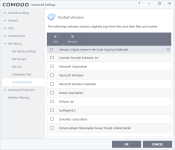
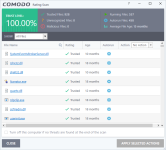
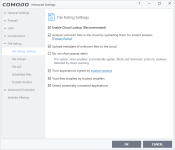
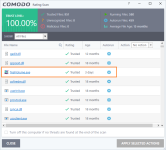
Comodo firewall is set to Cruelsister settings.
I think that this malware is bypased that settings (maybe I'm wrong).
What do you think?
Video summary:
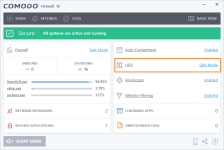
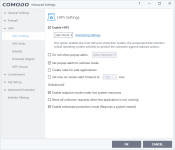
1. check Comodo firewall settings
2. delete all trusted vendors
3. add some malware to see if Comodo is working OK
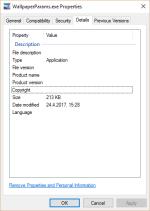
4. check that one malware at VT
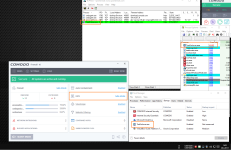
5. run malware and watch:
- C:\Users\Av-Gurus\AppData\Local
- Task manager startup
- network connection
I think that this malware is bypased that settings (maybe I'm wrong).
What do you think?
Video summary:
1. check Comodo firewall settings
2. delete all trusted vendors
3. add some malware to see if Comodo is working OK
4. check that one malware at VT
5. run malware and watch:
- C:\Users\Av-Gurus\AppData\Local
- Task manager startup
- network connection
Last edited: