Some more info on the payload...
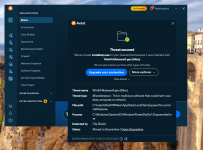
Sending request to SiriusLLM Model 0...
Model 0 confidence (85% Malicious) is below the 90% confidence threshold.
Sending request to Model 1...
Selected result: Malicious with 92% confidence from Model 1.
Total tokens: 3707 (3030 request / 677 response)
File path: C:\Users\User\Desktop\Instalihaly.exe
File hash: 19a331e787c3f5c3ba9c565f4e265a69f0804f92255abceccc670343e0ffdb2a
File size: 0.09 MB
File publisher: This file is a signable file type but has not been digitally signed.
WhitelistCloud verdict: Not Safe
Final Verdict: Not Safe with 92% confidence.
Analysis Summary
The file Instalihaly.exe (93 KB, 2025-11-07) is a 64-bit native console executable – not .NET – that imports only a handful of Win32 functions.
Despite the minimal import table, the presence of Internet-open/download primitives, resource-only code execution via VirtualProtect/ShellExecute, and multiple indicators (missing ASLR/DEP, no signature, resource-heavy, TLS table) point to a small packed or self-decrypting loader rather than a legitimate installer/helper.
Coupled with a high-confidence WhitelistCloud “Malicious” flag, we assess this artifact as malicious.
Detailed Analysis
• Import footprint: 12 functions, including InternetOpenA, ShellExecuteA, VirtualProtect, BitBlt, GdiplusStartup.
– InternetOpenA together with no documented updater/installer brand is a red flag for silent download-and-run behavior.
– VirtualProtect is commonly abused to make on-the-fly code sections writable/executable (typical for shell-code injection or run-time unpacking).
– GdiplusStartup/BitBlt suggest possible screenshot capability or simple steganography, not normally present in clean installers this small.
• Security mitigations disabled: ASLR = 0, DEP = 0, DllCharacteristics = 0x0.
Legitimate Windows software almost always opts-in to these protections; their deliberate absence is a classic malware evasion trick.
• Resources: ~67 KB (≈72 % of file) and a TLS callback table imply encrypted/packed payload stored in .rsrc and decrypted at thread-start.
• No digital signature; FileDescription et al. absent. WhitelistCloud marks it “Malicious”.
• Exports: none – acceptable for a dropper/loader whose only job is to deploy additional code.
Strings review (top meaningful)
/botY/sendMessageA37 – Telegram bot API fragment used for C2 or data exfil.
TelegramB – corroborates Telegram abuse for command & control.
USERNAME, COMPUTA: – likely part of victim-fingerprinting routine.
DOWNLOAD/oFILEDOWN – indicates download-to-execute logic.
SUCCESS – simple status keyword echoed back to C2.
Standard system DLL names already listed in imports; no embedded paths/URLs that would suggest a reputable publisher.
Likely purpose
A compact first-stage loader/downloader that beacons to a Telegram bot, downloads the next-stage payload, and executes it while taking a desktop snapshot for proof-of-infection. The executable masquerades as an “installer” (filename) but exhibits none of the metadata, signing, or protective features expected of legitimate setup programs.
Malware type: Downloader
Malware name: TgLoader.A
Final verdict: Malicious with 92% confidence.