A quick update:
We've officially released NoVirusThanks OSArmor v1.6.2:
Download OSArmor for Windows 7, 8, 10 (32 & 64-bit) | OSArmor
Changelog 14 Nov 2021:
The new protection option "Block installation of Windows Apps via AppInstaller" can be used to mitigate this:

 news.sophos.com
news.sophos.com
Here is a screenshot of when "ms-appinstaller:" HREF link is clicked:
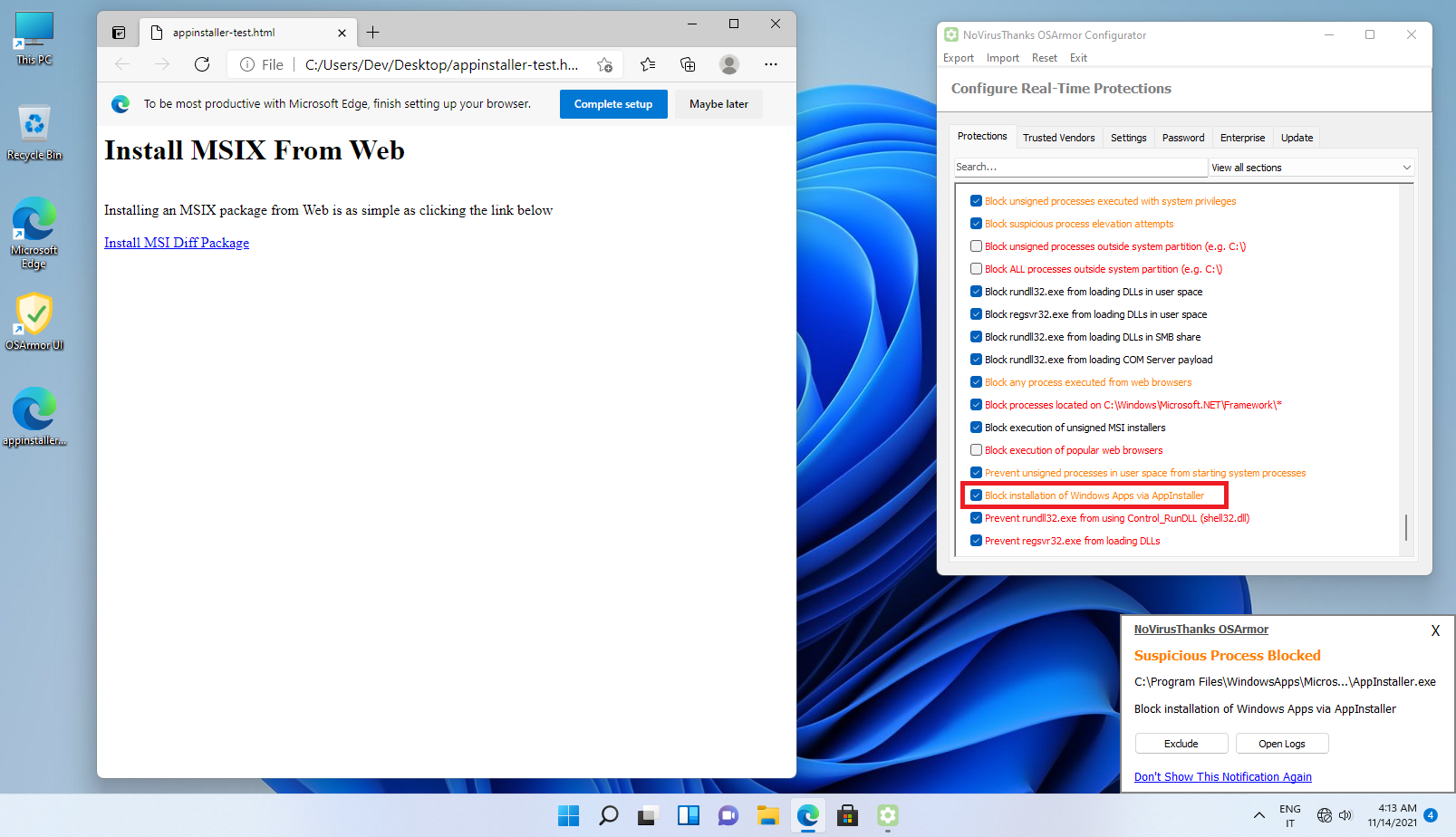
The targets of the attack are (for now) companies, so home users may not need to enable that option.
If you find FPs or issues please let me know.
Thanks guys!
We've officially released NoVirusThanks OSArmor v1.6.2:
Download OSArmor for Windows 7, 8, 10 (32 & 64-bit) | OSArmor
Changelog 14 Nov 2021:
+ Added Block installation of Windows Apps via AppInstaller
+ Fixed UTF-8 encoding when loading TrustedVendors.db
+ Fixed UTF-8 encoding on Exclusions Helper
+ Improved detection of some known bad behaviors
+ Fixed all reported false positives
+ Minor improvements
The new protection option "Block installation of Windows Apps via AppInstaller" can be used to mitigate this:

BazarLoader ‘call me back’ attack abuses Windows 10 Apps mechanism
The unusual technique invokes the Windows App Installer to deliver malware
Here is a screenshot of when "ms-appinstaller:" HREF link is clicked:
The targets of the attack are (for now) companies, so home users may not need to enable that option.
If you find FPs or issues please let me know.
Thanks guys!