strict mode profile you can install JShelter and for bookmarked websites you can switch to the more relaxed profile without JShelter. I agree with @oldschool the current implementation is a bit rough on the edges and the protection might not be worth the extra hassle. All in all it is just version 0.6 and to their credits they seem to have taken a more promising counter strategy
Last edited by a moderator:
New version 0.7 released with a new UI (still potential for improvement) and easier understandable descriptions for each setting.
1.
2.
3.

Even tho there were quite a few different opinions about the best way of protecting yourself from fingerprinting it would be much appreaciated if @Sunkar could give us any other updates worth mentioning.
1.

2.

3.

Even tho there were quite a few different opinions about the best way of protecting yourself from fingerprinting it would be much appreaciated if @Sunkar could give us any other updates worth mentioning.
Last edited:
F
ForgottenSeer 92963
@SecureKongo They adopted their approach  I am using this extension in my STRICT browser profile (not in my EASY profile)
I am using this extension in my STRICT browser profile (not in my EASY profile)
So it's worth using now in your opinion?@SecureKongo They adopted their approachI am using this extension in my STRICT browser profile (not in my EASY profile)
F
ForgottenSeer 92963
@SecureKongo Yes, but as posted, I use it only in my Strict Edge profile (with fingerprinting protection enabled) which I use for surfing (I use my Easy profile for booking, banking & buying).
You may also like...
-
New Update JShelter Debuts as a Manifest V3 Extension
- Started by oldschool
- Replies: 1
-
Malware News DarkSpectre Browser Extension Campaigns Exposed After Impacting 8.8 Million Users Worldwide
- Started by Gandalf_The_Grey
- Replies: 2
-
New Update Windscribe added "Anti-Fingerprinting" to their VPN extension
- Started by rashmi
- Replies: 3
-
-
Serious Discussion Browser Wars 2025: Which Browser Really Keeps You Safe?
- Started by Bot
- Replies: 17